Google on Wednesday introduced the .1 Beta model of GUAC (small for Graph for Knowing Artifact Composition) for corporations to protected their application supply chains.
To that finish, the lookup large is producing accessible the open resource framework as an API for builders to combine their individual resources and policy engines.
GUAC aims to mixture computer software security metadata from unique sources into a graph database that maps out relationships between computer software, aiding corporations establish how a single piece of application has an effect on another.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Graph for Being familiar with Artifact Composition (GUAC) presents you structured and actionable insights into your software program supply chain security position,” Google states in its documentation.
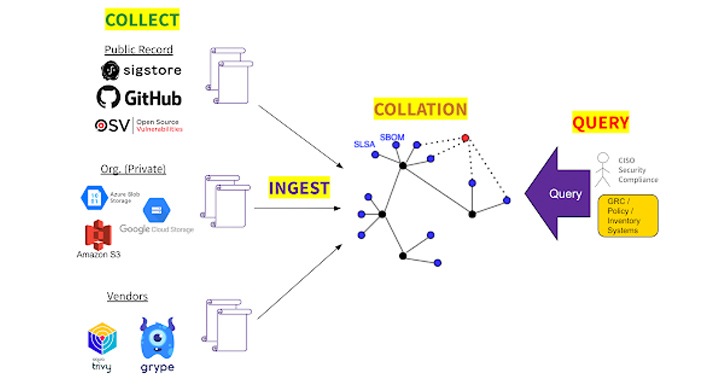
“GUAC ingests program security metadata, like SBOMs, and maps out the romantic relationship concerning application so that you can entirely fully grasp your computer software security posture.”
In other phrases, it’s designed to convey together Software Bill of Products (SBOM) files, SLSA attestations, OSV vulnerability feeds, deps.dev insights, and a company’s inside personal metadata to assist make a greater photo of the risk profile and visualize the associations among artifacts, deals, and repositories.
Forthcoming WEBINARZero Belief + Deception: Understand How to Outsmart Attackers!
Find how Deception can detect sophisticated threats, stop lateral motion, and increase your Zero Believe in tactic. Be part of our insightful webinar!
Conserve My Seat!
With this sort of a setup in location, the goal is to tackle superior-profile provide chain attacks, create a patch plan, and swiftly reply to security compromises.
“For example, GUAC can be utilized to certify that a builder is compromised (e.g., through credential leakage or ingestion of malware) and then query for affected artifacts,” Google stated.
“This permits the [chief information security officer] to simply create a policy to forbid use of any software package from in the blast radius.”
Discovered this short article exciting? Observe us on Twitter and LinkedIn to study far more distinctive content we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Lazarus Group Targeting Microsoft Web Servers to Launch Espionage Malware
Lazarus Group Targeting Microsoft Web Servers to Launch Espionage Malware