Menace actors are taking gain of Android’s WebAPK technology to trick unsuspecting buyers into setting up malicious web apps on Android telephones that are created to capture sensitive own facts.
“The attack started with victims acquiring SMS messages suggesting the have to have to update a mobile banking software,” researchers from CSIRT KNF stated in an analysis produced last week. “The url contained in the message led to a internet site that utilized WebAPK technology to install a destructive application on the victim’s gadget.”
The application impersonates PKO Lender Polski, a multinational banking and money providers organization headquartered in Warsaw. Specifics of the campaign ended up first shared by Polish cybersecurity firm RIFFSEC.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
WebAPK makes it possible for customers to set up progressive web apps (PWAs) to their home display screen on Android gadgets with no obtaining to use the Google Enjoy Retail store.
“When a user installs a PWA from Google Chrome and a WebAPK is employed, the minting server “mints” (deals) and symptoms an APK for the PWA,” Google points out in its documentation.
“That procedure normally takes time, but when the APK is all set, the browser installs that app silently on the user’s device. Because trusted providers (Participate in Products and services or Samsung) signed the APK, the phone installs it with no disabling security, as with any application coming from the retail store. There is no need to have for sideloading the application.”
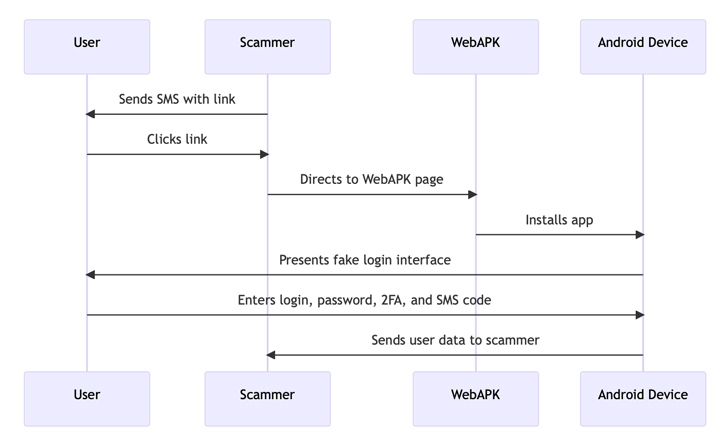
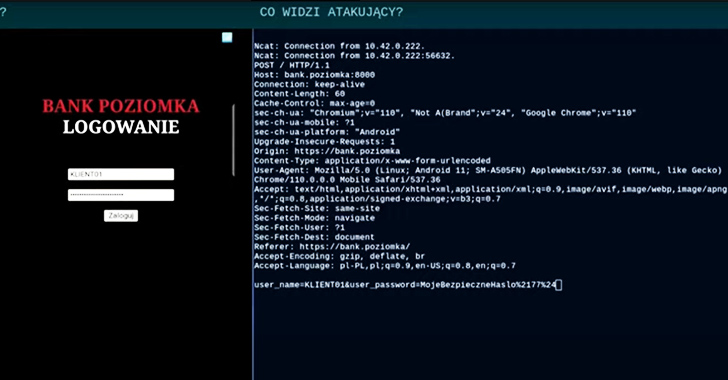
After put in, the pretend banking application (“org.chromium.webapk.a798467883c056fed_v2”) urges end users to enter their credentials and two-factor authentication (2FA) tokens, effectively resulting in their theft.
“Just one of the difficulties in countering this sort of attacks is the simple fact that WebAPK programs create diverse bundle names and checksums on each individual gadget,” CSIRT KNF said. “They are dynamically constructed by the Chrome engine, which would make the use of this knowledge as Indicators of Compromise (IoC) challenging.”
Approaching WEBINARShield Versus Insider Threats: Grasp SaaS Security Posture Administration
Fearful about insider threats? We’ve acquired you coated! Be part of this webinar to investigate functional methods and the tricks of proactive security with SaaS Security Posture Management.
Be a part of Now
To counter this sort of threats, it is suggested to block web sites that use the WebAPK mechanism to carry out phishing attacks.
The enhancement comes as Resecurity discovered that cybercriminals are progressively leveraging specialised system spoofing tools for Android that are marketed on the dark web in a bid to impersonate compromised account holders and bypass anti-fraud controls.
The antidetect instruments, such as Enclave Assistance and MacFly, are capable of spoofing cell unit fingerprints and other computer software and network parameters that are analyzed by anti-fraud units, with threat actors also leveraging weak fraud controls to conduct unauthorized transactions via smartphones making use of banking malware these types of as TimpDoor and Clientor.
“Cybercriminals use these equipment to access compromised accounts and impersonate respectable customers by exploiting stolen cookie information, impersonating hyper-granular product identifiers, and using fraud victims’ one of a kind network configurations,” the cybersecurity firm said.
Located this report attention-grabbing? Observe us on Twitter and LinkedIn to study a lot more exceptional information we post.
Some areas of this article are sourced from:
thehackernews.com

 These 6 Questions Will Help You Choose the Best Attack Surface Management Platform
These 6 Questions Will Help You Choose the Best Attack Surface Management Platform