Cybersecurity researchers have found out a new cryptojacking marketing campaign that employs susceptible drivers to disable known security options (EDRs) and thwart detection in what is actually named a Bring Your Very own Vulnerable Driver (BYOVD) attack.
Elastic Security Labs is tracking the campaign beneath the identify REF4578 and the primary payload as GHOSTENGINE. Preceding investigate from Chinese cybersecurity business Antiy Labs has codenamed the exercise as Concealed SHOVEL.
“GHOSTENGINE leverages vulnerable motorists to terminate and delete regarded EDR brokers that would likely interfere with the deployed and perfectly-known coin miner,” Elastic scientists Salim Bitam, Samir Bousseaden, Terrance DeJesus, and Andrew Pease reported.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This campaign included an uncommon quantity of complexity to guarantee both of those the set up and persistence of the XMRig miner.”
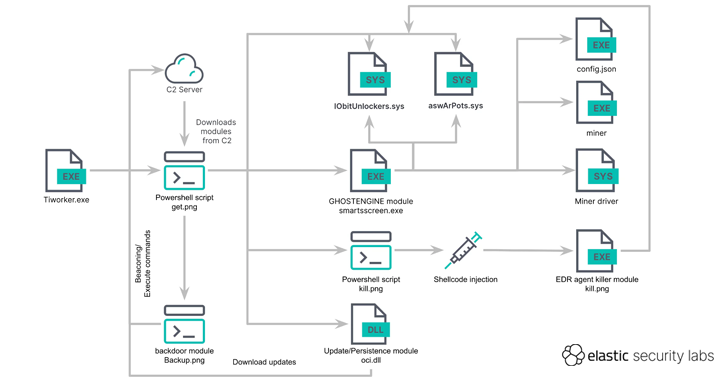
It all begins with an executable file (“Tiworker.exe”), which is utilized to operate a PowerShell script that retrieves an obfuscated PowerShell script that masquerades as a PNG graphic (“get.png”) to fetch extra payloads from a command-and-command (C2) server.
These modules — aswArPot.sys, IObitUnlockers.sys, curl.exe, smartsscreen.exe, oci.dll, backup.png, and kill.png — are released on the contaminated host just after downloading them more than HTTP from possibly the configured C2 server or a backup server in situation the domains are unavailable. It also incorporates an FTP-based mostly fallback system.
In addition, the malware makes an attempt to disable Microsoft Defender Antivirus, apparent many Windows occasion log channels, and make certain that the C: volume has at least 10 MB of absolutely free room to down load information, which are then stashed in the C:WindowsFonts folder.
“If not, it will check out to delete huge documents from the process prior to hunting for a further acceptable quantity with sufficient house and developing a folder less than $RECYCLE.BINFonts,” the researchers stated.
The PowerShell script is also designed to develop three scheduled duties on the program to run a malicious DLL every single 20 minutes, launch by itself by suggests of a batch script each and every hour, and execute smartsscreen.exe every 40 minutes.

The main payload of the attack chain is smartsscreen.exe (aka GHOSTENGINE), whose main purpose is to deactivate security procedures using the vulnerable Avast driver (“aswArPot.sys”), entire first an infection, and execute the miner.
The security agent binary is then deleted by usually means of a different susceptible driver from IObit (“iobitunlockers.sys”), pursuing which the XMRig customer mining system is downloaded from the C2 server and executed.
The DLL file is used to ensure the persistence of the malware and down load updates from the C2 servers by fetching the get.png script and executing it, even though the “backup.png” Powershell script features as a backdoor to permit remote command execution on the method.
In what has been interpreted as a redundancy measure, the PowerShell script “get rid of.png” has comparable abilities as smartsscreen.exe to delete security agent binaries by injecting and loading an executable file into memory.
The development arrives as the Uptycs Menace Study Workforce found a substantial-scale, ongoing operation considering the fact that January 2024 that exploits recognized flaws in the Log4j logging utility (e.g., CVE-2021-44228) to produce an XMRig miner on to the targeted hosts.

“Subsequent to compromising a sufferer device, it initiated speak to with a URL to fetch a shell script for the deployment of the XMRig miner, or alternatively, in find circumstances, it disseminated Mirai or Gafgyt malware,” security researcher Shilpesh Trivedi mentioned.
A bulk of the impacted servers are found in China, adopted by Hong Kong, Netherlands, Japan, the U.S., Germany, South Africa, and Sweden.
BYOVD and Other Procedures to Undermine Security Mechanisms
BYOVD is an ever more preferred procedure wherein a menace actor delivers a acknowledged-vulnerable signed driver, masses it into the kernel, and exploits it to conduct privileged actions, normally with an intention to disarm security procedures and allow them to function stealthily.
“Drivers operate at ring , the most privileged level of the functioning system,” Israeli cybersecurity firm Cymulate notes. “This grants them direct entry to critical memory, CPU, I/O operations, and other elementary methods. In the case of BYOVD, the attack is intended to load a vulnerable driver to further more the attack.”
While Microsoft has deployed the Vulnerable Driver Blocklist by default beginning in Windows 11 22H2, the checklist is only up-to-date only after or twice a yr, necessitating that consumers manually update it periodically for exceptional protection.
The precise scope of the marketing campaign remains unknown and it truly is presently not distinct who is driving it. On the other hand, the abnormal sophistication powering what appears to be a easy illicit cryptocurrency mining attack bears detect.

The disclosure also follows the discovery of a novel approach referred to as EDRaser that normally takes benefit of flaws in Microsoft Defender (CVE-2023-24860 and CVE-2023-36010) to remotely delete accessibility logs, Windows occasion logs, databases, and other data files.
The issue, which also impacts Kaspersky, stems from the fact that both equally the security packages use byte signatures to detect malware, thus allowing a risk actor to implant malware signatures into legit documents and fool the applications into contemplating that they are malicious, SafeBreach stated.
The cybersecurity corporation has independently uncovered a resourceful exploit to get around security protections available by Palo Alto Networks Cortex XDR and weaponize it to deploy a reverse shell and ransomware, efficiently repurposing it into a rogue offensive device.

At its main, the bypass would make it probable to load a vulnerable driver (“rtcore64.sys”) by using a BYOVD attack and tamper with the solution to protect against a respectable administrator from removing the software package and finally insert malicious code into a single of its processes, granting the risk actor high privileges although remaining undetected and persistent.
“The logic guiding the detection processes of a security products ought to be carefully guarded,” security researcher Shmuel Cohen mentioned past month. “By offering attackers obtain to this delicate detection logic by way of the solution’s articles files, they are a great deal much more very likely to be equipped to engineer a way all over it.”
An additional novel system is HookChain, which, as Brazilian security researcher Helvio Carvalho Junior, requires combining IAT hooking, dynamic program service quantities (SSN) resolution, and indirect system phone calls to escape monitoring and control mechanisms applied by security software program in the consumer mode, specially in the NTDLL.dll library.
“HookChain is able of redirecting the execution move of all main Windows subsystems, these types of as kernel32.dll, kernelbase.dll, and user32.dll,” Carvalho Junior explained in a newly revealed paper.
“This usually means that, after deployed, HookChain ensures that all API phone calls within the context of an application are carried out transparently, wholly avoiding detection by [Endpoint detection and response software].”
Observed this posting intriguing? Observe us on Twitter and LinkedIn to read through more unique written content we write-up.
Some areas of this write-up are sourced from:
thehackernews.com

 MS Exchange Server Flaws Exploited to Deploy Keylogger in Targeted Attacks
MS Exchange Server Flaws Exploited to Deploy Keylogger in Targeted Attacks