2021 was a 12 months peppered by cyberattacks, with numerous information breaches occurring. Not only that, but ransomware has also become a prominent participant in the hackers’ environment.
Now, much more than ever, it is really critical for enterprises to phase up cybersecurity measures. They can do this as a result of numerous pieces of technology, this kind of as an open up-supply security platform like Wazuh.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Wazuh is a no cost and open supply security platform that unifies XDR and SIEM capabilities, which not only permits companies to detect sophisticated threats, but can also assist immensely in avoiding info breaches and leaks from going on. As a result, it can preserve companies from costly fixes that can eventually end in their closure.
It is also doable to integrate Wazuh with a variety of external solutions and equipment. Some of them are VirusTotal, YARA, Amazon Macie, Slack, and Fortigate Firewall. Consequently, firms can enhance their security in opposition to hackers from penetrating their networks.
What’s terrific about Wazuh is that it’s scalable, open up resource and free. It can compete with quite a few substantial-stop cybersecurity methods that are out there for a large amount of dollars. So this can help SMEs immensely funds-wise.
Examine on to come across out far more on how Wazuh can enable with cybersecurity for enterprises.
Security Analytics
Wazuh immediately collects and aggregates security info from techniques functioning Linux, Windows, macOS, Solaris, AIX, and other operating systems in the monitored area, producing it an extremely extensive SIEM alternative.
But extra importantly, Wazuh also analyzes and correlates information in buy to detect anomalies and intrusions. This sort of intelligence usually means there is certainly early threat detection in different environments.
For example, Wazuh can be applied in the business office, as effectively as in cloud environments so distant personnel can nevertheless enjoy the advantages of Wazuh. Strengthening electronic security will not have to be limited to just a brick-and-mortar location.
Intrusion Detection
Wazuh software has multi-system agents that check systems, detect threats, and result in automatic responses as essential. A lot more exclusively, they hone in on rootkits and malware, as nicely as suspicious anomalies.
In addition, these brokers can detect stealth technology like hidden documents, cloaked procedures, and unregistered network listeners.
On prime of these capabilities for intrusion detection, Wazuh’s server has a signature-based strategy. It analyzes collected log info and can establish points of compromise by evaluating them with regarded signatures.
This feature can promptly determine and avert employees from downloading and installing malicious applications.
This provides workplaces a protection net. Worker education and learning on cybersecurity really should be the initially line of defense, following all.
Vulnerability Detection
Wazuh can also pinpoint the place network vulnerabilities are. This allows enterprises to discover their weakest back links and plug up holes ahead of cybercriminals can exploit them 1st.
Wazuh brokers will pull software program stock knowledge and ship it to their server. Here, it’s when compared with continuously up to date popular vulnerabilities and publicity (CVE) databases. As a consequence, these agents will obtain and discover any software package which is vulnerable.
In lots of situations, antivirus computer software can take treatment of these vulnerabilities. These packages launch security patches on a normal foundation.
But in unusual scenarios, antivirus builders will never discover vulnerabilities in time. Or they may not find them at all, which can depart enterprises uncovered. Possessing Wazuh means businesses get an excess set of eyes to be certain their cybersecurity is airtight.
Log Knowledge Examination
Not only does Wazuh acquire network knowledge and application logs, but it also securely sends them to a central manager for rule-dependent evaluation and storage.
This evaluation of log facts is based mostly on above 3000 various policies that identify anything that has long gone incorrect, no matter whether it is an outside the house force or person mistake. For illustration, the procedures in position can detect software or method faults, coverage violations, misconfigurations, as well as attempted or productive destructive action.
In addition, the log data investigation can pinpoint both tried and profitable malicious routines. Early detection is vital in retaining networks risk-free.
Enterprises can study from tried malicious routines and update their cybersecurity accordingly.
And for effective destructive pursuits, the procedure can speedily quarantine infected files. Or they can delete them right before they can do a lot more hurt.
An additional issue the log information examination can display is policy violations. No matter if they’re intentional or unintended, these violations can be brought to management’s consideration. Then, they can just take swift motion to rectify the scenario.
