Google on Thursday introduced that it can be in search of contributors to a new open up source initiative referred to as Graph for Comprehending Artifact Composition, also recognized as GUAC, as component of its ongoing endeavours to beef up the software provide chain.
“GUAC addresses a have to have made by the burgeoning endeavours throughout the ecosystem to create application make, security, and dependency metadata,” Brandon Lum, Mihai Maruseac, and Isaac Hepworth of Google explained in a write-up shared with The Hacker News.
“GUAC is intended to democratize the availability of this security details by creating it freely available and useful for every group, not just people with business-scale security and IT funding.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Software program source chain has emerged a rewarding attack vector for menace actors, wherein exploiting just one particular weakness — as seen in the circumstance of SolarWinds and Log4Shell — opens a pathway extended enough to traverse down the supply chain and steal delicate facts, plant malware, and consider command of units belonging to downstream buyers.

Google, final 12 months, unveiled a framework known as SLSA (quick for Offer chain Levels for Software program Artifacts) that aims to ensure the integrity of software program offers and stop unauthorized modifications.
It has also released an up to date edition of Security Scorecards, which identifies the risk third-party dependencies can introduce to a job, permitting developers to make informed selections about accepting susceptible code or taking into consideration other alternatives.
This previous August, Google further launched a bug bounty system to discover security vulnerabilities spanning a number of initiatives these kinds of as Angular, Bazel, Golang, Protocol Buffers, and Fuchsia.
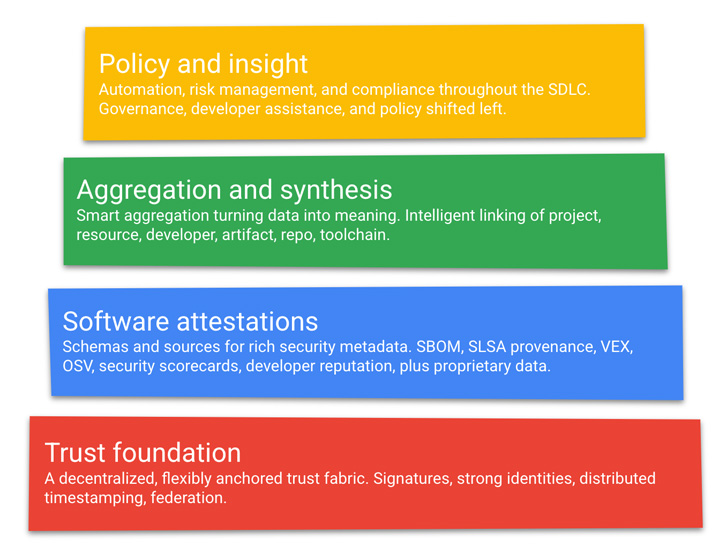
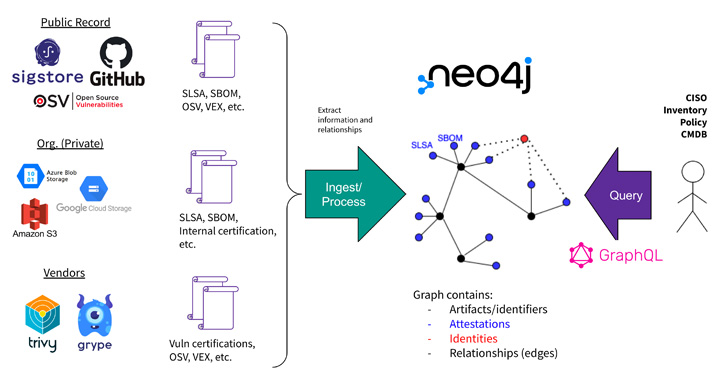
GUAC is the firm’s most recent work to bolster the health and fitness of the provide chain. It achieves this by aggregating computer software security metadata from a combine of public and private sources into a “awareness graph” that can response queries about source chain challenges.
The info that undergirds this architecture is derived from Sigstore, GitHub, Open up Resource Vulnerabilities (OSV), Grype, and Trivy, among some others, to derive significant relationships concerning vulnerabilities, assignments, sources, developers, artifacts, and repositories.

“Querying this graph can drive increased-stage organizational outcomes these as audit, policy, risk administration, and even developer help,” Google claimed.
Place in different ways, the concept is to hook up the diverse dots between a job and its developer, a vulnerability and the corresponding software program model, and the artifact and the resource repository it belongs to.
The aim, therefore, is to not only help organizations to determine if they are impacted by a particular vulnerability, but also estimate the blast radius really should the source chain be compromised.
That claimed, Google also seems to be cognizant of the possible threats that could undermine GUAC, such as scenarios where by the technique is tricked into ingesting cast info about artifacts and their metadata, which it expects to mitigate through cryptographic verification of information paperwork.
“[GUAC] aims to fulfill the use situation of currently being a keep an eye on for general public source chain and security paperwork as well as for internal use by businesses to question info about artifacts that they use,” the internet large famous.
Found this report exciting? Adhere to THN on Facebook, Twitter and LinkedIn to read more special content material we submit.
Some elements of this report are sourced from:
thehackernews.com

 Cybersecurity Workforce Gap Grows by 26% in 2022
Cybersecurity Workforce Gap Grows by 26% in 2022