Risk actors have been distributing destructive purposes less than the guise of seemingly harmless searching apps to concentrate on clients of 8 Malaysian banks considering that at least November 2021.
The attacks associated location up fraudulent but respectable-looking internet websites to trick users into downloading the applications, Slovak cybersecurity company ESET explained in a report shared with The Hacker Information.
The copycat web sites impersonated cleaning providers this kind of as Maid4u, Grabmaid, Maria’s Cleansing, Maid4u, YourMaid, Maideasy and MaidACall and a pet shop named PetsMore, all of which are aimed at consumers in Malaysia.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“The danger actors use these phony e-store apps to phish for banking qualifications,” ESET reported. “The apps also ahead all SMS messages obtained by the sufferer to the malware operators in case they comprise 2FA codes sent by the lender.”
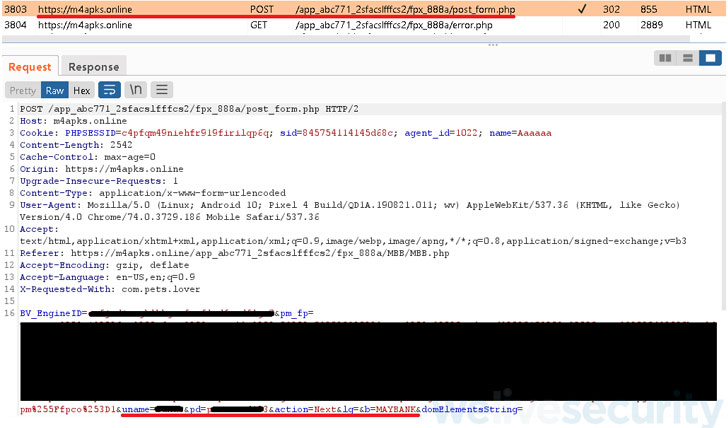
The specific banks involve Maybank, Affin Financial institution, Community Bank Berhad, CIMB bank, BSN, RHB, Financial institution Islam Malaysia, and Hong Leong Financial institution.
The internet websites, distributed by Fb advertisements, urge people to obtain what the attackers declare to be are Android applications readily available on the Google Play Retail outlet, but in actuality, redirect them to rogue servers below their control.
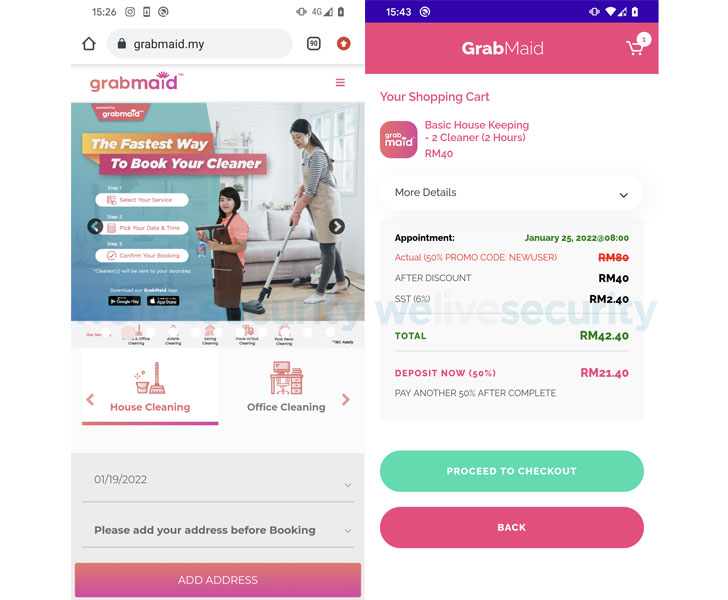
It is really worth noting below that the attack hinges on the prerequisite that the possible victims enable the non-default “Set up unidentified applications” alternative on their equipment for it to succeed. What is actually much more, five of the abused providers do not even have an app on Google Perform.
After launched, the apps prompt the users to indication in to their accounts, making it possible for them to spot bogus orders, adhering to which solutions are offered to finish the checkout approach by including a fund transfer from their bank accounts.
“Just after selecting the immediate transfer choice, victims are offered [with] a faux FPX payment webpage and asked to select their lender out of the eight Malaysian banks presented, and then enter their credentials,” ESET malware researcher Lukáš Štefanko claimed.
The greatest aim of the campaign is to steal the banking credentials entered by the people and exfiltrate it to the attacker-managed server, even though exhibiting an mistake message that the entered user ID or password is invalid.
In addition, the pretend apps are engineered to access and transmit all SMS messages been given by the consumers to the remote server in the celebration the financial institution accounts are secured by two-factor authentication.
“Though the marketing campaign targets Malaysia exclusively for now, it may well grow to other nations and banking companies afterwards on,” Štefanko explained. “At this time, the attackers are after banking credentials, but they may also empower the theft of credit card information in the upcoming.”
Discovered this report interesting? Follow THN on Fb, Twitter and LinkedIn to examine far more exceptional material we put up.
Some components of this posting are sourced from:
thehackernews.com




 No 10 urges gov and businesses to “act as one” against Russian cyber attacks
No 10 urges gov and businesses to “act as one” against Russian cyber attacks