The U.S. Cybersecurity and Infrastructure Security Company (CISA) on Friday disclosed facts of a “novel persistent backdoor” named SUBMARINE deployed by danger actors in relationship with the hack on Barracuda Email Security Gateway (ESG) appliances.
“SUBMARINE contains a number of artifacts — which includes a SQL set off, shell scripts, and a loaded library for a Linux daemon — that jointly help execution with root privileges, persistence, command and regulate, and cleanup,” the company explained.
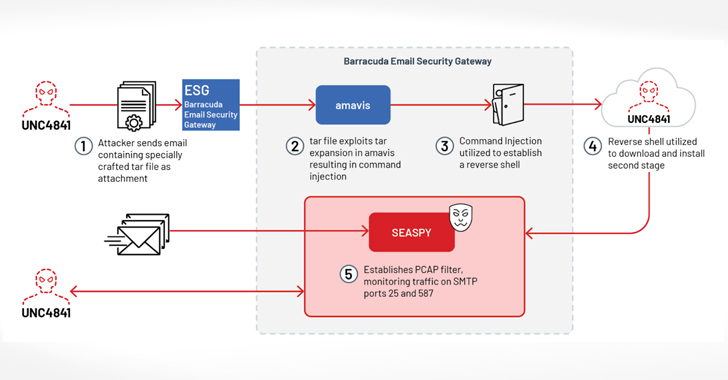
The conclusions occur from an investigation of malware samples obtained from an unnamed firm that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868 (CVSS score: 9.8), which makes it possible for for remote command injection.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Evidence gathered so significantly displays that the attackers behind the activity, a suspected China nexus-actor tracked by Mandiant as UNC4841, leveraged the flaw as a zero-working day in Oct 2022 to attain first accessibility to victim environments and implanted backdoors to create and retain persistence.
To that end, the an infection chain associated sending phishing emails with booby-trapped TAR file attachments to set off exploitation, main to the deployment of a reverse shell payload to create communication with the danger actor’s command-and-management (C2) server, from wherever a passive backdoor acknowledged as SEASPY is downloaded for executing arbitrary instructions on the machine.
SUBMARINE, also codenamed DEPTHCHARGE by the Google-owned danger intelligence agency, is the most current malware relatives to be learned in connection with the operation, which resides in a Structured Query Language (SQL) database on the ESG appliance.
Impending WEBINARShield Versus Insider Threats: Master SaaS Security Posture Management
Concerned about insider threats? We’ve got you covered! Join this webinar to take a look at practical approaches and the techniques of proactive security with SaaS Security Posture Management.
Be part of Currently
It is believed to have been “deployed in reaction to remediation efforts,” echoing Mandiant’s characterization of the adversary as an aggressive actor capable of promptly altering their malware and employing added persistence mechanisms in an try to sustain their access.
The agency further more mentioned it “analyzed artifacts associated to SUBMARINE that contained the contents of the compromised SQL databases,” and that it “poses a serious danger for lateral movement.”
Uncovered this article interesting? Observe us on Twitter and LinkedIn to go through more special content material we article.
Some areas of this article are sourced from:
thehackernews.com

 Ivanti Warns of Another Endpoint Manager Mobile Vulnerability Under Active Attack
Ivanti Warns of Another Endpoint Manager Mobile Vulnerability Under Active Attack