Security vulnerabilities in remote desktop courses such as Sunlogin and AweSun are becoming exploited by threat actors to deploy the PlugX malware.
AhnLab Security Unexpected emergency Reaction Center (ASEC), in a new evaluation, explained it marks the ongoing abuse of the flaws to supply a selection of payloads on compromised techniques.
This includes the Sliver post-exploitation framework, XMRig cryptocurrency miner, Gh0st RAT, and Paradise ransomware. PlugX is the newest addition to this listing.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The modular malware has been thoroughly place to use by menace actors based in China, with new capabilities continuously additional to assistance perform technique manage and details theft.
In the attacks observed by ASEC, thriving exploitation of the flaws is adopted by the execution of a PowerShell command that retrieves an executable and a DLL file from a remote server.
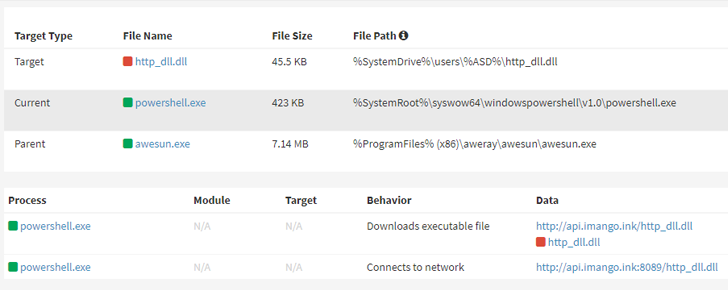
This executable is a genuine HTTP Server Services from cybersecurity business ESET, which is used to load the DLL file by means of a system known as DLL side-loading and in the end run the PlugX payload in memory.
“PlugX operators use a substantial wide variety of trusted binaries which are vulnerable to DLL Aspect-Loading, such as various anti-virus executables,” Security Joes noted in a September 2022 report. “This has been demonstrated to be productive when infecting victims.”
WEBINARDiscover the Concealed Potential risks of 3rd-Party SaaS Applications
Are you mindful of the risks affiliated with 3rd-party app access to your firm’s SaaS apps? Be a part of our webinar to learn about the types of permissions getting granted and how to lessen risk.
RESERVE YOUR SEAT
The backdoor is also noteworthy for its capacity to commence arbitrary providers, obtain and execute documents from an exterior source, and fall plugins that can harvest details and propagate applying Remote Desktop Protocol (RDP).
“New attributes are staying additional to [PlugX] even to this working day as it carries on to see continuous use in attacks,” ASEC mentioned. “When the backdoor, PlugX, is set up, menace actors can achieve regulate over the contaminated procedure devoid of the knowledge of the person.”
Located this report interesting? Comply with us on Twitter and LinkedIn to study more unique written content we write-up.
Some pieces of this write-up are sourced from:
thehackernews.com


 IceFire Ransomware Exploits IBM Aspera Faspex to Attack Linux-Powered Enterprise Networks
IceFire Ransomware Exploits IBM Aspera Faspex to Attack Linux-Powered Enterprise Networks