Malware evaluation is an crucial portion of security researcher’s work. But working with destructive samples can be dangerous — it demands specialized tools to history their exercise, and a safe environment to avert unintended hurt.
Having said that, manual lab setup and configuration can show to be a laborious and time-consuming process.
In this write-up, we will glimpse at 4 techniques to create a reverse engineering lab, discuss how to help save time, and, probably, boost the detection charge applying a cloud assistance, and a advisable list of resources for a detailed set up.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
What is a malware evaluation lab?
In essence, a malware analysis lab offers a risk-free, isolated house for examining malware.
The setup can vary from a straightforward virtual equipment applying VirtualBox to a extra intricate network of interconnected devices and genuine networking hardware.
But in this posting, we are going to appear at constructing a lab personalized for static assessment, so what we will require is a safe surroundings wherever we can operate disassemblers, edit binary files and debug.
There are a couple of ways we can go about creating it:
1 — Virtualization
Probably the easiest way to produce a safe and isolated ecosystem is by making use of a digital device.
A well known solution is Digital Box, open up-source software package from Oracle. If you are on Linux, to set up it, just use the command sudo apt set up virtualbox. VMWare is another well-known choice — it is really a business software, but there is a absolutely free tier.
Established up is effortless — obtain and set up the software, produce a digital machine, configure the configurations to make certain it would not have network accessibility or shared folders with the host, and then boot it with an .ISO file of your chosen functioning program.
But this approach has some negatives: you will have to set up customized detection regulations for figuring out suspicious or destructive entities, independently investigation emerging procedures, sustain configurations, and ascertain logging policies using available applications. This increased emphasis on routine maintenance and configuration detracts from the time spent on evaluation.
Professionals
- Free or available at a reduced value
- The setup is effortless
- Delivers an isolated setting if configured the right way
Cons
- The performance requires a hit
- Minimal scalability bottlenecked by your CPU
- The malware could escape to the host
- Calls for to manually configure detection procedures
2 — Focused hardware
In situation you have an outdated laptop lying close to or you have the usually means to get one or establish a Personal computer, this is absolutely an possibility. You don’t have to break the lender possibly — the 11-13th technology of Intel processors make even spending plan devices far more than a feasible selection.
The major upside of opting for a actual physical laptop or computer is greater performance and better security because you can make positive the machine is actually isolated from all units and networks.
Professionals:
- Most performant alternative
- Wholly isolated natural environment
- Can be endlessly custom made
Drawbacks:
- Higher-close components is pricey
- Demands computer software and hardware routine maintenance
- Desires to be configured to get the job done
3 — A cloud lab
Building a malware lab in the cloud basically is not as tough as it may audio. Also — it is totally free! All you want is an account at AWS, or any comparable cloud company supplier, and a machine to link to it. The setup may possibly be marginally much more intricate than a neighborhood digital device, but there are numerous tutorials that you can use as a guidebook.
If you choose to do the job with AWSs, search for Kali in the marketplace to established up a Kali Linux Digital Device. To use the GUI, you can make a VNC server and link to your lab with a tool like VNC Viewer.
One particular of the downsides of this tactic is that it’s free until finally it isn’t. If you exceed the boundaries of the absolutely free tier, your cloud bill could balloon quickly.
At times, cloud providers may well also prohibit malware execution, posing lawful pitfalls. Also, cloud machines demand from customers aid, burdening IT functions. Whilst suitable for beginner impartial scientists, this technique offers downsides in company configurations. Crucially, it lacks the capacity to counteract malware’s VM detection and bypass anti-evasion strategies.
Pros:
- Scalability
- No components routine maintenance
- Isolated from your network for much better security
Negatives:
- Opportunity lawful risks.
- Complicated setup
- Requires to be configured to do the job
- Latency decreases the excellent of perform
- Highly developed setups are dear
- Inclined to anti-avastin procedures
4 — Sandbox-as-a-Support
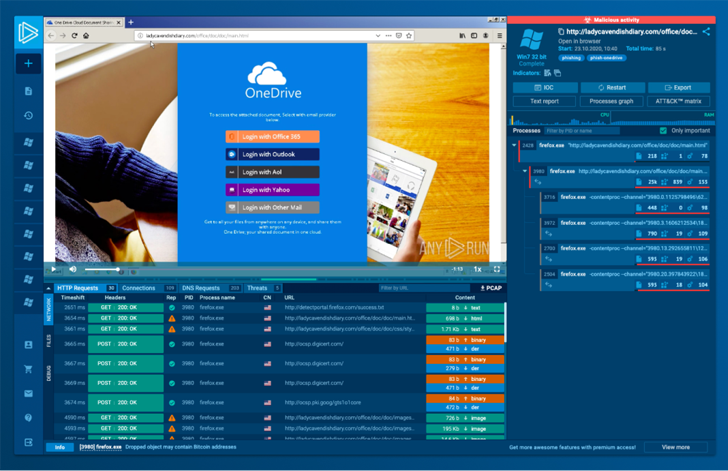
Just one significant edge of cloud-dependent sandbox providers is their crafted-in resilience from VM detection. This reduces the chance of a malware sample recognizing it truly is in a virtual device and halting its execution, a element that necessitates handbook configuration in other sandboxes.
