If you have not not too long ago up-to-date your Chrome, Opera, or Edge web browser to the hottest out there version, it would be an fantastic idea to do so as quickly as achievable.
Cybersecurity researchers on Monday disclosed information about a zero-working day flaw in Chromium-based web browsers for Windows, Mac and Android that could have authorized attackers to entirely bypass Material Security Policy (CSP) rules because Chrome 73.
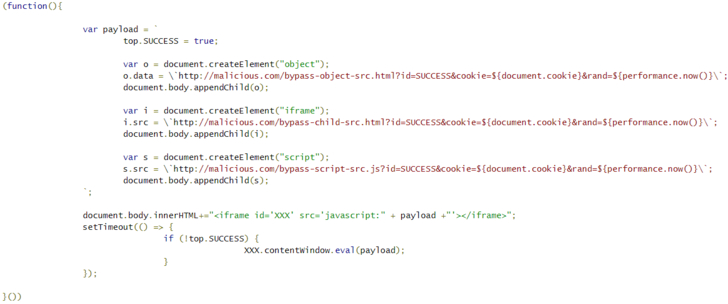
Tracked as CVE-2020-6519 (rated 6.5 on the CVSS scale), the issue stems from a CSP bypass that effects in arbitrary execution of malicious code on goal internet sites.
According to PerimeterX, some of the most well-known websites, like Fb, Wells Fargo, Zoom, Gmail, WhatsApp, Investopedia, ESPN, Roblox, Without a doubt, TikTok, Instagram, Blogger, and Quora, were susceptible to the CSP bypass.
Interestingly, it seems that the very same flaw was also highlighted by Tencent Security Xuanwu Lab much more than a yr ago, just a thirty day period just after the release of Chrome 73 in March 2019, but was by no means resolved right up until PerimeterX claimed the issue before this March.
Soon after the conclusions were disclosed to Google, the Chrome staff issued a deal with for the vulnerability in Chrome 84 update (edition 84..4147.89) that began rolling out on July 14 final month.
CSP is an extra layer of security that can help detect and mitigate selected styles of attacks, which includes Cross-Internet site Scripting (XSS) and data injection assaults. With CSP rules, a site can mandate the victim’s browser to accomplish particular consumer-side checks with an aim to block specific scripts that are created to exploit the browser’s have faith in of the content material been given from the server.
Provided that CSP is the major process made use of by web page house owners to enforce details security policies and reduce the execution of malicious scripts, a CSP bypass can proficiently set user info at danger.
This is attained by specifying the domains that the browser should really take into consideration to be valid resources of executable scripts, so that a CSP-compatible browser only executes scripts loaded in source documents obtained from people let-shown domains, ignoring all some others.
The flaw identified by Tencent and PerimeterX circumvents the configured CSP for a web-site by merely passing a destructive JavaScript code in the “src” property of an HTML iframe factor.
It’s worthy of noting that web-sites like Twitter, Github, LinkedIn, Google Play Store, Yahoo’s Login Web site, PayPal, and Yandex had been not identified susceptible considering the fact that the CSP guidelines were carried out utilizing a nonce or hash to let the execution of inline scripts.
“Owning a vulnerability in Chrome’s CSP enforcement mechanism isn’t going to immediately signify that websites are breached, as the attackers also need to deal with to get the destructive script named from the internet site (which is why the vulnerability was categorized as medium severity),” PerimeterX’s Gal Weizman observed.
Although the implications of the vulnerability continue to be unfamiliar, people will have to update their browsers to the latest model to shield towards this sort of code execution. Website proprietors, for their element, are advised to use nonce and hash capabilities of CSP for additional security.
Moreover this, the most current Chrome update 84..4147.125 for Windows, Mac, and Linux methods also patches 15 other security vulnerabilities, 12 of which are rated ‘high’ and two ‘low’ in severity.
Discovered this post exciting? Stick to THN on Fb, Twitter and LinkedIn to read far more unique written content we article.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount


 Company need to prevail over privacy obstacle for facial recognition to thrive
Company need to prevail over privacy obstacle for facial recognition to thrive