E-commerce industries in South Korea and the U.S. are at the obtaining finish of an ongoing GuLoader malware campaign, cybersecurity agency Trellix disclosed late last thirty day period.
The malspam activity is noteworthy for transitioning away from malware-laced Microsoft Phrase files to NSIS executable data files for loading the malware. Other countries targeted as portion of the campaign include things like Germany, Saudi Arabia, Taiwan and Japan.
NSIS, brief for Nullsoft Scriptable Put in System, is a script-driven open source procedure utilized to develop installers for the Windows operating process.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Whilst attack chains in 2021 leveraged a ZIP archive made up of a macro-laced Term document to fall an executable file tasked with loading GuLoader, the new phishing wave employs NSIS documents embedded inside ZIP or ISO visuals to activate the an infection.
“Embedding malicious executable files in archives and pictures can assist threat actors evade detection,” Trellix researcher Nico Paulo Yturriaga stated.
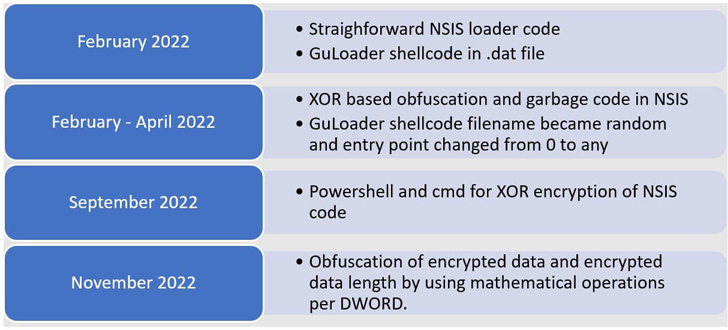
Over the program of 2022, the NSIS scripts applied to produce GuLoader are reported to have developed in sophistication, packing in extra obfuscation and encryption levels to conceal the shellcode.
The enhancement is also emblematic of a broader shift in just the danger landscape, which has witnessed spikes in alternate malware distribution approaches in reaction to Microsoft’s blocking of macros in Business office information downloaded from the internet.
“The migration of GuLoader shellcode to NSIS executable information is a notable case in point to clearly show the creativeness and persistence of risk actors to evade detection, avoid sandbox examination and obstruct reverse engineering,” Yturriaga noted.
Located this article attention-grabbing? Adhere to us on Twitter and LinkedIn to read through a lot more special material we publish.
Some parts of this posting are sourced from:
thehackernews.com


 Warning issued over ransomware attacks targeting VMware ESXi servers globally
Warning issued over ransomware attacks targeting VMware ESXi servers globally