Cybersecurity scientists have learned a new marketing campaign that’s exploiting a not too long ago disclosed security flaw in Fortinet FortiClient EMS devices to produce ScreenConnect and Metasploit Powerfun payloads.
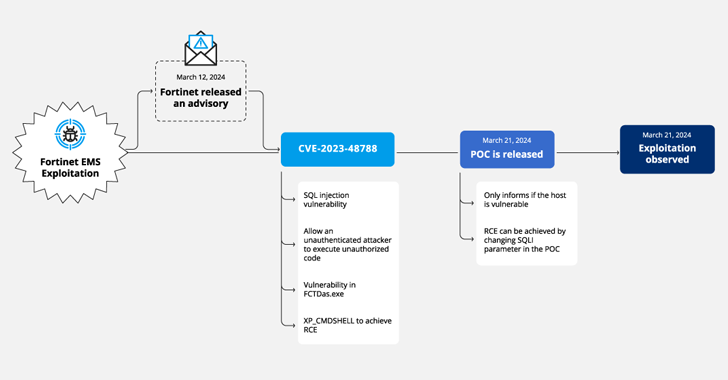
The exercise involves the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to execute unauthorized code or instructions through specifically crafted requests.
Cybersecurity agency Forescout is monitoring the marketing campaign under the codename Link:entertaining owing to the use of ScreenConnect and Powerfun for write-up-exploitation.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The intrusion targeted an unnamed media company that experienced its susceptible FortiClient EMS system exposed to the internet soon soon after the launch of a evidence-of-strategy (PoC) exploit for the flaw on March 21, 2024.
About the next pair of times, the unfamiliar adversary was observed leveraging the flaw to unsuccessfully download ScreenConnect and then set up the distant desktop computer software working with the msiexec utility.
However, on March 25, the PoC exploit was used to start PowerShell code that downloaded Metasploit’s Powerfun script and initiated a reverse connection to one more IP tackle.

Also detected were being SQL statements developed to obtain ScreenConnect from a distant area (“ursketz[.]com”) applying certutil, which was then mounted by means of msiexec just before developing connections with a command-and-command (C2) server.
There is evidence to recommend that the risk actor at the rear of it has been active considering the fact that at least 2022, exclusively singling out Fortinet appliances and making use of Vietnamese and German languages in their infrastructure.
“The noticed action clearly has a guide ingredient evidenced by all the unsuccessful attempts to download and set up tools, as perfectly as the relatively prolonged time taken between attempts,” security researcher Sai Molige claimed.

“This is evidence that this exercise is component of a precise marketing campaign, fairly than an exploit included in automated cybercriminal botnets. From our observations, it seems that the actors powering this marketing campaign are not mass scanning but choosing target environments that have VPN appliances.”
Forescout stated the attack shares tactical and infrastructure overlaps with other incidents documented by Palo Alto Networks Device 42 and Blumira in March 2024 that include the abuse of CVE-2023-48788 to down load ScreenConnect and Atera.
Businesses are advisable to utilize patches delivered by Fortinet to address potential threats, monitor for suspicious targeted traffic, and use a web application firewall (WAF) to block probably destructive requests.
Located this posting intriguing? Comply with us on Twitter and LinkedIn to go through extra unique written content we write-up.
Some parts of this report are sourced from:
thehackernews.com

 Cisco Warns of Global Surge in Brute-Force Attacks Targeting VPN and SSH Services
Cisco Warns of Global Surge in Brute-Force Attacks Targeting VPN and SSH Services