Risk actors have been exploiting the freshly disclosed zero-working day flaw in Palo Alto Networks PAN-OS software courting back again to March 26, 2024, virtually a few weeks right before it came to light-weight yesterday.
The network security firm’s Device 42 division is tracking the activity below the identify Procedure MidnightEclipse, attributing it as the do the job of a one threat actor of mysterious provenance.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The security vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.), is a command injection flaw that permits unauthenticated attackers to execute arbitrary code with root privileges on the firewall.
It can be really worth noting that the issue is applicable only to PAN-OS 10.2, PAN-OS 11., and PAN-OS 11.1 firewall configurations that have GlobalProtect gateway and device telemetry enabled.
Operation MidnightEclipse entails the exploitation of the flaw to build a cron job that operates each and every minute to fetch instructions hosted on an external server (“172.233.228[.]93/coverage” or “172.233.228[.]93/patch”), which are then executed making use of the bash shell.
The attackers are claimed to have manually managed an access command listing (ACL) for the command-and-command (C2) server to make certain that it can only be accessed from the unit communicating with it.

While the specific nature of the command is unfamiliar, it is really suspected that the URL serves as a supply car or truck for a Python-based backdoor on the firewall that Volexity – which identified in-the-wild exploitation of CVE-2024-3400 on April 10, 2024 – is tracking as UPSTYLE and is hosted on a unique server (“144.172.79[.]92” and “nhdata.s3-us-west-2.amazonaws[.]com”).
The Python file is designed to produce and start an additional Python script (“method.pth”), which subsequently decodes and runs the embedded backdoor component which is responsible for executing the danger actor’s commands in a file termed “sslvpn_ngx_mistake.log.” The final results of the operation are penned to a separate file named “bootstrap.min.css.”
The most attention-grabbing factor of the attack chain is that the two the information utilized to extract the instructions and create the effects are authentic documents involved with the firewall –
- /var/log/pan/sslvpn_ngx_error.log
- /var/appweb/sslvpndocs/global-secure/portal/css/bootstrap.min.css
As for how the commands are created to the web server mistake log, the danger actor forges specifically crafted network requests to a non-existent web website page that contains a unique pattern. The backdoor then parses the log file and queries for the line matching the exact normal expression (“img[([a-zA-Z0-9+/=]+)]”) to decode and operate the command in it.
“The script will then make an additional thread that runs a purpose identified as restore,” Device 42 stated. “The restore perform normally takes the authentic information of the bootstrap.min.css file, as effectively as the unique entry and modified times, sleeps for 15 seconds and writes the authentic contents back to the file and sets the obtain and modified moments to their originals.”
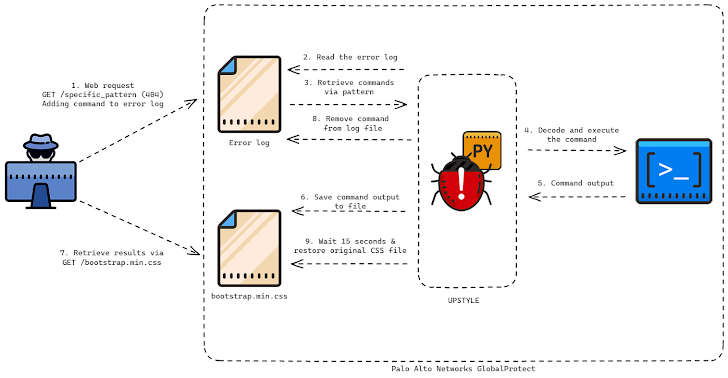
The primary objective appears to be to stay clear of leaving traces of the command outputs, necessitating that the results are exfiltrated inside 15 seconds prior to the file is overwritten.
Volexity, in its individual examination, mentioned it noticed the menace actor remotely exploiting the firewall to make a reverse shell, down load further tooling, pivot into internal networks, and in the end exfiltrate facts. The specific scale of the marketing campaign is presently unclear. The adversary has been assigned the moniker UTA0218 by the corporation.

“The tradecraft and speed employed by the attacker indicates a extremely capable threat actor with a crystal clear playbook of what to obtain to additional their goals,” the American cybersecurity company stated.
“UTA0218’s first goals were aimed at grabbing the area backup DPAPI keys and targeting active listing qualifications by getting the NTDS.DIT file. They further focused consumer workstations to steal saved cookies and login details, along with the users’ DPAPI keys.”
Companies are recommended to glimpse for symptoms of lateral motion internally from their Palo Alto Networks GlobalProtect firewall machine.
The enhancement has also prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to incorporate the flaw to its Known Exploited Vulnerabilities (KEV) catalog, demanding federal companies to utilize the patches by April 19 to mitigate opportunity threats. Palo Alto Networks is anticipated to release fixes for the flaw no later on than April 14.
“Targeting edge products continues to be a well known vector of attack for able risk actors who have the time and methods to spend into exploring new vulnerabilities,” Volexity said.
“It is hugely probable UTA0218 is a point out-backed danger actor based mostly on the methods necessary to establish and exploit a vulnerability of this character, the style of victims qualified by this actor, and the abilities shown to put in the Python backdoor and further obtain sufferer networks.”
Discovered this posting interesting? Follow us on Twitter and LinkedIn to read through much more exclusive articles we article.
Some areas of this write-up are sourced from:
thehackernews.com


 Popular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files
Popular Rust Crate liblzma-sys Compromised with XZ Utils Backdoor Files