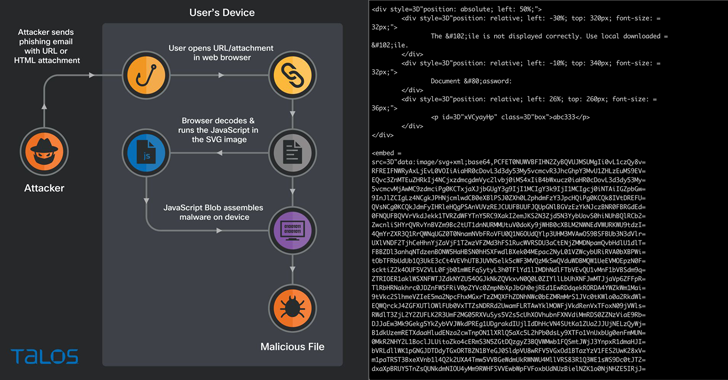
Phishing strategies involving the Qakbot malware are working with Scalable Vector Graphics (SVG) photographs embedded in HTML email attachments.
The new distribution method was noticed by Cisco Talos, which mentioned it discovered fraudulent email messages featuring HTML attachments with encoded SVG illustrations or photos that incorporate HTML script tags.
HTML smuggling is a system that relies on working with reputable capabilities of HTML and JavaScript to run encoded destructive code contained in just the entice attachment and assemble the payload on a victim’s device as opposed to producing an HTTP request to fetch the malware from a remote server.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

In other phrases, the concept is to evade email gateways by storing a binary in the sort of a JavaScript code that’s decoded and downloaded when opened by using a web browser.
The attack chain spotted by the cybersecurity enterprise issues a JavaScript that’s smuggled inside of the SVG image and executed when the unsuspecting email receiver launches the HTML attachment.

“When the target opens the HTML attachment from the email, the smuggled JavaScript code inside the SVG impression springs into motion, producing a malicious ZIP archive and then presenting the user with a dialog box to conserve the file,” researchers Adam Katz and Jaeson Schultz mentioned.
The ZIP archive is also password-protected, demanding end users to enter a password which is shown in the HTML attachment, next which an ISO graphic is extracted to run the Qakbot trojan.
The locating comes as recent investigation from Trustwave SpiderLabs reveals that HTML smuggling attacks are a frequent incidence, with .HTML (11.39%) and .HTM (2.7%) data files accounting for the next most spammed file attachment style soon after .JPG photos (25.29%) in September 2022.
“Possessing strong endpoint defense can reduce execution of possibly obfuscated scripts, and avert scripts from launching downloaded executable material,” the scientists stated.
“HTML smuggling’s means to bypass articles scanning filters usually means that this technique will almost certainly be adopted by a lot more risk actors and employed with escalating frequency.”MS Drivers –
concentrating on the identical sectors due to the fact June 2022 with the aim of penetrating cell networks to offer SIM swapping solutions. ->
targeting the exact verticals considering that June 2022, with some of the attacks penetrating cell provider networks to deliver SIM swapping services.
Located this short article intriguing? Observe us on Twitter and LinkedIn to browse far more exceptional content we publish.
Some sections of this write-up are sourced from:
thehackernews.com

 Signed Microsoft Drivers Used in Attacks Against Businesses
Signed Microsoft Drivers Used in Attacks Against Businesses