Made by John Tuckner and the workforce at workflow and automation platform Tines, the SOC Automation Ability Matrix (SOC ACM) is a set of techniques created to help security functions groups understand their automation capabilities and answer a lot more properly to incidents.
A customizable, vendor-agnostic instrument featuring lists of automation opportunities, it truly is been shared and suggested by members of the security group given that its start in January 2023, notably by Airbnb engineer Allyn Stott in his BSides and Black Hat chat, How I Realized to Prevent Worrying and Build a Modern Detection & Reaction Method.
The SOC ACM has been in comparison to the MITRE ATT&CK and RE&CT frameworks, with just one consumer expressing, “it could be a standard for classification of SOAR automations, a little bit like the RE&CT framework, but with a lot more automation target.” It is really been applied by corporations in Fintech, Cloud Security, and beyond, as a foundation for assessing and optimizing their security automation applications.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Here, we are going to consider a closer search at how the SOC ACM is effective, and share how you can use it in your group.
What is the SOC Automation Capability Matrix?
The SOC Automation Capacity Matrix is an interactive established of tactics that empower security functions groups to respond proactively to typical cybersecurity incidents.
It is really not a listing of unique use situations associated to any just one item or service, but a way to consider about the abilities an corporation might comply with.
It features a sound basis for inexperienced persons to fully grasp what is actually doable with security automation. For much more state-of-the-art applications, it serves as a resource of inspiration for future implementations, a resource to gauge achievement, and a signifies to report results.
When the instrument is vendor-agnostic, it pairs well with a platform like Tines, which was developed by security practitioners to help fellow security practitioners automate their mission-critical procedures.
How does the SOC Automation Capability Matrix do the job?
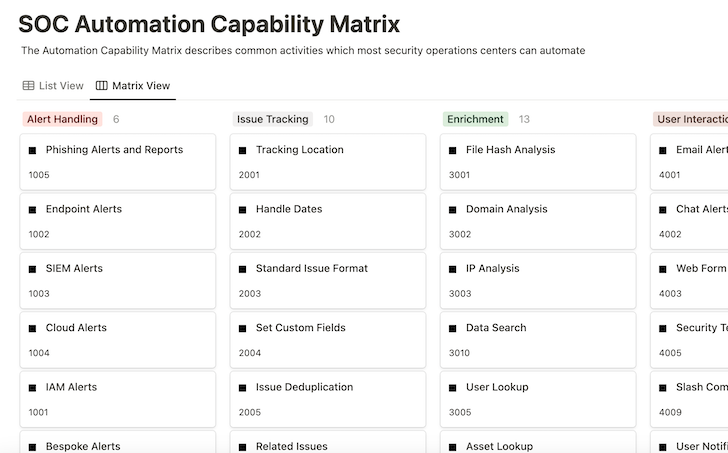
The SOC ACM is split into categories that comprise automation capabilities.
Each individual functionality includes:
- Description – a brief overview of what the capability is accomplishing
- Strategies – technology-agnostic suggestions for how to employ the functionality
- Examples – appropriate workflow templates from the Tines library
- References – other research contributing to the functionality
The framework reads from remaining to proper and leading to bottom in categories. While it is minimally opinionated about which abilities carry the most price or are simpler to carry out, the framework is adaptable to what organizations find most worthwhile.
Every ability can stand by itself in the matrix, but signing up for a lot of abilities with each other can create numerous a lot more complicated and impactful outcomes.
How to use the SOC Automation Functionality Matrix
Subsequent, we’ll illustrate how to use the SOC ACM, using phishing reaction as our example. Quite a few businesses use numerous strategies to come across and evaluate suspicious messages to reply properly to destructive e-mail.