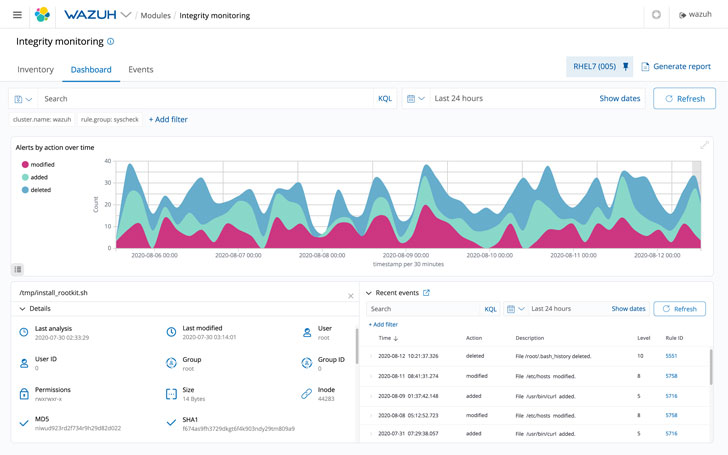
File Integrity Checking
Wazuh’s File integrity monitoring (FIM) attribute can be configured to scan selected files or directories periodically and warn the user when any improvements are detected. Not only does it hold monitor of which users develop and modify data files, but it also tracks which programs are employed and when possession is improved.
Thanks to the level of depth from file integrity monitoring, corporations will be able to know exactly when threats arrive in. They will also detect compromised hosts appropriate absent.
For instance, ransomware is now rampant, but Wazuh can help prevent and detect this menace. Ought to a hacker endeavor phishing, the security checking will select up on the destructive documents that have snuck in. It will detect new information created, as effectively as any initial documents eliminated.
Must there be a superior quantity of these situations, the file integrity checking will flag it as a doable ransomware attack. Notice that customized rules should really be established for this to come about.
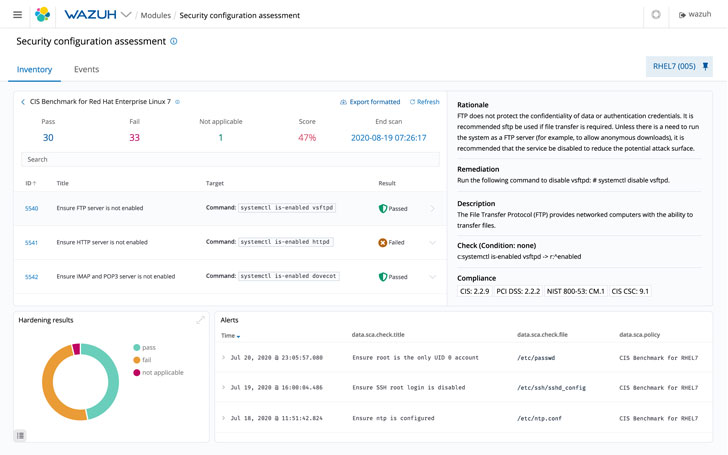
Configuration Evaluation
Security compliance is crucial to improve an organization’s security posture and reduce its attack surface area. But it can be equally time-consuming and demanding. Thankfully, Wazuh can guide with it.
Wazuh’s Automated Security Configuration Assessment (SCA) seems to be for misconfigurations and will help maintain a typical configuration throughout all monitored endpoints.
In addition, Wazuh agents also scan applications that are acknowledged to be vulnerable, unpatched or configured insecurely. That way, the strongest cybersecurity walls are up at all moments.
