Microsoft on Tuesday explained it took measures to disable bogus Microsoft Partner Network (MPN) accounts that had been used for generating malicious OAuth applications as portion of a malicious marketing campaign built to breach organizations’ cloud environments and steal email.
“The purposes made by these fraudulent actors have been then applied in a consent phishing campaign, which tricked customers into granting permissions to the fraudulent applications,” the tech big explained. “This phishing marketing campaign specific a subset of buyers mostly based mostly in the U.K. and Eire.”
Consent phishing is a social engineering attack whereby people are tricked into granting permissions to malicious cloud applications, which can then be weaponized to get obtain to respectable cloud products and services and delicate user facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Windows maker mentioned it turned conscious of the marketing campaign on December 15, 2022. It has because alerted impacted shoppers via email, with the enterprise noting that the threat actors abused the consent to exfiltrate mailboxes.
On top of that, Microsoft mentioned it implemented more security actions to strengthen the vetting procedure linked with the Microsoft Cloud Associate Plan (previously MPN) and reduce the likely for fraud in the potential.
The disclosure coincides with a report unveiled by Proofpoint about how menace actors have correctly exploited Microsoft’s “confirmed publisher” position to infiltrate the cloud environments of corporations.
What is noteworthy about the campaign is that by mimicking well-liked brand names, it was also effective at fooling Microsoft in order to attain the blue verified badge. “The actor employed fraudulent associate accounts to add a verified publisher to OAuth app registrations they designed in Azure Advert,” the enterprise discussed.
These attacks, which were very first observed on December 6, 2022, utilized lookalike variations of authentic applications like Zoom to deceive targets into authorizing access and aid information theft. Targets included economic, marketing and advertising, professionals, and senior executives.
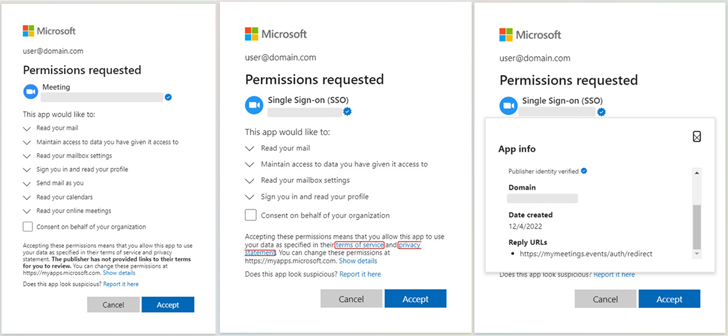
Proofpoint pointed out the destructive OAuth apps had “considerably-reaching delegated permissions” these as looking at e-mails, adjusting mailbox options, and gaining obtain to information and other info linked to the user’s account.
It also mentioned that not like a former marketing campaign that compromised present Microsoft confirmed publishers to get edge of OAuth application privileges, the most up-to-date attacks are created to impersonate genuine publishers to develop into verified and distribute the rogue apps.
Two of the apps in issue had been named “One Indication-on (SSO),” even though the 3rd application was named “Conference” in an attempt to masquerade as video conferencing application. All three apps, developed by a few unique publishers, targeted the exact firms and leveraged the identical attacker-managed infrastructure.
“The potential effect to businesses contains compromised consumer accounts, knowledge exfiltration, model abuse of impersonated corporations, business enterprise email compromise (BEC) fraud, and mailbox abuse,” the enterprise security company explained.
The marketing campaign is claimed to have appear to an conclude on December 27, 2022, just after Proofpoint educated Microsoft of the attack on December 20 and the applications had been disabled.
The results exhibit the sophistication that has absent into mounting the attack, not to mention bypass Microsoft’s security protections and misuse the believe in customers spot in organization suppliers and assistance providers.
This is not the initial time bogus OAuth apps have been applied to target Microsoft’s cloud services. In January 2022, Proofpoint in depth a further threat activity dubbed OiVaVoii that specific large-stage executives to seize manage of their accounts.
Then in September 2022, Microsoft unveiled that it dismantled an attack that manufactured use of rogue OAuth purposes deployed on compromised cloud tenants to finally seize management of Exchange servers and distribute spam.
Discovered this write-up intriguing? Abide by us on Twitter and LinkedIn to examine more exceptional information we publish.
Some parts of this posting are sourced from:
thehackernews.com

 Additional Supply Chain Vulnerabilities Uncovered in AMI MegaRAC BMC Software
Additional Supply Chain Vulnerabilities Uncovered in AMI MegaRAC BMC Software