Indian federal government entities and vitality providers have been specific by mysterious menace actors with an intention to produce a modified model of an open up-source information and facts stealer malware called HackBrowserData and exfiltrate sensitive facts in some instances by employing Slack as command-and-management (C2).
“The information and facts stealer was sent by using a phishing email, masquerading as an invitation letter from the Indian Air Drive,” EclecticIQ researcher Arda Büyükkaya mentioned in a report posted nowadays.
“The attacker utilized Slack channels as exfiltration points to add private interior documents, private email messages, and cached web browser facts just after the malware’s execution.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The marketing campaign, observed by the Dutch cybersecurity agency beginning March 7, 2024, has been codenamed Procedure FlightNight in reference to the Slack channels operated by the adversary.

Targets of the malicious exercise span multiple govt entities in India, counting individuals linked to electronic communications, IT governance, and national defense.
The threat actor is reported to have properly compromised personal power companies, harvesting financial files, particular aspects of personnel, information about drilling things to do in oil and gas. In all, about 8.81 GB of details has been exfiltrated more than the system of the marketing campaign.
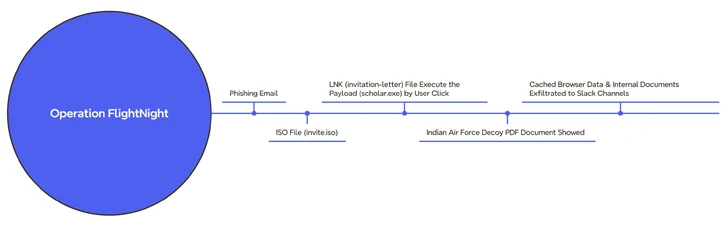
The attack chain starts off with a phishing information that contains an ISO file (“invite.iso”), which, in switch, incorporates a Windows shortcut (LNK) that triggers the execution of a hidden binary (“scholar.exe”) existing within the mounted optical disk graphic.
Concurrently, a entice PDF file that purports to be an invitation letter from the Indian Air Power is shown to the victim whilst the malware clandestinely harvests documents and cached web browser details and transmits them to an actor-controlled Slack channel named FlightNight.
The malware is an altered edition of HackBrowserData that goes further than its browser knowledge theft characteristics to incorporate abilities to siphon documents (Microsoft Business, PDFs, and SQL databases information), communicate more than Slack, and far better evade detection utilizing obfuscation techniques.

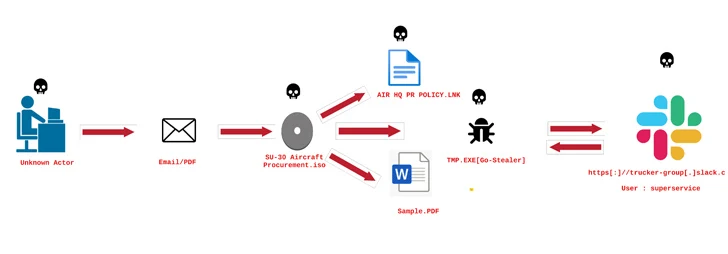
It truly is suspected that the danger actor stole the decoy PDF during a former intrusion, with behavioral similarities traced back again to a phishing campaign concentrating on the Indian Air Drive with a Go-primarily based stealer known as GoStealer.
Facts of the action have been disclosed by an Indian security researcher who goes by the alias xelemental (@ElementalX2) in mid-January 2024.
The GoStealer infection sequence is almost similar to that FlightNight, employing procurement-themed lures (“SU-30 Aircraft Procurement.iso”) to screen a decoy file though the stealer payload is deployed to exfiltrate information of fascination more than Slack.
By adapting freely offered offensive equipment and repurposing legitimate infrastructure these types of as Slack which is widespread in company environments, it lets menace actors to minimize time and enhancement costs, as perfectly as effortlessly fly underneath the radar.
 Impression resource: ElementalX2
Impression resource: ElementalX2
The effectiveness added benefits also indicate that it is really that a great deal easier to start a qualified attack, even letting a lot less-experienced and aspiring cybercriminals to spring into motion and inflict considerable injury to companies.
“Operation FlightNight and the GoStealer campaign highlight a easy nevertheless successful solution by threat actors to use open-source instruments for cyber espionage,” Büyükkaya stated.
“This underscores the evolving landscape of cyber threats, whereby actors abuse greatly utilised open up-supply offensive tools and platforms to reach their aims with nominal risk of detection and expenditure.”
Uncovered this article exciting? Adhere to us on Twitter and LinkedIn to examine a lot more unique content we article.
Some elements of this short article are sourced from:
thehackernews.com


 CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability
CISA Warns: Hackers Actively Attacking Microsoft SharePoint Vulnerability