In 2022, Russia-backed cyber-attacks focusing on Ukraine rose 250% as opposed to 2020 and all those targeting NATO nations around the world, 300%.
This staggering surge is just one of the results from Google Menace Evaluation Team (TAG) in a February 16 report, Fog of War: How the Ukraine Conflict Transformed the Cyber Threat Landscape, revealed in collaboration with Google Have confidence in & Protection and menace intelligence organization Mandiant, now part of Google Cloud.
In the report, Google discovered that Russia’s intense, multi-faceted approach to “gain a decisive wartime edge in cyberspace” could truly date again to 2019.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
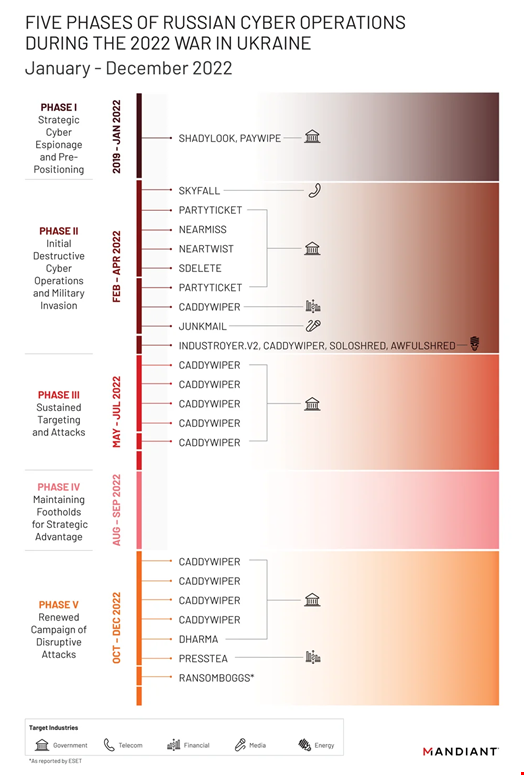
Five Phases of Cyber Operations
During the to start with period highlighted by Google, which spanned in between 2019 and early 2022, Russia ran cyber espionage campaigns from Ukraine and NATO member-states, as nicely as what the American tech huge phone calls “pre-positioning” operations.
From April 2021, just one thirty day period just after Russian troops began to mass on the Ukraine border, the Russian State-of-the-art Persistent Risk (APT) team UNC2589 (aka Frozenvista), “a new, possible GRU actor,” began deploying phishing attacks from Ukrainian businesses, the report statements. The GRU is the prevalent acronym provided to the Russian Armed Forces’ Principal Directorate of the Basic Staff, a armed service intelligence company.
Various other Russian-sponsored followed go well with all over 2021, such as Fancy Bear (APT28, aka Frozenlake).
In mid-January 2022, a wave of disruptive and damaging cyber-attacks commenced, with wiper attacks these kinds of as WhisperGate (aka PayWipe) and its affiliate, WhisperKill (aka ShadyLook).
These were being a style of what was to come in the 2nd phase when Russian troops began their kinetic invasion of Ukraine. The land-advance in February was accompanied by numerous far more disruptive and harmful wiper attacks. This phase lasted until eventually April, with the emergence of quite a few new malware households, which includes the PartyTicket ransomware, the wiper CaddyWiper and Industroyer 2, an up-to-date version of Industroyer, a damaging malware concentrating on industrial command systems (ICS), which is considered to have been applied in the cyber-attack on Ukraine’s energy grid in December 2016.
In May perhaps, Russian-backed threat actors entered a 3rd section the place they started out to reuse the identical malware, largely CaddyWiper, to attack entities in Ukraine and NATO nations around the world.
In accordance to the report, this section lasted until July, adopted by a lull in exercise in the course of August and September. Cyber-attacks resumed in Oct, in a fifth period that saw Russian threat actors use CaddyWiper together with other new malware.
 Resource: Google
Resource: Google
“From its incident reaction do the job, Mandiant noticed far more harmful cyberattacks in Ukraine all through the first four months of 2022 than in the prior 8 years, with attacks peaking all over the commence of the invasion. […] Quite a few operations indicated an attempt by the GRU to harmony competing priorities of accessibility, selection, and disruption all through just about every section of action,” the report reads.
