Human beings are intricate beings with consciousness, feelings, and the capacity to act based mostly on feelings. In the at any time-evolving realm of cybersecurity, humans regularly keep on being key targets for attackers. About the yrs, these attackers have made their know-how in exploiting various human traits, sharpening their expertise to manipulate biases and emotional triggers with the objective of influencing human behaviour to compromise security regardless of whether it be private and organisational security.
More than just a ‘human factor’
Comprehending what defines our humanity, recognizing how our qualities can be perceived as vulnerabilities, and comprehending how our minds can be focused provide the foundation for determining and responding when we inevitably grow to be the concentrate on.
The human thoughts is a complicated landscape that progressed over years of exposure to the natural surroundings, interactions with other folks, and lessons drawn from previous ordeals.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
As human beings, our minds set us aside, marked by a multitude of attributes and feelings, typically too complicated to articulate precisely.
Human behaviour is complex
Some of our elementary qualities can be outlined as follows:
- Believe in – Individuals location their believe in in other people, assuming inherent goodness.
- Empathy – Individuals show care for some others and their thoughts.
- Ego – Individuals harbour a competitive spirit, aspiring to outshine their friends.
- Guilt – Human beings expertise remorse for their steps, specially when they harm other people.
- Greed – Human beings motivation belongings and may perhaps succumb to impulsivity.
- Urgency – People answer immediately to scenarios demanding quick consideration.
- Vulnerability – Individuals frequently grapple with concern and are candid about their emotions.
Although this listing is not exhaustive, it summarises widespread and comprehensible areas that push human conduct. Human interactions hold necessary benefit, instilling everyday living with importance and advancing cultural norms. However, for attackers trying to find to exploit us, the social build of human-to-human interactions delivers a pathway for manipulation.
Our by natural means social mother nature forces us to revert to these characteristics. Emotions provide as a safety net for interaction, issue-resolving, and connections in our daily lifestyle and we have come to have confidence in our emotional responses to even more guideline and safeguard us in a assortment of scenarios.
I consider, thus I can be manipulated
Attackers exploit this security net (thoughts and elementary traits) when concentrating on humans, as it can be manipulated to fulfil their aims. This basic safety net weakens even more when we venture into the “online” realm, as selected safeguards fall short owing to a lack of insight. The abstraction of communication via a identify on monitor often misleads our minds in deciphering cases in a way that our emotions simply cannot correctly navigate.
In the realm of manipulation, a variety of versions and procedures have been employed more than centuries to affect human conduct. In today’s context, attackers exploit these products to recognize human vulnerabilities, characterised as weaknesses within the process that can be exploited.
In addition to immediately manipulating essential features by very carefully focused attacks, attackers are inclined to goal people by way of forms of affect and persuasion. These can be summarised as follows, and people are likely to work mentally in these realms:
- Reciprocation – People truly feel compelled to reciprocate what they have acquired.
- Authority – People are inclined to comply with authoritative/known figures.
- Shortage – Human beings want items that are much less attainable.
- Commitment & Regularity – Humans favour plan and framework.
- Liking – People kind psychological connections.
- Social Proof – Humans request validation and fame.
These elements can be seen as possible vulnerabilities in the human brain when put together with feelings and basic attributes. Attackers leverage these areas to achieve immediate command above our steps, an occurrence now recognised as social engineering. Social engineering encompasses many tactics and strategies, nonetheless at its core, it exploits just one or more of the areas talked about above by way of properly crafted interactions.
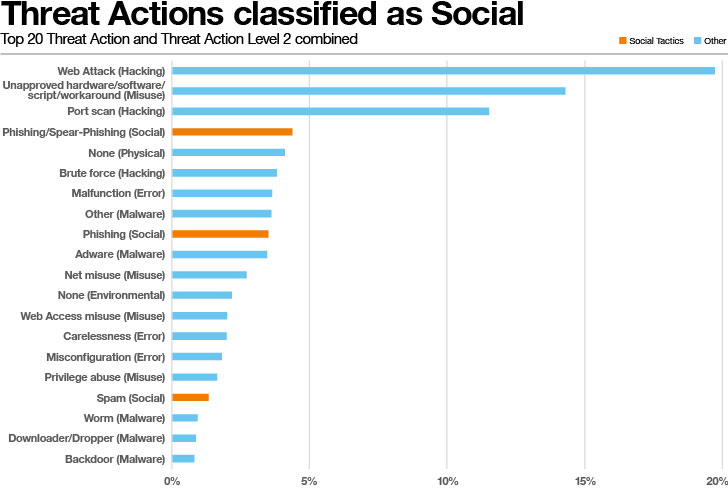
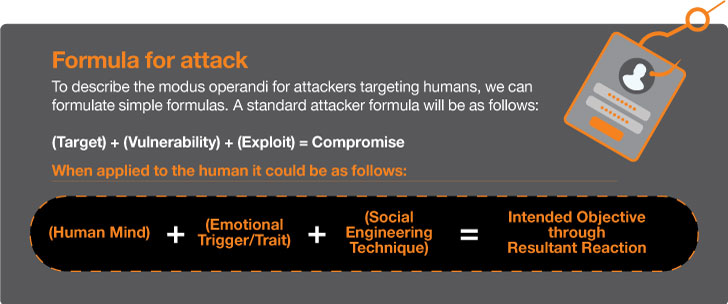

Exploitation tactics, typically noticed in electronic channels like email, phone calls, or text messages, are frequently utilised for phishing. These techniques manipulate proven interactions to realize several goals, this sort of as deceiving persons into parting with money, opening destructive files, distributing qualifications, or revealing sensitive data. The consequences of these attacks can vary from personal losses to organizational breaches.
Defending ourselves
To safeguard in opposition to these attacks towards our minds, we ought to align our cognitive standards with psychological triggers by asking issues like what is the purpose, expectation, and legitimacy of the interaction. These issues could stop impulsive reactions and let introspection.
Creating a “cease and evaluate” mentality functions as a psychological firewall, strengthened by vigilance, to increase particular and organisational security. By considering prospective attacks, we heighten our recognition of vulnerabilities and operate on resilience. This recognition, coupled with a proactive solution, can help mitigate threats to our minds and humanity, promoting collaboration to disarm attackers and weaken their functions.
Remain vigilant, stay educated, and carry on to query every little thing.
This is just 1 of the stories found in the Security Navigator. Other fascinating study like a study of Hacktivism and an analysis of the surge in Cyber Extortion (as properly as a ton of other interesting study matters) can be observed there as nicely. It is really free of charge of charge, so have a appear. It is truly worth it!
Notice: This report was expertly published by Ulrich Swart, Education Manager & Technological Staff Chief at Orange Cyberdefense.
Identified this posting attention-grabbing? Follow us on Twitter and LinkedIn to read through a lot more unique content we publish.
Some areas of this posting are sourced from:
thehackernews.com

 Building a Robust Threat Intelligence with Wazuh
Building a Robust Threat Intelligence with Wazuh