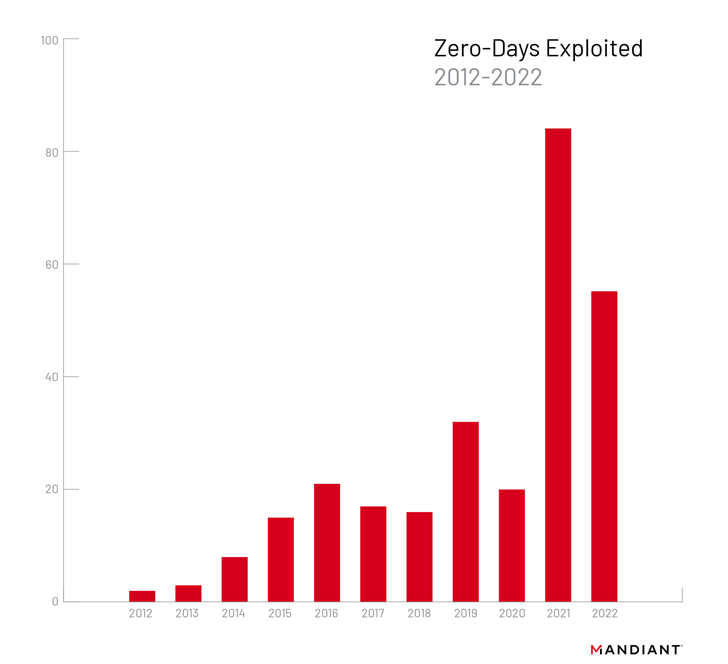
As several as 55 zero-day vulnerabilities ended up exploited in the wild in 2022, with most of the flaws found in software package from Microsoft, Google, and Apple.
Though this determine represents a lessen from the 12 months in advance of, when a staggering 81 zero-times have been weaponized, it nevertheless signifies a substantial uptick in new several years of risk actors leveraging unidentified security flaws to their benefit.
The findings arrive from menace intelligence firm Mandiant, which famous that desktop working systems (19), web browsers (11), IT and network management items (10), and cellular running units (six) accounted for the most exploited solution forms.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
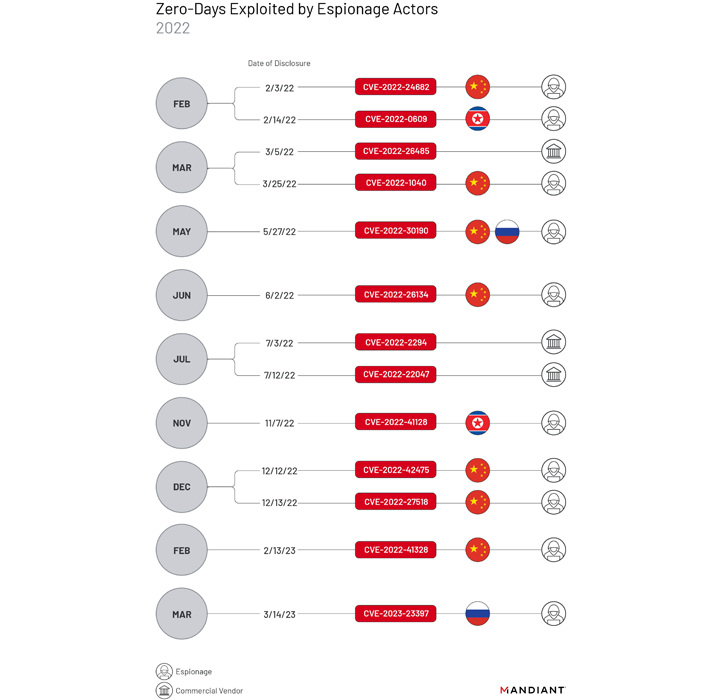
Of the 55 zero-day bugs, 13 are estimated to have been abused by cyber espionage teams, with four many others exploited by monetarily inspired danger actors for ransomware-relevant operations. Commercial adware vendors were being connected to the exploitation of three zero-times.
Among the condition-sponsored groups, all those attributed to China have emerged as the most prolific, exploiting seven zero-times – CVE-2022-24682, CVE-2022-1040, CVE-2022-30190, CVE-2022-26134, CVE-2022-42475, CVE-2022-27518, and CVE-2022-41328 – throughout the calendar year.
A great deal of the exploitation has concentrated on vulnerabilities in edge network gadgets these kinds of as firewalls for getting original accessibility. Various China-nexus clusters have also been noticed leveraging a flaw in Microsoft Diagnostics Instrument (aka Follina) as element of disparate strategies.
“A number of individual campaigns could reveal that the zero-day was dispersed to a number of suspected Chinese espionage clusters through a electronic quartermaster,” Mandiant reported, adding it factors to the “existence of a shared advancement and logistics infrastructure and potentially a centralized coordinating entity.”
North Korean and Russian menace actors, on the other hand, have been connected to the exploitation of two zero-times every single. This features CVE-2022-0609, CVE-2022-41128, CVE-2022-30190, and CVE-2023-23397.
The disclosure will come as risk actors are also getting greater at turning freshly disclosed vulnerabilities into highly effective exploits for breaching a wide range of targets across the environment.
“When the discovery of zero-working day vulnerabilities is a useful resource-intensive endeavor and profitable exploitation is not confirmed, the full quantity of vulnerabilities disclosed and exploited has continued to increase, the varieties of specific software, including Internet of Issues (IoT) equipment and cloud answers, continue on to evolve, and the variety of actors exploiting them has expanded,” Mandiant said.
WEBINARDiscover the Concealed Dangers of 3rd-Party SaaS Applications
Are you knowledgeable of the risks affiliated with 3rd-party application entry to your company’s SaaS apps? Sign up for our webinar to learn about the sorts of permissions becoming granted and how to lower risk.
RESERVE YOUR SEAT
The Mandiant report also follows a warning from Microsoft’s Digital Risk Evaluation Center about Russia’s persistent kinetic and cyber concentrating on as the war in Ukraine proceeds into the 2nd year.
The tech big stated since January 2023 it has observed “Russian cyber menace exercise changing to enhance harmful and intelligence gathering capacity on Ukraine and its partners’ civilian and armed service belongings.”
It additional warned of a possible “renewed destructive marketing campaign” mounted by the nation-state group recognized as Sandworm (aka Iridium) on organizations positioned in Ukraine and somewhere else.
What is actually far more, Moscow-backed hackers have deployed at the very least two ransomware and nine wiper families towards about 100 Ukrainian entities. No significantly less than 17 European international locations have been focused in espionage strategies concerning January and mid-February 2023, and 74 international locations have been specific considering that the commence of the war.
Other essential traits related with Russian danger action include things like the use of ransomware as weapons of cyber sabotage, gaining initial accessibility through various procedures, and leveraging genuine and pseudo hacktivist teams to expand the reach of Moscow’s cyber presence.
Observed this post fascinating? Observe us on Twitter and LinkedIn to read through additional special articles we put up.
Some components of this article are sourced from:
thehackernews.com


 Ferrari Reveals Data Breach Ransom Attack
Ferrari Reveals Data Breach Ransom Attack