To start out, listed here are some procedures a regime phishing investigation may possibly include things like:
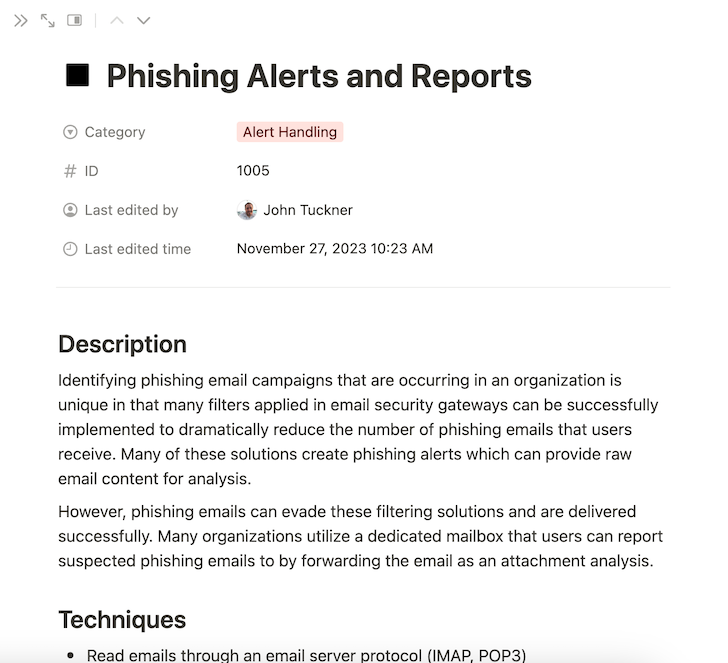
Within just the matrix capability, Phishing Alerts appear in the Inform Managing area it mentions that quite a few organizations apply equipment like email security gateways to avoid suspicious e-mail from currently being delivered to inboxes whilst also building alerts of attack strategies that could be automatic.
The capability also outlines a system to produce a purposeful inbox for consumers to easily ahead phishing e-mail that might have handed by the filters. Employing both of those of these capabilities offers an opportunity to begin an automation workflow.
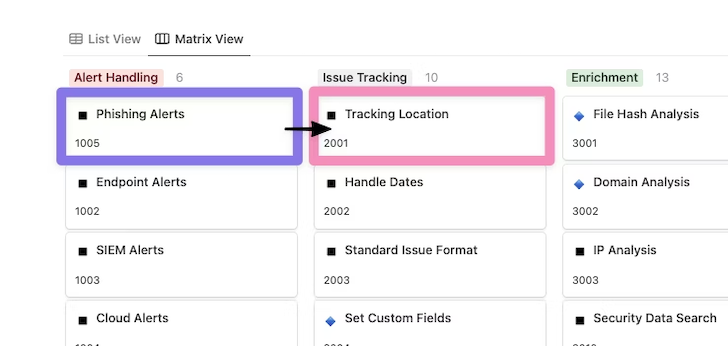
The moment a suspicious concept has been recognized, possibly as a result of the person reporting or generated warn, a lot more automation abilities grow to be accessible. One recommendation is to develop a locale for monitoring the lifecycle of each alert as shortly as doable.
Utilizing the Tracking Spot capability in the Issue Monitoring portion, we can discover where by these alerts should really be recorded, current, and described. Notice how the workflow has now moved involving sections of the Automation Functionality Matrix to increase the system.
With the notify and tracking area determined on, we can transfer towards doing a extensive investigation of the phishing notify in problem. Phishing email messages generally contain possibly destructive attachments and suspicious hyperlinks to seize authentication substance and are normally sent from spoofed resources.
Shifting into the Enrichment phase, we want to concentrate on employing a couple important abilities at a least: Area Analysis for any backlinks existing in the email entire body, File Hash Examination/File Analysis to appear at any attachments to the email, and Email Attributes to search deeper into email headers for symptoms of e-mail from spoofed addresses.
For Enrichment possibilities, the amount of possibilities for API-driven tools and solutions that can be applied to offer these abilities grows exponentially. Some frequent selections involve VirusTotal for files, URLscan for domains, and EmailRep for sender facts. Every single of these enrichment success can be recorded in the connected monitoring locale discovered earlier to document the results and deliver analysts with a look at into the final results.
This shows how numerous abilities from the very same portion can be applied to the exact same automation workflow, in this scenario, to supply as much facts as doable to analysts.

Right after enrichment happens, a verdict may be arrived at now, but additional likely, the issue will require a speedy overview from an analyst. At this position, the Person Conversation section gets critical.
