A 7 days just after it emerged that a advanced mobile spyware dubbed Hermit was employed by the federal government of Kazakhstan in its borders, Google explained it has notified Android users of infected units.
Additionally, vital changes have been executed in Google Perform Safeguard — Android’s designed-in malware protection services — to protect all end users, Benoit Sevens and Clement Lecigne of Google Risk Assessment Group (TAG) stated in a Thursday report.
Hermit, the work of an Italian vendor named RCS Lab, was documented by Lookout past week, contacting out its modular feature-established and its talents to harvest delicate information such as contact logs, contacts, pictures, specific locale, and SMS messages.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
After the menace has carefully insinuated alone into a device, it is really also geared up to file audio and make and redirect phone calls, in addition to abusing its permissions to accessibility products and services to continue to keep tabs on the foreground applications made use of by the victims.
Its modularity also allows it to be wholly customizable, equipping the spyware’s performance to be extended or altered at will. It really is not right away crystal clear who had been focused in the campaign, or which of RCS Lab clientele were concerned.
The Milan-based firm, operating since 1993, promises to provide “regulation enforcement companies globally with slicing-edge technological answers and specialized aid in the field of lawful interception for much more than twenty yrs.” More than 10,000 intercepted targets are purported to be managed daily in Europe by itself.
“Hermit is nevertheless yet another illustration of a digital weapon currently being employed to concentrate on civilians and their mobile units, and the details gathered by the malicious get-togethers concerned will surely be invaluable,” Richard Melick, director of risk reporting for Zimperium, claimed.
The targets have their telephones contaminated with the spy instrument via drive-by downloads as initial infection vectors, which, in flip, involves sending a one of a kind hyperlink in an SMS information that, upon clicking, activates the attack chain.
It really is suspected that the actors labored in collaboration with the targets’ internet provider providers (ISPs) to disable their cellular facts connectivity, adopted by sending an SMS that urged the recipients to install an software to restore cell knowledge obtain.
“We believe this is the motive why most of the programs masqueraded as cellular provider purposes,” the researchers reported. “When ISP involvement is not achievable, purposes are masqueraded as messaging applications.”
To compromise iOS people, the adversary is claimed to have relied on provisioning profiles that permit pretend carrier-branded apps to be sideloaded on to the equipment without the need of the have to have for them to be available on the Application Keep.
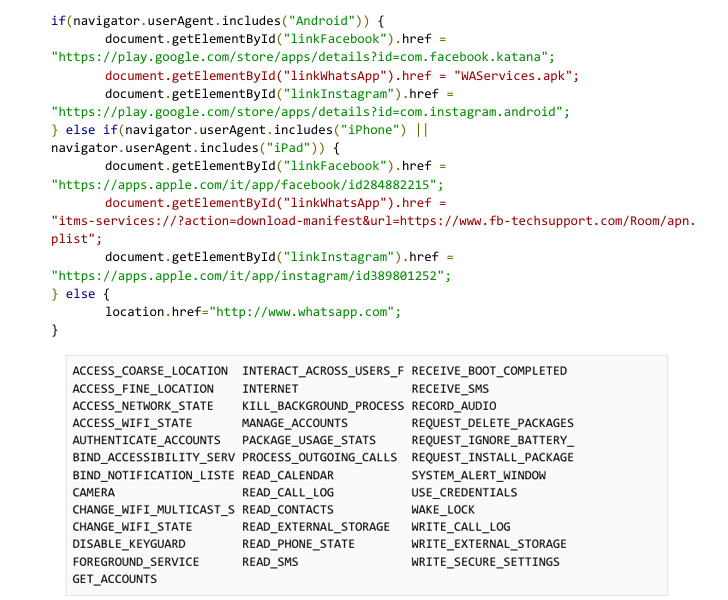
An assessment of the iOS edition of the application exhibits that it leverages as several as six exploits — CVE-2018-4344, CVE-2019-8605, CVE-2020-3837, CVE-2020-9907, CVE-2021-30883, and CVE-2021-30983 — to exfiltrate data files of fascination, such as the WhatsApp database, from the system.
“As the curve slowly and gradually shifts towards memory corruption exploitation having more expensive, attackers are possible shifting much too,” Google Project Zero’s Ian Beer mentioned in a deep-dive evaluation of an iOS artifact that impersonated the My Vodafone provider app.

On Android, the generate-by attacks need that victims allow a placing to set up third-party applications from mysterious sources, executing so which benefits in the rogue app, masquerading as smartphone models like Samsung, requests for in depth permissions to obtain its destructive plans.
The Android variant, aside from attempting to root the system for entrenched obtain, is also wired in different ways in that as a substitute of bundling exploits in the APK file, it contains operation that permits it to fetch and execute arbitrary distant factors that can talk with the principal app.
“This marketing campaign is a fantastic reminder that attackers do not normally use exploits to accomplish the permissions they will need,” the researchers noted. “Simple an infection vectors and drive by downloads still function and can be very effective with the aid from nearby ISPs.”
Stating that seven of the nine zero-working day exploits it found out in 2021 were created by industrial suppliers and bought to and utilized by government-backed actors, the tech behemoth claimed it can be tracking far more than 30 suppliers with various degrees of sophistication who are recognised to trade exploits and surveillance capabilities.
What is actually extra, Google TAG elevated problems that distributors like RCS Lab are “stockpiling zero-working day vulnerabilities in solution” and cautioned that this poses severe dangers contemplating a amount of adware suppliers have been compromised over the past 10 many years, “boosting the specter that their stockpiles can be introduced publicly devoid of warning.”
“Our results underscore the extent to which commercial surveillance distributors have proliferated abilities historically only made use of by governments with the complex skills to develop and operationalize exploits,” TAG explained.
“Even though use of surveillance systems may well be lawful under nationwide or international legislation, they are normally located to be made use of by governments for applications antithetical to democratic values: concentrating on dissidents, journalists, human legal rights employees and opposition party politicians.”
Uncovered this write-up exciting? Stick to THN on Fb, Twitter and LinkedIn to examine additional exceptional material we post.
Some pieces of this article are sourced from:
thehackernews.com


 Cisco to exit Russia, Belarus in business wind-down
Cisco to exit Russia, Belarus in business wind-down