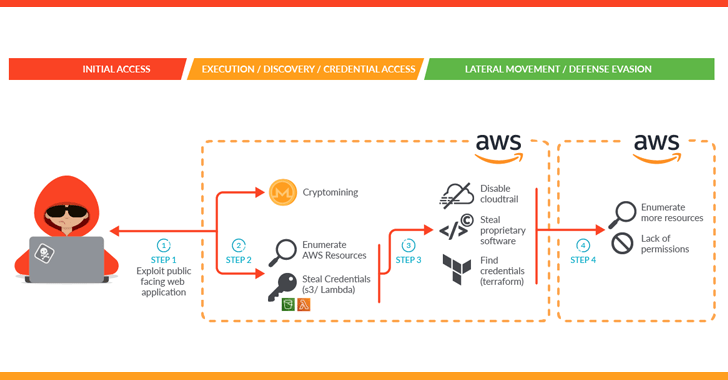
A sophisticated attack campaign dubbed SCARLETEEL is concentrating on containerized environments to perpetrate theft of proprietary facts and software.
“The attacker exploited a containerized workload and then leveraged it to accomplish privilege escalation into an AWS account in purchase to steal proprietary computer software and credentials,” Sysdig explained in a new report.
The superior cloud attack also entailed the deployment of crypto miner program, which the cybersecurity enterprise mentioned is either an endeavor to generate illicit gains or a ploy to distract defenders and throw them off the path.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The preliminary an infection vector banked on exploiting a susceptible general public-experiencing assistance in a self-managed Kubernetes cluster hosted on Amazon Web Expert services (AWS).
On attaining a thriving foothold, an XMRig crypto miner was launched and a bash script was utilized to acquire credentials that could be utilised to more burrow into the AWS cloud infrastructure and exfiltrate delicate info.
“Possibly crypto mining was the attacker’s preliminary target and the purpose adjusted as soon as they accessed the victim’s setting, or crypto mining was used as a decoy to evade the detection of information exfiltration,” the business stated.
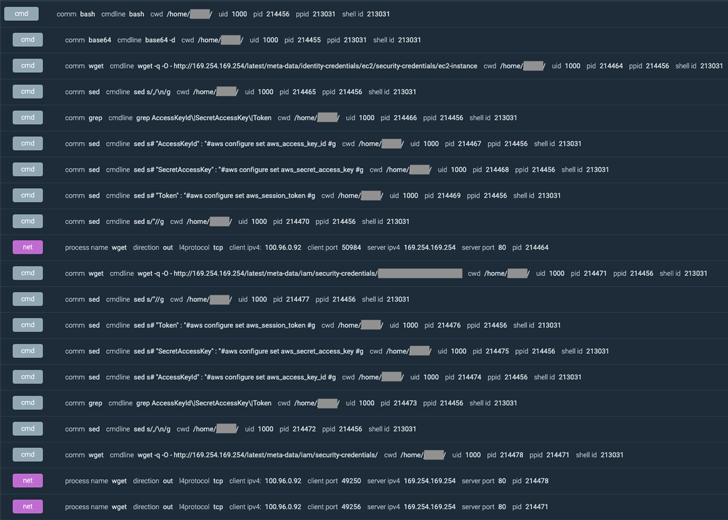
The intrusion notably also disabled CloudTrail logs to minimize the digital footprint, preventing Sysdig from accessing added proof. In all, it authorized the risk actor to entry additional than 1TB of data, which includes client scripts, troubleshooting tools, and logging documents.
“They also tried to pivot applying a Terraform condition file to other connected AWS accounts to distribute their access during the group,” the company reported. This, even so, proved to be unsuccessful because of to deficiency of permissions.
The results come months after Sysdig also specific one more cryptojacking marketing campaign mounted by the 8220 Gang concerning November 2022 and January 2023 concentrating on exploitable Apache web server and Oracle Weblogic applications.
Discovered this posting exciting? Observe us on Twitter and LinkedIn to read much more unique content we post.
Some components of this article are sourced from:
thehackernews.com

 WH Smith Discloses Cyber-Attack, Company Data Theft
WH Smith Discloses Cyber-Attack, Company Data Theft