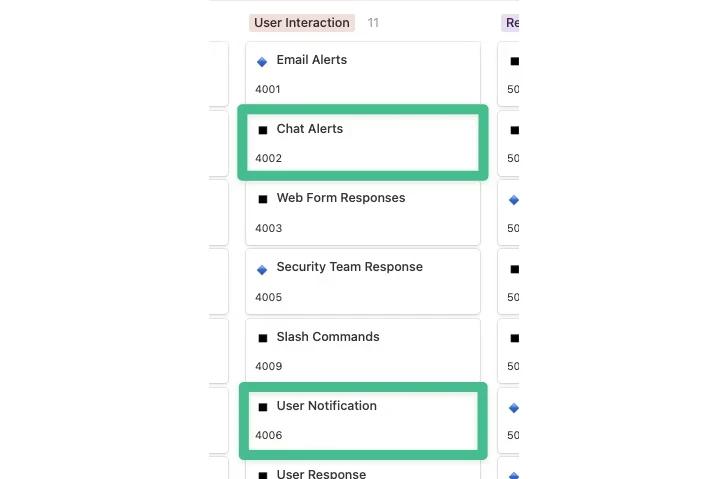
To start off, we can use Chat Alerts to notify the security group in a Slack channel that a phishing email has arrived and a tracking issue has been produced, with various enrichment aspects additional as extra context is completely ready for evaluate.
That takes care of informing the security group, but what about updating any people who could possibly be impacted or who documented the email? Phishing reaction processes, in certain, are distinctive for the reason that lots of organizations actively educate end users to report e-mail they may possibly establish as suspicious. Informing these customers with a self-confident verdict within just a small timeframe is a fantastic way to empower operations these kinds of as finding delicate documents signed immediately or blocking mass malware outbreaks.
To do this, we can use the User Notification capability to discover the user who documented the email and present them with the effects of the email investigation. In the scenario of Person Interaction, it is really not only about extra notification of the security staff but also extending the get to and empowering many others with real-time information to make the appropriate choices.
At this position, a ton of activity has taken place, and we have a good deal of information at our disposal. Whilst extra information and facts is normally valuable, acting on it correctly is what ultimately counts most, ensuing in the remediation stage. Quite a few of the knowledge factors (indicators) we gathered right before can be used for remediation motion. Dependent on how the circumstance has played out, we could just take some of the following methods:
- Area blocklist: Incorporate any domains and URLs determined as suspicious to a blocklist.
- File hash blocklist: Include any file hashes determined as malicious to a blocklist.
- Email deletion: Take out e-mails similar to an attack campaign from inboxes.
- Password invalidation: Adjust the passwords of any people discovered to have submitted credentials to a phishing internet site.

The important to any remediation is being aware of what is achievable and beginning smaller, primarily when using automation to make confidence. A single way to do this is to present backlinks or buttons that need to have to be manually clicked to take remediation steps, but in a repeatable method. If you want to introduce entire automation, preserving lists of suspicious domains that can be blocked gives you with fantastic utility, minor risk, and can be mounted swiftly with tiny total influence when glitches happen.
On the lookout at the system conclude-to-conclude, we have utilized the pursuing abilities to enable automate critical actions for numerous cybersecurity groups:
- Phishing alerts
- Tracking place
- File hash investigation
- Domain examination
- Email attributes
- Chat alerts
- Person notification
- Domain blocklist
- File hash blocklist
- Email deletion
- Password invalidation
A significant benefit of acquiring these capabilities in your firm to handle a single system, these kinds of as phishing, is that quite a few of these abilities are now obtainable to be reused for supplemental needs like malware detection or dealing with suspicious logins, creating every single subsequent automation chance less complicated.
