Risk actors are flooding the npm open up source offer repository with bogus packages that briefly even resulted in a denial-of-support (DoS) attack.
“The menace actors create destructive internet sites and publish vacant offers with links to all those destructive internet sites, having gain of open-supply ecosystems’ superior reputation on look for engines,” Checkmarx’s Jossef Harush Kadouri claimed in a report revealed previous week.
“The attacks induced a denial-of-support (DoS) that created NPM unstable with sporadic ‘Service Unavailable’ errors.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Whilst similar strategies have been lately observed propagating phishing links, the newest wave pushed the amount of deal variations to 1.42 million, a spectacular uptick from the approximate 800,000 offers produced on npm.
The attack technique leverages the fact that open up supply repositories are ranked larger on search engine outcomes to produce rogue web sites and add vacant npm modules with inbound links to those sites in the README.md information.
“Considering the fact that the open up resource ecosystems are highly reputed on research engines, any new open up-resource offers and their descriptions inherit this superior track record and come to be effectively-indexed on search engines, making them much more seen to unsuspecting users,” Harush Kadouri stated.
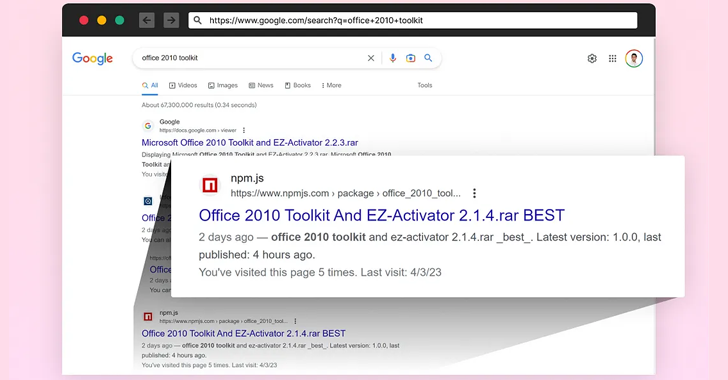
Specified that the complete approach is automated, the load established by publishing quite a few offers led to NPM intermittently going through stability issues in direction of the conclude of March 2023.
Checkmarx details out that in which there may perhaps be various actors driving the exercise, the end purpose is to infect the victim’s method with malware this sort of as RedLine Stealer, Glupteba, SmokeLoader, and cryptocurrency miners.
Approaching WEBINARLearn to Secure the Id Perimeter – Verified Strategies
Make improvements to your company security with our approaching expert-led cybersecurity webinar: Examine Id Perimeter strategies!
Do not Miss out on Out – Conserve Your Seat!
Other links choose people through a sequence of intermediate internet pages that in the end lead to authentic e-commerce web-sites like AliExpress with referral IDs, earning them a gain when the victim can make a purchase on the platform. A third group entails inviting Russian buyers to sign up for a Telegram channel that specializes in cryptocurrency.
“The struggle from danger actors poisoning our software package source chain ecosystem continues to be tough, as attackers continuously adapt and shock the field with new and unanticipated techniques,” Harush Kadouri reported.
To protect against these automatic campaigns, Checmarx has proposed npm to incorporate anti-bot methods throughout person account development.
Located this post interesting? Abide by us on Twitter and LinkedIn to examine additional special written content we post.
Some areas of this post are sourced from:
thehackernews.com


 Top 10 Cybersecurity Trends for 2023: From Zero Trust to Cyber Insurance
Top 10 Cybersecurity Trends for 2023: From Zero Trust to Cyber Insurance