Just about every Google Workspace administrator understands how promptly Google Drive results in being a messy sprawl of loosely shared private facts. This isn’t anyone’s fault it is inevitable as your productiveness suite is purposefully built to allow genuine-time collaboration – both of those internally and externally.
For Security & Risk Management teams, the untenable risk of any Google Push footprint lies in the harmful combinations of sensitive info, excessive permissions, and poor sharing. Even so, it can be difficult to differentiate concerning typical business enterprise procedures and possible threats with no totally comprehension the context and intent.
Materials Security, a business renowned for its impressive process of defending delicate information inside of personnel mailboxes, has recently released Details Security for Google Drive to safeguard the sprawl of confidential details scattered in the course of Google Push with a powerful discovery and remediation toolkit.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
How Substance Security can help organizations safeguard Google Travel
Seeking to answer fundamental concerns about what’s in Google Generate and in which it’s shared is painstakingly guide utilizing the Workspace admin dashboard, and performing with the Push API is pricey and intricate. Specified the breadth of delicate articles, this is an place that warrants emphasis, but it really is tough to get to the depth needed.
Content is backed by a strong facts system that syncs with your Google Workspace tenant to establish out a structured model of historic file contents, metadata, permissions, and sharing options that is retained up-to-date based on ongoing activity. This facts platform allows in-depth inspection that would not be possible by interfacing with the Push API alone. With this knowledge platform as the foundation, Content:
- Scans file contents in opposition to a established of tailor made built ML-based detection policies to identify and classify delicate articles throughout a huge selection of PII, PCI, PHI, and other confidential data groups
- Calculates file and folder permission sets and sharing options to create a unified access design that is a lot easier to comprehend and reveal for compliance
- Permits automatic obtain revocation primarily based on specific look for final results and activity triggers to repeatedly cut down the risk profile
The precision of Product enables you to correctly wrangle this kind of a elaborate and extensive info repository with out getting in the way of everyday use – security without the need of impacting efficiency. See it for yourself.
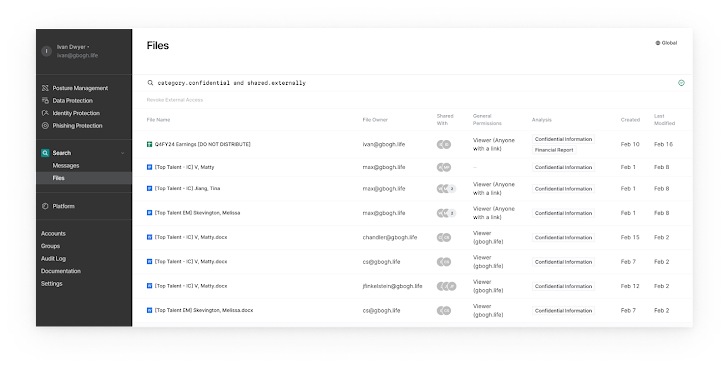
Illuminate blind spots across your Google Drive footprint
With a impressive details platform as the basis, you gain an expressive search interface that guides you by way of your Google Push footprint to establish harmful mixtures worthy of investigation. You can look for towards file metadata, ownership, written content, place, and sharing to reply queries this kind of as:
- Show me just about every file that incorporates economical data that are shared externally
- Demonstrate me each file viewable through a community website link that contains PII
- Clearly show me every single file accessible by these users who are departing the business future 7 days
- Show me every file with confidential data which is shared with a gmail handle
- Clearly show me each file in a Shared Generate that includes wellbeing documents
As you illuminate a lot more of these unsafe blind places, you continuously gain a far more comprehensive watch of the natural environment with heightened security posture – the varieties of things that make it much easier to snooze at evening.
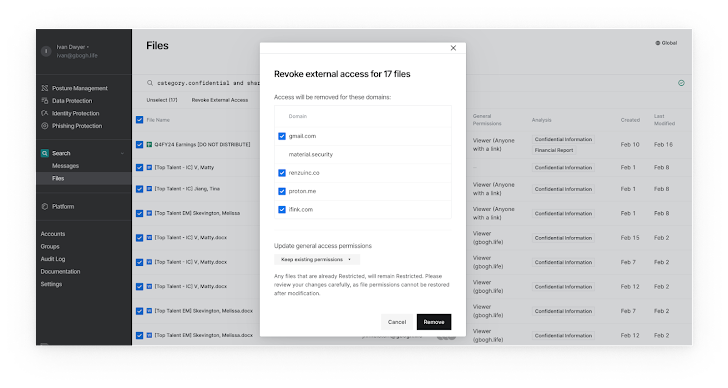
Block exfiltration paths with automatic remediation
The most important remediation method to take care of poisonous mixtures in Google Push is to revoke accessibility. That seems uncomplicated on the surface area, but when you take into account the disorders of the complete house, it gets a multi-dimensional puzzle. When is exterior sharing legitimate and when is it not? Are there customers that belong to groups that they should not? Which configurations need to modify when a document is modified to insert private facts?
Exact lookup and action-primarily based filtering enables remediation workflows for situations this sort of as:
- Mechanically revoking general public backlinks for any file that contains labeled data
- Sending consumers a concept to confirm exterior sharing when data files comprise any delicate data
- Cutting off access to all information shared with particular external domains in a solitary bulk work
- Revoking all entry to a distinct account that displays behaviors of a compromise
- Resetting any information available to the organization that contain individual well being info to Limited
Implementing automation usually can get in the way of day-to-day use, so it’s crucial to establish with precision – a greater comprehending of the mother nature of information, which domains are reliable, and widespread consumer behaviors enable you contain the floor spot the correct way.
Retain your efficiency suite productive with Content Security
At Material, we concentration our endeavours on the productivity suite simply because we imagine that it’s critical infrastructure to any group. And as critical infrastructure, in-depth security defenses that can correctly prevent attacks and minimize risk throughout the setting are paramount.
The new capabilities with Details Defense for Google Drive solve really hard information discovery, governance, and accessibility issues that have historically been complicated to do without the need of devoted tooling.
Want to see it for your self? Plan a own demo with our crew now.
Uncovered this short article exciting? This short article is a contributed piece from a single of our valued associates. Adhere to us on Twitter and LinkedIn to browse additional exclusive written content we write-up.
Some elements of this report are sourced from:
thehackernews.com

 U.S. Cracks Down on Predatory Spyware Firm for Targeting Officials and Journalists
U.S. Cracks Down on Predatory Spyware Firm for Targeting Officials and Journalists