Authorities entities and large corporations have been targeted by an unknown danger actor by exploiting a security flaw in Fortinet FortiOS computer software to final result in information decline and OS and file corruption.
“The complexity of the exploit indicates an advanced actor and that it is remarkably specific at governmental or authorities-relevant targets,” Fortinet researchers Guillaume Lovet and Alex Kong claimed in an advisory final week.
The zero-working day flaw in question is CVE-2022-41328 (CVSS rating: 6.5), a medium security path traversal bug in FortiOS that could lead to arbitrary code execution.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“An inappropriate limitation of a pathname to a restricted listing vulnerability (‘path traversal’) [CWE-22] in FortiOS may permit a privileged attacker to read through and produce arbitrary files by way of crafted CLI instructions,” the organization mentioned.
The shortcoming impacts FortiOS variations 6., 6.2, 6.4. by way of 6.4.11, 7.. through 7..9, and 7.2. by 7.2.3. Fixes are obtainable in variations 6.4.12, 7..10, and 7.2.4 respectively.
The disclosure will come times right after Fortinet produced patches to address 15 security flaws, which includes CVE-2022-41328 and a critical heap-based buffer underflow issue impacting FortiOS and FortiProxy (CVE-2023-25610, CVSS rating: 9.3).
According to the Sunnyvale-dependent business, various FortiGate products belonging to an unnamed purchaser experienced from a “sudden method halt and subsequent boot failure,” indicating an integrity breach.
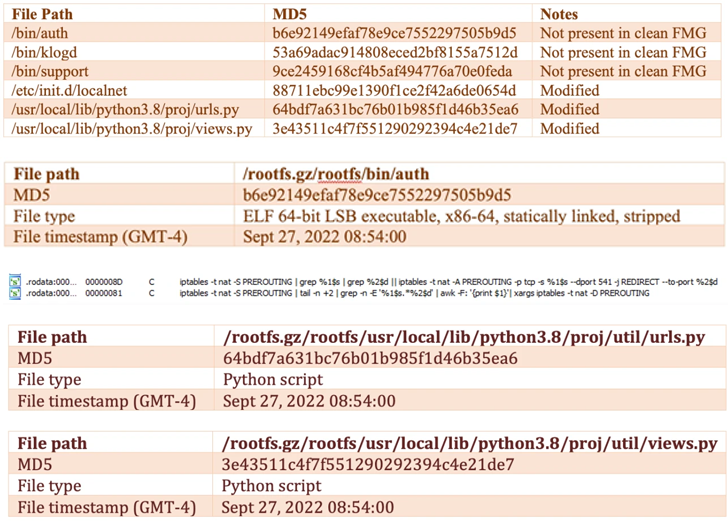
Further more evaluation of the incident disclosed that the risk actors modified the device’s firmware image to include a new payload (“/bin/fgfm”) this kind of that it is really usually released in advance of the booting procedure started.
The /bin/fgfm malware is made to build make contact with with a distant server to download information, exfiltrate facts from the compromised host, and grant distant shell entry.
Added changes introduced to the firmware are reported to have provided the attacker with persistent entry and handle, not to point out even disable firmware verification at startup.
WEBINARDiscover the Hidden Hazards of Third-Party SaaS Apps
Are you informed of the pitfalls associated with third-party app obtain to your company’s SaaS apps? Join our webinar to learn about the sorts of permissions remaining granted and how to decrease risk.
RESERVE YOUR SEAT
Fortinet stated the attack was really focused, with proof pointing to governmental or federal government-affiliated companies.
Given the complexity of the exploit, it is suspected that the attacker has a “deep comprehending of FortiOS and the underlying components” and possesses sophisticated abilities to reverse engineer diverse areas of the FortiOS working process.
It truly is not instantly apparent if the menace actor has any connections to yet another intrusion set that was noticed weaponizing a flaw in FortiOS SSL-VPN (CVE-2022-42475) previously this January to deploy a Linux implant.
Uncovered this post interesting? Abide by us on Twitter and LinkedIn to read through far more exclusive articles we publish.
Some sections of this short article are sourced from:
thehackernews.com


 Remote Code Execution and Camera Access Flaws Found in Smart Intercoms
Remote Code Execution and Camera Access Flaws Found in Smart Intercoms