Destructive actors have been noticed abusing authentic adversary simulation software program in their attacks in an attempt to stay beneath the radar and evade detection.
Palo Alto Networks Device 42 said a malware sample uploaded to the VirusTotal database on May well 19, 2022, contained a payload related with Brute Ratel C4, a rather new innovative toolkit “developed to keep away from detection by endpoint detection and reaction (EDR) and antivirus (AV) capabilities.”
Authored by an Indian security researcher named Chetan Nayak, Brute Ratel (BRc4) is analogous to Cobalt Strike and is explained as a “custom-made command-and-handle heart for red workforce and adversary simulation.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The industrial program was initially unveiled in late 2020 and has due to the fact attained about 480 licenses throughout 350 shoppers. Just about every license is made available at $2,500 per person for a year, soon after which it can be renewed for the very same period at the cost of $2,250.
BRc4 is equipped with a vast wide range of capabilities, these kinds of as method injection, automating adversary TTPs, capturing screenshots, uploading and downloading data files, aid for a number of command-and-command channels, and the ability to retain memory artifacts concealed from anti-malware engines, amid others.
The artifact, which was uploaded from Sri Lanka, masquerades as a curriculum vitae of an particular person named Roshan Bandara (“Roshan_CV.iso”) but in fact is an optical disc impression file that, when double-clicked, mounts it as a Windows generate made up of a seemingly harmless Word doc that, upon launching, installs BRc4 on the user’s machine and establishes communications with a distant server.
The shipping of packaged ISO documents is usually despatched by means of spear-phishing email strategies, although it truly is not apparent if the exact same strategy was made use of to deliver the payload to the concentrate on environment.
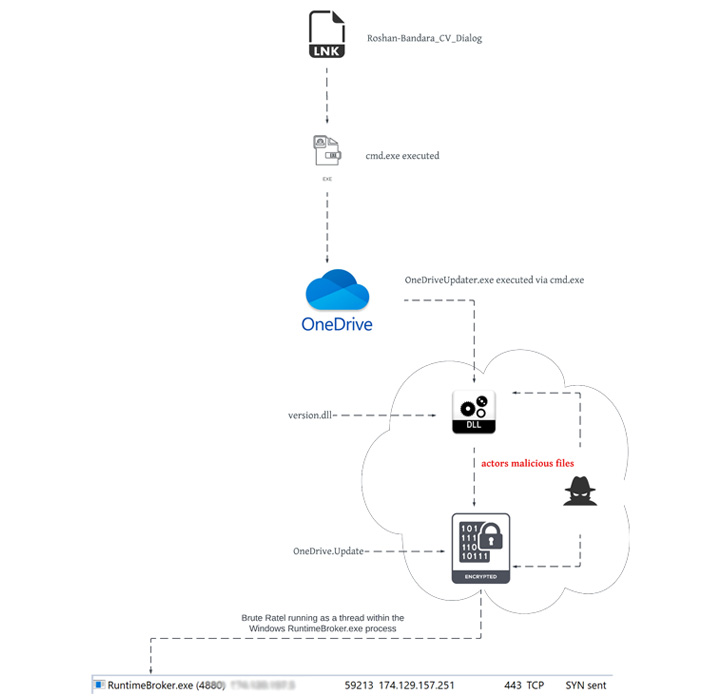
“The composition of the ISO file, Roshan_CV.ISO, carefully resembles that of other country-state APT tradecraft,” Device 42 scientists Mike Harbison and Peter Renals explained, contacting out similarities to that of a likewise packaged ISO file earlier attributed to Russian country-state actor APT29 (aka Cozy Bear, The Dukes, or Iron Hemlock).
APT29 rose to notoriety previous year right after the point out-sponsored group was blamed for orchestrating the massive-scale SolarWinds offer chain attack.

The cybersecurity firm mentioned it also spotted a second sample that was uploaded to VirusTotal from Ukraine a day later on and which exhibited code overlaps to that of a module accountable for loading BRc4 in memory. The investigation has since unearthed 7 much more BRc4 samples dating back to February 2021.
By inspecting the C2 server that was employed as a covert channel, a number of opportunity victims have been recognized. This incorporates an Argentinian group, an IP tv provider giving North and South American information, and a big textile maker in Mexico.
“The emergence of a new penetration screening and adversary emulation capacity is considerable,” the scientists stated. “But a lot more alarming is the performance of BRc4 at defeating modern defensive EDR and AV detection capabilities.”
Shortly just after the conclusions became community, Nayak tweeted that “appropriate steps have been taken versus the uncovered licenses which have been bought in the black market,” incorporating BRc4 v1.1 “will transform each and every factor of IoC uncovered in the preceding releases.”
Found this report intriguing? Stick to THN on Facebook, Twitter and LinkedIn to go through additional distinctive written content we article.
Some sections of this posting are sourced from:
thehackernews.com


 The End of False Positives for Web and API Security Scanning?
The End of False Positives for Web and API Security Scanning?