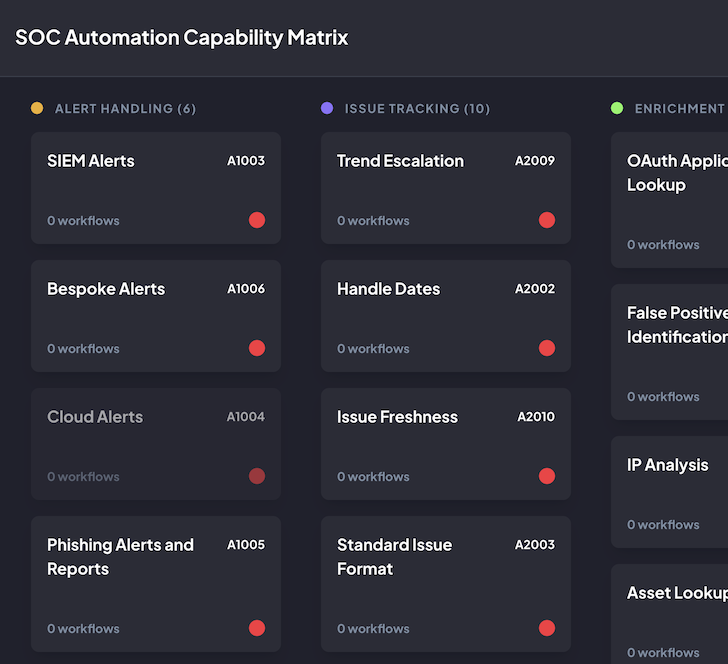
Customizing the matrix
The SOC ACM is also readily available on GitHub for those who like to operate it on their own or lead.
This way, the SOC ACM can be entirely custom-made to in shape your desires. This involves:
- Incorporating new groups and capabilities
- Reorganizing according to your priorities
- Tracking automation workflows that align with these abilities
- Exporting the configuration
- Dark and light-weight manner
You can also assess different environments or diverse corporations otherwise by creating different boards. For example, if your firm acquires a company with various abilities from yours, you can use the matrix to visualize that natural environment absolutely differently.
All of this configuration can be saved locally in your browser for privacy. As perfectly as exporting the configuration, you can import it to revive past assessments, all without having a login account, and without the need of any tracking.
The SOC ACM as a reporting instrument
Groups accessing the SOC ACM on GitHub can also use the matrix to visually display wherever they are in their automation journey and connect the benefit of their automation system to leadership and other key stakeholders.
Shortly after employing a number of capabilities, groups will have an understanding of which capabilities they’re making use of most, the associated pursuits, and their price, such as time saved or reduced response time. This enables them to share success with related groups and come to a decision what to prioritize upcoming.
Situation review: monitoring time saved and executions to clearly show worth with the SOC ACM
At the Tines Roadshow: San Francisco, the creator of the SOC Automation Ability Matrix, John Tuckner, shared how he worked with a Fintech organization to evaluate and boost their automation program applying the matrix. They advised Tuckner, “The Automation Capacity Matrix will help us arrange our workflows, detect which workflows are saving us the most time, and spotlight long term regions of prospect.”
Highlights:
- 25 abilities carried out and tagged
- 10 workflows making use of Slack slash instructions with 2,000 executions
- Send multifactor prompt workflows ran 721 occasions for 6.5 hours of time financial savings for every thirty day period
Tips:
- Glance at managing lists of IOCs for response abilities, “IP list,”https://thehackernews.com/2024/02/”area listing,” and “hash listing.”
- Document and spotlight the endeavours made in time saved when making use of situation management.
Potential state – what they’re going to do otherwise:
- Tackling dispersed alerting, person interaction by way of Slack
- Consumer notification
- Consumer response
- Updating security Slack channel and incident reporting to use a Slack bot and route reviews and asks to the accurate subteam
- Notify unexpected emergency assets
- Timed escalations
- Slash commands
- Insert much more reaction actions via Tines automation by our Slack bot
- Artifact gathering
- Disabling MFA gadget
- Asset lookup (not just endpoints, will need to consist of cloud belongings)
The SOC Automation Ability Matrix is a valuable useful resource for teams at all stages in their automation journey, giving inspiration for their subsequent automation builds and a suggests to evaluate their automation method.
If you would like to investigate the SOC Automation Ability Matrix in extra element, you will uncover it on Notion, hosted by the Tines crew.
Observed this write-up attention-grabbing? This article is a contributed piece from one particular of our valued companions. Comply with us on Twitter and LinkedIn to read through much more exclusive written content we put up.
Some sections of this posting are sourced from:
thehackernews.com

 Researchers Detail Apple’s Recent Zero-Click Shortcuts Vulnerability
Researchers Detail Apple’s Recent Zero-Click Shortcuts Vulnerability