Also, in a service like this, detection regulations are composed by experts utilizing wide malware and menace intel databases. As a end result, the software package can enrich investigation results with tactics and IOCs, yielding more detailed output when compared to uncooked details from cloud or on-prem VMs.
In addition, cloud-dependent sandbox services streamline natural environment configurations. For occasion, in its place of creating separate snapshots in a VM, ANY.RUN’s cloud assistance makes it possible for straightforward atmosphere set up by a user-friendly menu each and every time a lab is initiated.
Pros
- Saves time
- Simplicity of use
- Secure and fully isolated from your network
- Hardened against VM detection
- Straightforward configuration of the execution setting
Cons
- Isn’t optimized to work with your toolset
- Selected alternatives on the sector may be laggy
- Digital machine occasions are time-constrained
Employing an on line, interactive sandbox this kind of as ANY.Operate as an alternative of a lab gives benefit and velocity. It can assist automate sections of static evaluation, like extracting malware configurations.
If you would like to try out ANY.Operate for you, they are currently working a specific promo for Hacker Information visitors:

Types of application for reverse engineering
Here are some vital applications that will help to you reverse-engineer malware:
- Disassemblers. Disassemblers are a should-have for reverse engineering. They enable you to completely transform equipment language into assembly code which is uncomplicated for people to fully grasp, so you can obtain perception into how malware features. IDA Pro, Ghidra, and Binary Ninja are all preferred disassemblers. To operate Ghidra on Linux, very first, put in JDK and down load Ghidra alone to your machine. No installation is needed, just execute these commands inside of the Ghidra listing: chmod +x ghirdRun and ./ghirdaRun.
- Decompilers. Decompilers are very similar to disassemblers, in that they can change device code into source code. It can be helpful for being familiar with the malware’s architecture and figuring out distinct functions or modules. Well-liked decompilers include IDA Pro, Ghidra, and Hex-Rays.
- Debuggers. Debuggers support programmers find faults and troubleshoot them by allowing them go by means of the code line by line, set breakpoints, and observe the way the malware capabilities. A number of of the most generally utilised debuggers are OllyDbg, x64dbg, and WinDbg. x64dbg is a person of the most well known possibilities right now: it really is totally free and readily available to obtain from x64dbg.com
- HEX editors. Hex editors are helpful for having a closer seem at binary files, knowing how they’re arranged, spotting specific values, and manipulating the file as a way of observing how the virus responds. Frequent hex editors include HxD and Hex Workshop.
- Network examination equipment. Sure malware requires an on the net link in buy to function. Network assessment systems like Wireshark can assist you establish and study the targeted visitors sent and gained by that malware.
Critical malware assessment applications
It is really up to the analyst to make a decision what computer software to set up, but, in our viewpoint, the list of vital applications seems like this:
- Detect It Uncomplicated. For figuring out forms of documents
- Procedure Hacker. Helps you keep track of method assets, debug software program and detect malware
- Course of action Observe. A Checking resource for Windows that shows authentic-time file system, Registry, and course of action/thread action
- Wireshark. For analyzing network activity
- x64dbg and Ghidra. Essential for both equally static and dynamic investigation.
Oh, and if you want to get a lab that is been pre-configured, you can use a specialized distribution package like Remnux, which will come with most of individuals systems now installed.
There is also FLARE VM — a selection of program installation scripts for Windows-centered systems that allows you to quickly set up and manage a reverse engineering atmosphere on a digital machine.
Wrapping up
We have talked over 4 unique approaches for building an assessment lab: employing virtualization, creating a dedicated equipment, deploying a cloud lab, or subscribing to a sandbox-as-a-service.
Just about every of these methods comes with its very own set of positive aspects and negatives, and the right preference is dependent on what you are trying to accomplish and the assets readily available to you.
Thankfully, most of these selections are completely totally free, so just test them all out and see what functions ideal!
Discovered this write-up exciting? Observe us on Twitter and LinkedIn to examine additional special articles we post.
Some components of this short article are sourced from:
thehackernews.com


 Multi-cloud ‘over-permissioning’ causing cyber risk headaches for businesses
Multi-cloud ‘over-permissioning’ causing cyber risk headaches for businesses