Platform certificates employed by Android smartphone sellers like Samsung, LG, and MediaTek have been located to be abused to sign destructive apps.
The findings were to start with identified and reported by Google reverse engineer Łukasz Siewierski on Thursday.
“A system certification is the software signing certificate used to signal the ‘android’ application on the technique picture,” a report filed via the Android Partner Vulnerability Initiative (AVPI) reads.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The ‘android’ software operates with a remarkably privileged user id – android.uid.process – and retains method permissions, such as permissions to accessibility person data.”

This effectively suggests that a rogue application signed with the exact certificate can obtain the best amount of privileges as the Android functioning system, permitting it to harvest all types of sensitive information from a compromised machine.
The checklist of malicious Android app deals that have abused the certificates is down below –
- com.russian.signato.renewis
- com.sledsdffsjkh.Lookup
- com.android.power
- com.management.propaganda
- com.sec.android.musicplayer
- com.houla.quicken
- com.attd.da
- com.arlo.fappx
- com.metasploit.phase
- com.vantage.ectronic.cornmuni
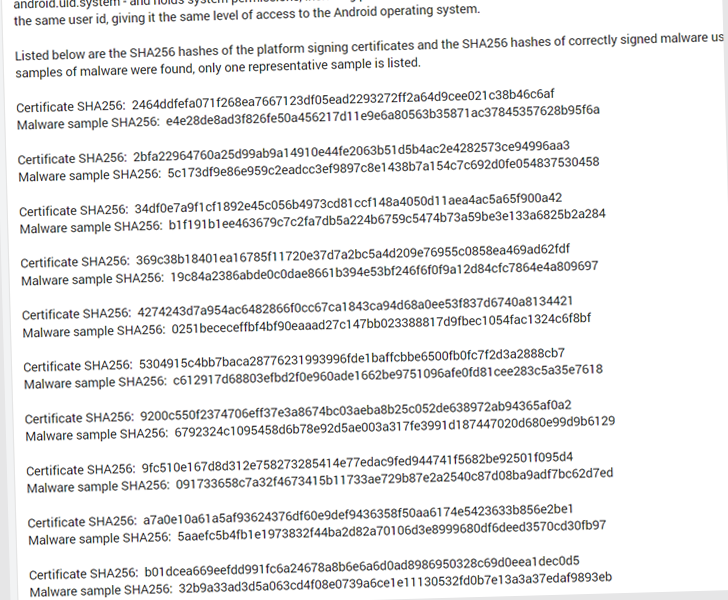
That said, it can be not instantly clear how and the place these artifacts have been located, and if they were utilized as element of any energetic malware marketing campaign.
A search on VirusTotal shows that the determined samples have been flagged by antivirus options as HiddenAds adware, Metasploit, info stealers, downloaders, and other obfuscated malware.
When reached for comment, Google mentioned it educated all impacted vendors to rotate the certificates and that there’s no proof these apps ended up sent by means of the Engage in Retail store.
“OEM companions promptly carried out mitigation steps as shortly as we described the important compromise,” the organization told The Hacker Information in a statement. “Conclusion people will be guarded by consumer mitigations executed by OEM companions.”
“Google has carried out wide detections for the malware in Construct Check Suite, which scans method images. Google Participate in Safeguard also detects the malware. There is no sign that this malware is or was on the Google Participate in Retailer. As always, we recommend users to guarantee they are operating the newest edition of Android.”
Found this post attention-grabbing? Stick to us on Twitter and LinkedIn to study more special articles we write-up.
Some elements of this post are sourced from:
thehackernews.com


 CISA Warns of Multiple Critical Vulnerabilities Affecting Mitsubishi Electric PLCs
CISA Warns of Multiple Critical Vulnerabilities Affecting Mitsubishi Electric PLCs