In the midst of ‘The Fantastic Resignation,’ the injury from workers (or contractors) leaving an group may possibly be just one of the biggest risks going through IT teams right now. The actuality is that in the occupied business computing atmosphere, consumer onboarding and offboarding is a actuality of day by day everyday living.
When employee counts variety into the five-figure territory — and complete networks of contractors have to be accounted for as effectively — it is really easy to eliminate observe of who’s, literally, coming and going. Frequently, there are “offboarding” actions that are overlooked about — disabling or eliminating the person from Lively Listing or IAM is not adequate as the user may perhaps have community qualifications on some of the SaaS platforms or other sensitive devices.
Technically talking, there are techniques to automate offboarding using protocols such as SCIM and JIT mapping nonetheless, it necessitates a higher amount of maturity in an IT surroundings and the workers to employ it.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
For organizations not applying SCIM or JIT, offboarded employees may possibly even now have regional credentials on some of their often used SaaS platforms or other sensitive devices. Leaving these users’ entry in position exposes corporations to unauthorized data access.
When it will come to getting old end users off units – deprovisioning – there are a number of best procedures that should be borne in thoughts and adopted.
Very best Methods in Deprovisioning
Hold an Stock — It is vital that IT groups hold an up-to-date report, at all occasions, of all users with obtain to business systems. A channel of communication with human resources need to be founded for trying to keep abreast of functions impacting the user inventory these kinds of as personnel terminations. To be helpful from a security standpoint, these programs want to be capable of scrutinizing both internal and external users. The vendor landscape can be regularly shifting.
Normally be on the lookout — In addition to preserving track of intended system customers, IT teams will need to have a capability for consumer discovery that accounts for the comprehensive breadth of techniques they may well be accessing – both those people in legacy environments, like on-premises techniques, and in the mushrooming cloud environment.
Demanding obtain management — It is really essential that IT groups establish onboarding and offboarding protocols that account for the whole extent of privileged personnel computing obtain. If an worker has accessibility to 3 interior techniques and 30 cloud-hosted types, then evidently restricting obtain to all those on-premises will go away a gaping data gap that they will retain accessibility to.
How to Automate the Deprovisioning Method
The meticulous mapping and security work that this course of action calls for from a security team is huge. A SaaS Security Posture Administration option, like Adaptive Protect, can streamline this system — a easy question in Adaptive Shield’s person inventory can expose the consumer posture of the deprovisioned users’ accounts across the entire SaaS stack.
When it arrives to deprovisioning these accounts, orchestration instruments give security groups an easy way to integrate Adaptive Shield’s abilities into an automated deprovisioning workflow. This vastly simplifies the approach, lowering the quantity of time it takes to fully deprovision buyers, and guaranteeing that no accounts are left energetic.
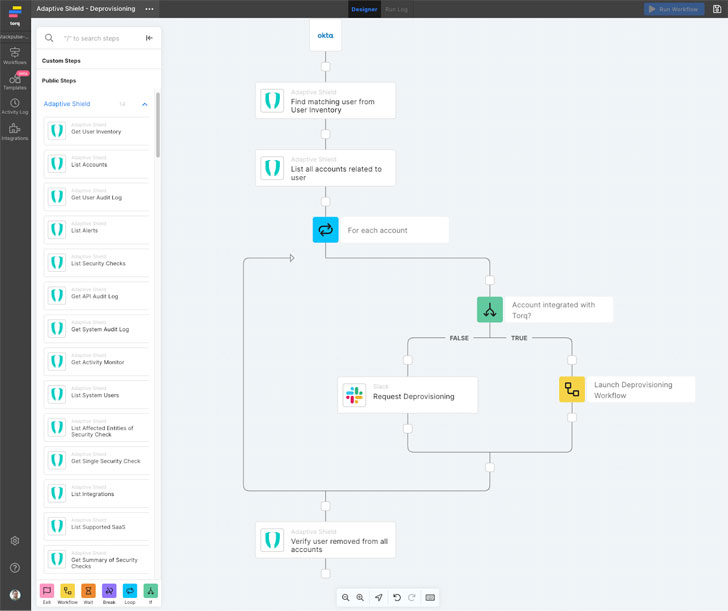
In the figure over, you can can see a opportunity workflow the place:
- The initial IAM deprovisioning can be utilised as the hook to notify Adaptive Protect that a deprovisioning event has transpired.
- Adaptive Defend can probe the organization’s built-in SaaS landscape for information for that person,
- When Adaptive Shield detects an energetic account, it triggers a workflow in the automation resource that identifies the account, and deactivates it.
- If the account are not able to be specifically deactivated, it sends a information by using Slack to an administrator, asking them to verify the deactivation.
- The automation instrument then re-runs the security check out in Adaptive Defend, to validate account deactivation.
This workflow is just just one illustration of how Adaptive Shield’s integration with an orchestration software streamlines the deprovisioning procedure through automation not only to relieve the stress of guide auditing and deactivating accounts, but also giving continuous visibility and control increasing the organization’s SaaS security posture.
Discover additional about how to automate deprovisioning for your firm.
Located this report exciting? Observe THN on Fb, Twitter and LinkedIn to go through much more special material we submit.
Some areas of this posting are sourced from:
thehackernews.com

 Singapore to launch digital defence agency to counter growing cyber threats
Singapore to launch digital defence agency to counter growing cyber threats