Threat actors have been observed leveraging a authentic but out-of-date WordPress plugin to surreptitiously backdoor sites as component of an ongoing marketing campaign, Sucuri uncovered in a report released previous 7 days.
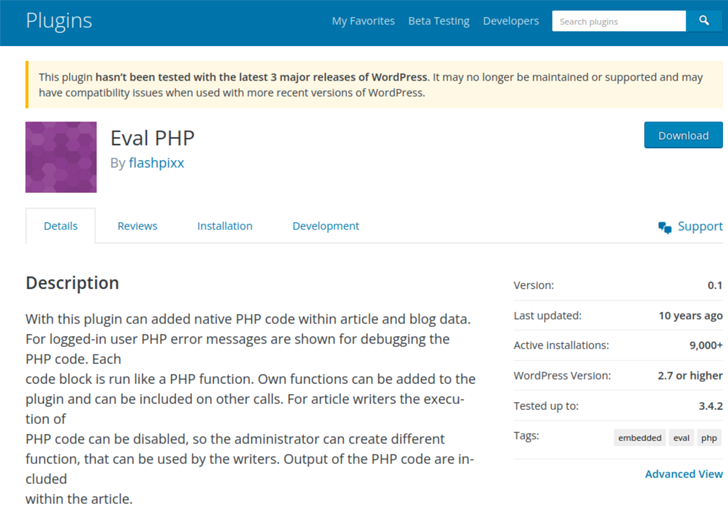
The plugin in problem is Eval PHP, produced by a developer named flashpixx. It allows customers to insert PHP code webpages and posts of WordPress web-sites which is then executed just about every time the posts are opened in a web browser.
While Eval PHP has in no way obtained an update in 11 years, stats collected by WordPress show that it truly is set up on about 8,000 sites, with the quantity of downloads skyrocketing from a person or two on regular due to the fact September 2022 to 6,988 on March 30, 2023.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
On April 23, 2023, by yourself, it was downloaded 2,140 instances. The plugin has racked up 23,110 downloads in excess of the earlier seven times.
GoDaddy-owned Sucuri mentioned it noticed some infected websites’ databases injected with malicious code into the “wp_posts” desk, which merchants a site’s posts, internet pages, and navigation menu data. The requests originate from these 3 IP addresses centered in Russia.
“This code is very basic: It works by using the file_set_contents functionality to produce a PHP script into the docroot of the web site with the specified remote code execution backdoor,” security researcher Ben Martin stated.
“While the injection in concern does fall a regular backdoor into the file structure, the mixture of a authentic plugin and a backdoor dropper in a WordPress put up will allow them to easily reinfect the web-site and keep hidden. All the attacker desires to do is to stop by 1 of the infected posts or webpages and the backdoor will be injected into the file structure.”
Sucuri explained it detected over 6,000 scenarios of this backdoor in the very last 6 months by yourself, describing the pattern of inserting the malware instantly into the database as a “new and fascinating improvement.”
The attack chain involves installing the Eval PHP plugin on compromised web sites and misusing it to create persistent backdoors across a number of posts that are in some cases also saved as drafts.
Future WEBINARZero Believe in + Deception: Discover How to Outsmart Attackers!
Uncover how Deception can detect superior threats, quit lateral movement, and increase your Zero Rely on approach. Join our insightful webinar!
Conserve My Seat!
“The way the Eval PHP plugin works it is really sufficient to save a site as a draft in buy to execute the PHP code within the [evalphp] shortcodes,” Martin spelled out, introducing the rogue internet pages are created with a true web site administrator as their writer, suggesting the attackers ended up able to successfully indication in as a privileged person.
The progress once all over again details to how destructive actors are experimenting with various procedures to preserve their foothold in compromised environments and evade server-facet scans and file integrity monitoring.
Website homeowners are recommended to protected the WP Admin dashboard as effectively as observe out for any suspicious logins to avert menace actors from attaining admin obtain and install the plugin.
Discovered this post intriguing? Stick to us on Twitter and LinkedIn to read through extra distinctive content we submit.
Some sections of this report are sourced from:
thehackernews.com


 Cloud Complexity Means Bugs Are Missed in Testing
Cloud Complexity Means Bugs Are Missed in Testing