A Chinese nation-point out group qualified an unnamed Taiwanese media organization to produce an open up supply red teaming tool identified as Google Command and Handle (GC2) amid broader abuse of Google’s infrastructure for malicious finishes.
The tech giant’s Threat Evaluation Group (TAG) attributed the campaign to a menace actor it tracks less than the geological and geographical-themed moniker HOODOO, which is also acknowledged by the names APT41, Barium, Bronze Atlas, Wicked Panda, and Winnti.
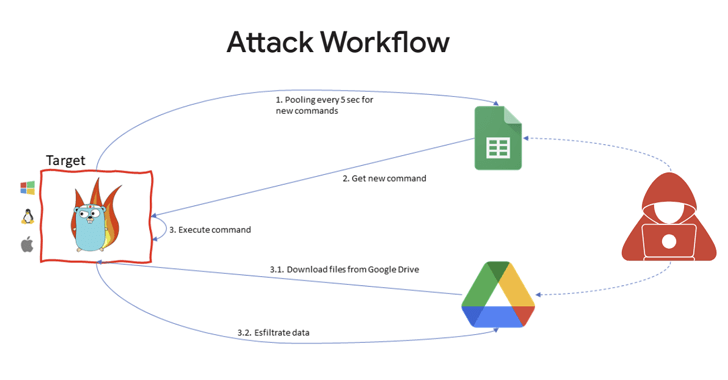
The starting position of the attack is a phishing email that is made up of inbound links to a password-protected file hosted on Google Travel, which, in flip, incorporates the GC2 instrument to study instructions from Google Sheets and exfiltrate facts using the cloud storage company.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Soon after installation on the sufferer machine, the malware queries Google Sheets to receive attacker instructions,” Google’s cloud division claimed in its sixth Danger Horizons Report. “In addition to exfiltration via Travel, GC2 enables the attacker to down load added documents from Travel on to the sufferer technique.”
Google claimed the threat actor formerly used the very same malware in July 2022 to target an Italian position look for website.
The advancement is noteworthy for two causes: Very first, it implies that Chinese menace groups are progressively relying on publicly offered tooling like Cobalt Strike and GC2 to confuse attribution initiatives.
Secondly, it also factors to the developing adoption of malware and instruments written in the Go programming language, owing to its cross-system compatibility and its modular nature.
Google further more cautioned that the “undeniable value of cloud solutions” have made them a rewarding focus on for cybercriminals and govt-backed actors alike, “either as hosts for malware or offering the infrastructure for command-and-command (C2).”
Forthcoming WEBINARMaster the Artwork of Dark Web Intelligence Accumulating
Master the art of extracting danger intelligence from the dark web – Be a part of this specialist-led webinar!
Save My Seat!
A circumstance in point is the use of Google Travel for storing malware this sort of as Ursnif (aka Gozi) and DICELOADER (aka Lizar or Tirion) in the kind of ZIP archive information as part of disparate phishing campaigns.
“The most common vector utilized to compromise any network, which includes cloud scenarios is to get in excess of an account’s credentials specifically: either for the reason that there is no password, as with some default configurations, or for the reason that a credential has been leaked or recycled or is frequently so weak as to be guessable,” Google Cloud’s Christopher Porter stated.
The results appear 3 months following Google Cloud comprehensive APT10’s (aka Bronze Riverside, Cicada, Potassium, or Stone Panda) focusing on of cloud infrastructure and VPN systems to breach company environments and exfiltrate info of interest.
Observed this posting appealing? Comply with us on Twitter and LinkedIn to examine far more unique content material we article.
Some areas of this post are sourced from:
thehackernews.com

 Tour of the Underground: Master the Art of Dark Web Intelligence Gathering
Tour of the Underground: Master the Art of Dark Web Intelligence Gathering