A Multi-Faceted Strategy
In summary, Russia’s multi-pronged offensive technique in cyberspace included the pursuing:
- A spectacular improve in the use of harmful attacks on the Ukrainian federal government, armed service and civilian infrastructure
- A spike in spear-phishing action targeting NATO nations around the world
- An uptick in cyber functions made to further multiple Russian objectives, these as hack-and-leak attacks targeting delicate data
The report confirmed that some actors targeted on precise styles of attacks, this sort of as Frozenlake/Fancy Bear, Frozenvista and Belarusian actor Puschcha (UNC1151) with phishing campaigns versus Ukraine and NATO nations, and Coldriver (aka Gossamer Bear) with hack-and-leak strategies in opposition to Ukraine and the UK.
Just one team, nevertheless, Frozenbarents (aka Sandworm, Voodoo Bear), dubbed “the GRU’s most adaptable operator” by Google, ran all varieties of cyber-attacks in opposition to Ukraine and NATO international locations.
“While we see these attackers focus intensely on the Ukrainian government and armed service entities, the campaigns we disrupted also exhibit a powerful emphasis on critical infrastructure, utilities and public products and services, and the media and info area,” the report reads.
However, the report also pointed out that a lot of of these operations led to “mixed benefits.”
A very good illustration is the Industroyer 2 tried attack on the Ukrainian power sector, which seemed to have failed.
Overt and Covert Disinformation Strategies
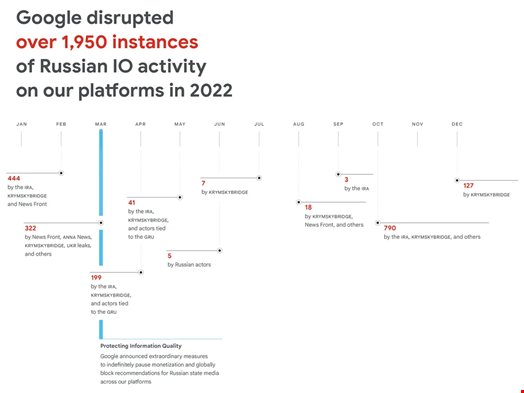
Along with these straightforward cyber-attacks, the report showed that Russia has been operating all sorts of details functions (IO) campaigns, from the most overt condition-sponsored disinformation campaigns run by the infamous St-Petersburg-dependent ‘troll farm,’ the Internet Study Agency (IRA), to a lot more covert campaigns run by affiliate marketers like the Russian consulting agency Krymskybridge or teams linked with Russian intelligence.
Google claimed it “disrupted in excess of 1950 situations of Russian IO exercise in 2022,” targeting both equally Russian and overseas audiences.
 Resource: Google
Resource: Google
The report also confirmed that “the war has split the loyalties of fiscally inspired attackers, [which has increased] the overlap concerning [them] and government-backed menace actors.”
This phenomenon is ideal represented by the fate of the Conti gang, which counted the two Russian and Ukrainian users and exploded just after some of its alleged leaders publicly supported the invasion.
“This shift in the Japanese European cyber-felony ecosystem will likely have extended-expression implications for coordination between criminal teams and the scale of cybercrime around the world,” notes the report.
On the lookout ahead, Google believes “with superior confidence that Russian govt-backed attackers will continue on to perform cyber-attacks from Ukraine and NATO partners, raise disruptive and destructive attacks in reaction to developments on the battlefield [and] more and more broaden to contain NATO companions.
The scientists also assume “with reasonable self-confidence, that Russia will carry on to increase the tempo and scope of IO, significantly as we approach key times like global funding, armed forces help, domestic referendums, and extra.
Some areas of this posting are sourced from:
www.infosecurity-journal.com


 Armenia and Azerbaijan Hackers Use OxtaRAT to Monitor Conflict
Armenia and Azerbaijan Hackers Use OxtaRAT to Monitor Conflict