The notorious ransomware team acknowledged as Conti has continued its onslaught towards entities inspite of struggling a significant info leak of its possess earlier this year, in accordance to new research.
Conti, attributed to a Russia-based mostly menace actor recognised as Gold Ulrick, is one of the most widespread malware strains in the ransomware landscape, accounting for 19% of all attacks during the 3-month-period concerning Oct and December 2021.
A person of the most prolific ransomware teams of the last 12 months along the likes of LockBit 2., PYSA, and Hive, Conti has locked the networks of hospitals, organizations, and government organizations, though obtaining a ransom payment in exchange for sharing the decryption crucial as element of its identify-and-shame scheme.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
But following the cybercriminal cartel came out in assist of Russia more than its invasion of Ukraine in February, an nameless Ukrainian security researcher below the Twitter take care of ContiLeaks began leaking the source code as well as private discussions involving its customers, giving an unparalleled perception into the group’s workings.

“The chats expose a mature cybercrime ecosystem across multiple threat teams with repeated collaboration and aid,” Secureworks claimed in a report revealed in March. The groups include Gold Blackburn (TrickBot and Diavol), Gold Crestwood (Emotet), Gold Mystic (LockBit), and Gold Swathmore (IcedID).
In fact, Intel 471’s technological checking of Emotet campaigns among December 25, 2021, and March 25, 2022, recognized that about a dozen Conti ransomware targets have been, in truth, victims of Emotet malspam attacks, highlighting how the two operations are intertwined.
That stated, the leaks you should not appear to be to have set a dampener on the syndicate’s pursuits, with the quantity of Conti victims posted in March surged to the 2nd-best regular monthly complete considering that January 2021, in accordance to the cybersecurity firm.
What is actually extra, the group is stated to have extra 11 victims in the initially four times of April, even as the operators go on to “evolve its ransomware, intrusion techniques, and strategies” in reaction to the public disclosure of their arsenal.
The results have also been corroborated by NCC Team late past thirty day period, which said that “Conti operators proceed their small business as normal by proceeding to compromise networks, exfiltrating data and ultimately deploying their ransomware.”
A web of connections involving Conti and Karakurt
The enhancement comes as fiscal and tactical overlaps have been uncovered involving Conti and the Karakurt details extortion team primarily based on facts published in the course of the ContiLeaks saga, weeks after TrickBot’s operators experienced been subsumed into the ransomware cartel.

An evaluation of blockchain transactions associated with cryptocurrency addresses belonging to Karakurt has revealed “Karakurt wallets sending significant sums of cryptocurrency to Conti wallets,” in accordance to a joint investigation by researchers from Arctic Wolf and Chainalysis.
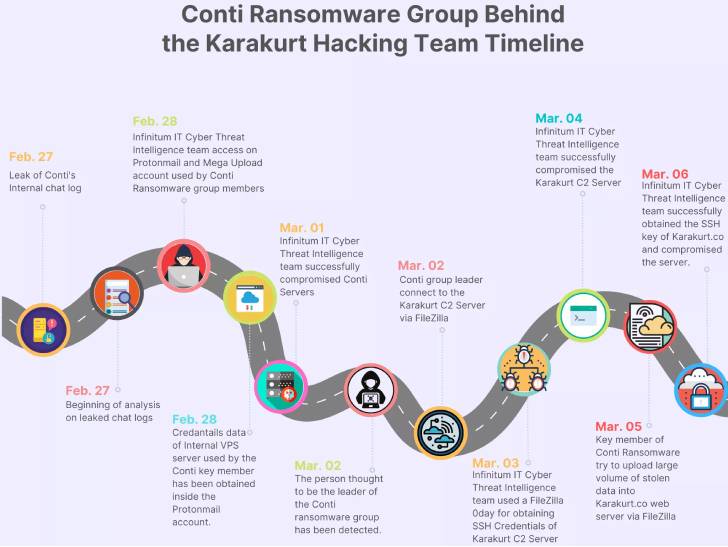
The shared wallet hosting is also claimed to involve the now-defunct TrickBot gang’s Diavol ransomware, with a “Diavol extortion handle hosted by a wallet that contains addresses utilised in Conti ransomware attacks,” indicating that Diavol is getting deployed by the exact established of actors powering Conti and Karakurt.
More forensic evaluation of an unnamed consumer that was hit with a subsequent wave of extortion attacks adhering to a Conti ransomware an infection has exposed that the 2nd group used the exact Cobalt Strike backdoor remaining powering by Conti, implying a solid association between seemingly disparate cybercrime actors.
“Whether Karakurt is an elaborate side hustle by Conti and Diavol operatives or regardless of whether this is an company sanctioned by the total business continues to be to be observed,” Arctic Wolf mentioned.
“This link probably clarifies why Karakurt is surviving and thriving regardless of some of its exfiltration-only opponents dying out,” the researchers claimed, introducing, “Or, alternatively, maybe this was the demo operate of a strategic diversification approved by the major group.”
Uncovered this report exciting? Adhere to THN on Facebook, Twitter and LinkedIn to study a lot more exclusive articles we write-up.
Some components of this short article are sourced from:
thehackernews.com


 AWS launches quantum random number generator
AWS launches quantum random number generator