Google on Tuesday declared the open source availability of OSV-Scanner, a scanner that aims to offer you easy entry to vulnerability information about several tasks.
The Go-based resource, run by the Open up Supply Vulnerabilities (OSV) databases, is designed to link “a project’s listing of dependencies with the vulnerabilities that influence them,” Google computer software engineer Rex Pan in a publish shared with The Hacker Information.
“The OSV-Scanner generates reliable, substantial-excellent vulnerability information and facts that closes the gap among a developer’s checklist of offers and the information in vulnerability databases,” Pan extra.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The notion is to discover all the transitive dependencies of a project and emphasize related vulnerabilities making use of details pulled from OSV.dev databases.
Google further mentioned that the open resource platform supports 16 ecosystems, counting all key languages, Linux distributions (Debian and Alpine), as properly as Android, Linux Kernel, and OSS-Fuzz.
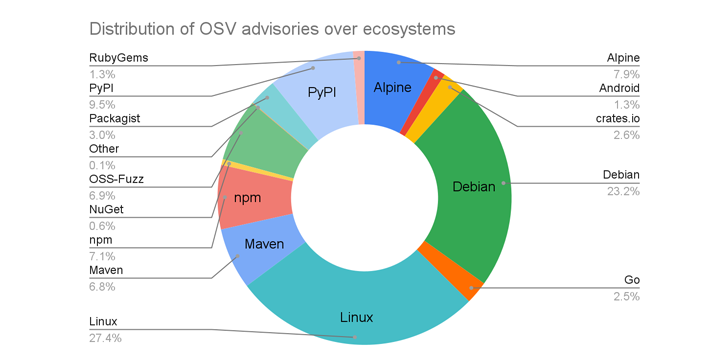
The result of this growth is that OSV.dev is a repository to far more than 38,000 advisories, up from 15,000 security alerts a calendar year ago, with Linux (27.4%), Debian (23.2%), PyPI (9.5%), Alpine (7.9%), and npm (7.1%) taking up the top 5 slots.
As for the future measures, the internet big noted it’s functioning to integrate assistance for C/C++ flaws by setting up a “superior high-quality databases” that requires including “specific dedicate degree metadata to CVEs.”
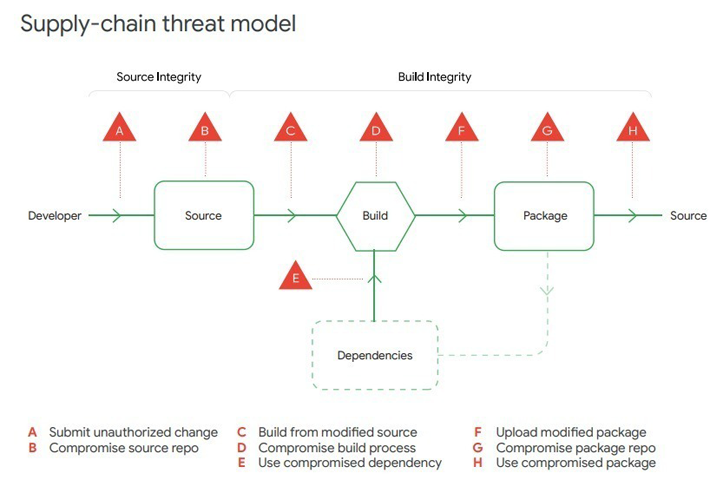
OSV-Scanner arrives almost two months right after Google launched GUAC – limited for Graph for Comprehending Artifact Composition – to enhance Offer chain Amounts for Computer software Artifacts (SLSA or “salsa”) as portion of its efforts to harden software package provide chain security.
Past week, Google also posted a new “Perspectives on Security” report contacting on businesses to build and deploy a popular SLSA framework to prevent tampering, improve integrity, and safe packages versus potential threats.
Other suggestions laid out by the business contain having on supplemental open up supply security duties and adopting a far more holistic approach to addressing risks such as individuals introduced by the Log4j vulnerability and the SolarWinds incident in latest many years.
“Software program offer chain attacks commonly involve strong specialized aptitude and lengthy-phrase determination to pull off,” the company reported. “Advanced actors are additional possible to have both the intent and capacity to conduct these varieties of attacks.”
“Most companies are vulnerable to application supply chain attacks mainly because attackers just take the time to concentrate on third-party vendors with trustworthy connections to their customers’ networks. They then use that belief to burrow further into the networks of their supreme targets.”
Located this short article fascinating? Comply with us on Twitter and LinkedIn to browse far more exceptional content material we put up.
Some areas of this report are sourced from:
thehackernews.com


 Twitter Addresses November Data Leak Claims
Twitter Addresses November Data Leak Claims