A new attack vector concentrating on the Visible Studio Code extensions marketplace could be leveraged to upload rogue extensions masquerading as their legitimate counterparts with the objective of mounting provide chain attacks.
The strategy “could act as an entry position for an attack on a lot of businesses,” Aqua security researcher Ilay Goldman explained in a report printed last 7 days.
VS Code extensions, curated via a market made offered by Microsoft, let builders to incorporate programming languages, debuggers, and applications to the VS Code source-code editor to augment their workflows.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“All extensions operate with the privileges of the user that has opened the VSCode with no any sandbox,” Goldman stated, describing the likely pitfalls of working with VS code extensions. “This suggests that the extension can install any program on your computer together with ransomwares, wipers, and a lot more.”
To that close, Aqua discovered that not only is it possible for a danger actor to impersonate a well-liked extension with modest variants to the URL, the market also permits the adversary to use the similar identify and extension publisher particulars, together with the undertaking repository data.
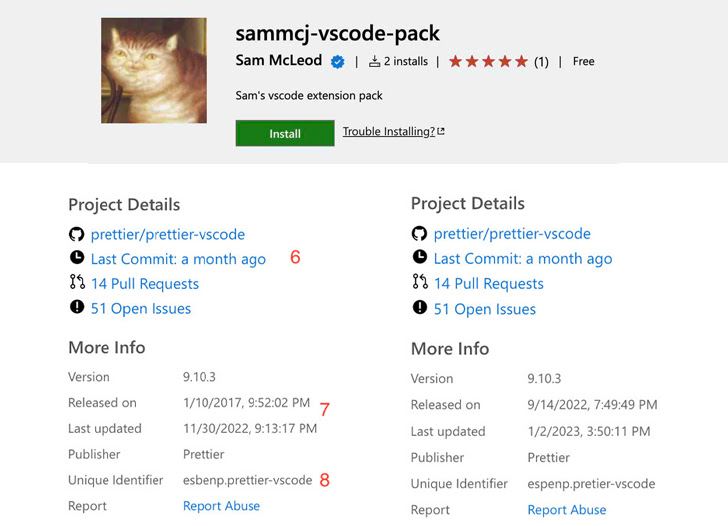
Though the process won’t allow for the variety of installs and the selection of stars to be replicated, the actuality that there are no limits on the other pinpointing qualities indicates it could be used to deceive builders.
The investigation also found that the verification badge assigned to authors could be trivially bypassed as the examine mark only proves that the extension publisher is the true proprietor of a area.
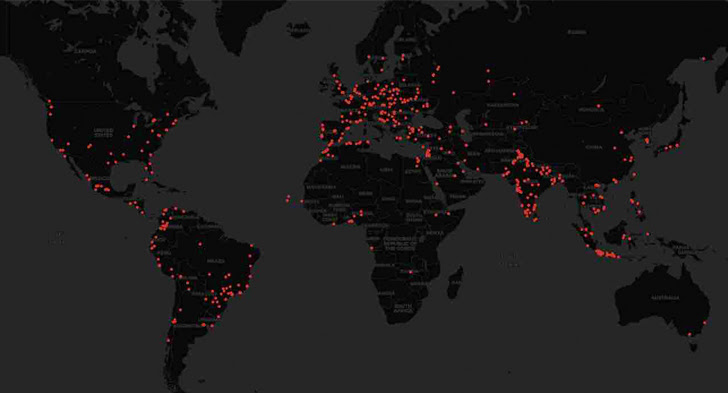
In other words, a malicious actor could buy any domain, sign-up it to get a confirmed test mark, and ultimately add a trojanized extension with the same identify as that of a legit just one to the marketplace.
A evidence-of-principle (PoC) extension masquerading as the Prettier code formatting utility racked up about 1,000 installations inside 48 several hours by builders throughout the planet, Aqua explained. It has since been taken down.
This is not the 1st time worries have been raised about software package provide chain threats in the VS Code extensions marketplace.
In May possibly 2021, business security firm Snyk uncovered a range of security flaws in well-known VS Code extensions with thousands and thousands of downloads that could have been abused by threat actors to compromise developer environments.
“Attackers are constantly doing work to extend their arsenal of techniques letting them to operate malicious code inside the network of companies,” Goldman reported.
Observed this report attention-grabbing? Follow us on Twitter and LinkedIn to examine much more exceptional content we article.
Some components of this report are sourced from:
thehackernews.com


 How To Comply With The Cyber Insurance MFA Checklistwww.silverfort.comMulti-Factor AuthenticationLearn how to comply with the checklist of resources requiring MFA coverage in cyber insurance policies.
How To Comply With The Cyber Insurance MFA Checklistwww.silverfort.comMulti-Factor AuthenticationLearn how to comply with the checklist of resources requiring MFA coverage in cyber insurance policies.