Researchers have thorough a beforehand undocumented .NET-primarily based submit-exploitation framework termed IceApple that has been deployed on Microsoft Exchange server instances to aid reconnaissance and data exfiltration.
“Suspected to be the get the job done of a state-nexus adversary, IceApple stays below active enhancement, with 18 modules observed in use throughout a variety of organization environments, as of May 2022,” CrowdStrike reported in a Wednesday report.
The cybersecurity firm, which uncovered the subtle malware in late 2021, observed its existence in multiple target networks and in geographically distinct areas. Targeted victims span a broad range of sectors, like technology, academic, and govt entities.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
A submit-exploitation toolset, as the title implies, is not utilised to give original access, but is alternatively utilized to have out observe-on attacks immediately after getting already compromised the hosts in question.
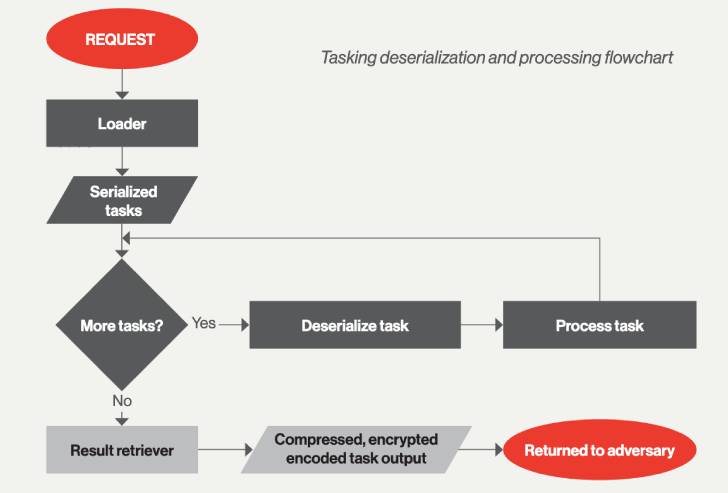
IceApple is noteworthy for the simple fact that it truly is an in-memory framework, indicating an endeavor on the portion of the threat actor to manage a very low forensic footprint and evade detection, which, in turn, bears all hallmarks of a very long-phrase intelligence-accumulating mission.
Even though intrusions noticed so far have concerned the malware currently being loaded on Microsoft Exchange Servers, IceApple is able of functioning under any Internet Information Services (IIS) web application, producing it a powerful menace.
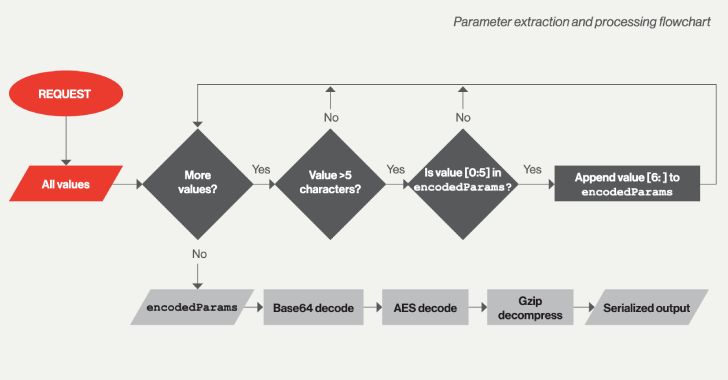
The various modules that come with the framework equip the malware to list and delete information and directories, create knowledge, steal qualifications, question Energetic Directory, and export delicate knowledge. Establish timestamps on these components day again to Could 2021.
“At its core, IceApple is a put up-exploitation framework concentrated on raising an adversary’s visibility of a concentrate on by means of acquisition of credentials and exfiltration of facts,” the researchers concluded.
“IceApple has been developed by an adversary with detailed expertise of the interior workings of IIS. Guaranteeing all web purposes are frequently and fully patched is critical to stopping IceApple from ending up in your atmosphere.”
Discovered this article fascinating? Abide by THN on Fb, Twitter and LinkedIn to read much more exceptional content material we put up.
Some elements of this post are sourced from:
thehackernews.com

 CISA Urges Organizations to Patch Actively Exploited F5 BIG-IP Vulnerability
CISA Urges Organizations to Patch Actively Exploited F5 BIG-IP Vulnerability