A new spam email campaign has emerged as a conduit for a previously undocumented malware loader that allows the attackers to gain an first foothold into company networks and fall malicious payloads on compromised devices.
“These bacterial infections are also utilized to aid the shipping of additional malware these kinds of as Qakbot and Cobalt Strike, two of the most popular threats on a regular basis noticed focusing on corporations all over the planet,” stated scientists with Cisco Talos in a complex write-up.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The malspam marketing campaign is thought to have commenced in mid-September 2021 through laced Microsoft Office paperwork that, when opened, triggers an infection chain that qualified prospects to the equipment getting contaminated with a malware dubbed SQUIRRELWAFFLE.
Mirroring a system that’s reliable with other phishing attacks of this sort, the most up-to-date procedure leverages stolen email threads to give it a veil of legitimacy and trick unsuspecting users into opening the attachments.
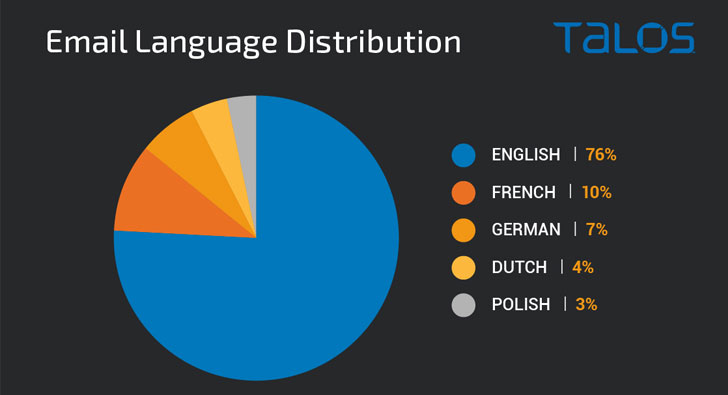
What is actually far more, the language utilized in the reply messages matches the language utilised in the primary email thread, demonstrating a scenario of dynamic localization set in position to increase the chance of success of the campaign. The top rated five languages used to deliver the loader are English (76%), adopted by French (10%), German (7%), Dutch (4%), and Polish (3%).
Email distribution volumes capitalizing on the new threat peaked about September 26, based on facts compiled by the cybersecurity organization.
Although previously compromised web servers, generally managing variations of the WordPress content material administration system (CMS), function as the malware distribution infrastructure, an interesting technique observed is the use of “antibot” scripts to block web requests that originate from IP addresses not belonging to victims but instead automatic investigation platforms and security exploration businesses.
The malware loader, other than deploying Qakbot and the notorious penetration screening instrument Cobalt Strike on the contaminated endpoints, also establishes communications with a remote attacker-controlled server to retrieve secondary payloads, building it a powerful multi-reason utility.
“Immediately after the Emotet botnet takedown earlier this 12 months, criminal threat actors are filling that void,” Zscaler famous in an assessment of the very same malware last month. “SQUIRRELWAFFLE seems to be a new loader having advantage of this gap. It is not but apparent if SQUIRRELWAFFLE is produced and distributed by a recognised threat actor or a new group. Even so, very similar distribution approaches have been formerly applied by Emotet.”
Uncovered this write-up intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to examine a lot more distinctive content material we submit.
Some areas of this report are sourced from:
thehackernews.com


![[ebook] the guide to centralized log management for lean it](https://thecybersecurity.news/data/2021/10/eBook-The-Guide-to-Centralized-Log-Management-for-Lean-IT-80x80.jpg) [eBook] The Guide to Centralized Log Management for Lean IT Security Teams
[eBook] The Guide to Centralized Log Management for Lean IT Security Teams