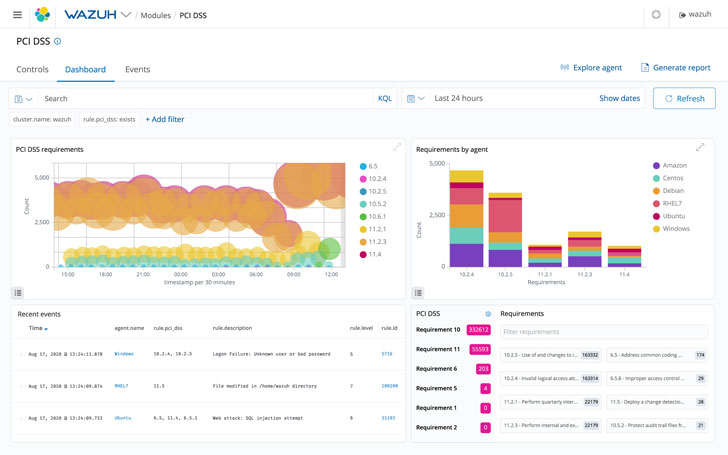
Regulatory Compliance
On the matter of compliance, the regulatory compliance aspect also aids customers hold up with standards and laws. A lot more importantly, it enables corporations to scale and integrate other platforms.
Wazuh generates reports with its web consumer interface. There are also several dashboards to permit users to take care of all platforms from one put. If the agents detect anything at all that is non-compliant, the people are quickly alerted.
Its ease of use allows a lot of financial providers satisfy Payment Card Sector Facts Security Regular (PCI DSS) needs. This consists of payment processing providers, also.
These in the health care business can have peace of head recognizing they are HIPAA-compliant. And for these who offer with European details, they are going to be GDPR-compliant as nicely.
Incident Reaction
Incident reaction is a really valuable attribute of Wazuh for active threats. There are out-of-the-box energetic responses, which indicates the user will not have to do anything to established them up. Should really the system detect active threats, countermeasures leap into motion suitable absent.
For example, many hackers use brute-pressure attacks to guess username and password combos. Wazuh will consider take note of each and every unsuccessful authentication attempt.
With enough failures, the procedure will recognize them as section of a brute-pressure attack. Simply because a selected criterion is met (e.g., five failed login tries), it will block that IP address from even further tries. This implies not only can Wazuh choose up on brute-drive attacks, but it can also shut them down.
In addition, consumers can use it to operate distant instructions and technique queries. They can also remotely determine indicators of compromise (IOCs).
This makes it possible for third events to operate live forensics and incident reaction jobs. As a result, this opens up opportunities to do the job with extra professionals who can safeguard organization knowledge.
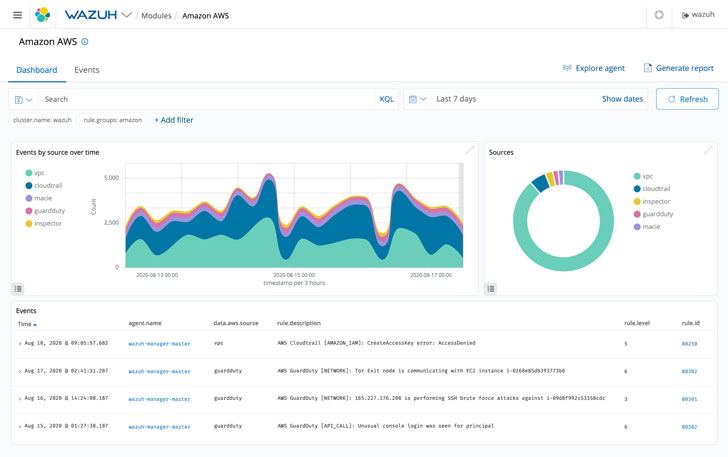
Cloud Security
Today, lots of workplaces use the cloud to retail outlet documents. This will allow personnel to entry them from all over the globe, so long as they have an internet connection.
But with this benefit comes a new security worry. Any individual with an internet connection can perhaps hack the cloud and achieve access to sensitive information.
Wazuh utilizes integration modules, which pull security info from properly-known cloud providers, such as Amazon AWS, Microsoft Azure or Google Cloud. In addition, it sets regulations for a user’s cloud natural environment to spot opportunity weaknesses.
It will work likewise to the vulnerability detection operate. It will warn people to intrusion attempts, system anomalies, and unauthorized consumer steps.
Containers Security
Wazuh’s containers security feature presents cyber risk intelligence for Docker hosts, Kubernetes nodes and containers. All over again, it will obtain system anomalies, vulnerabilities, and threats.
The agent’s indigenous integration means customers don’t have to set up connections with their Docker hosts and containers. It will maintain gathering and examining information. It will also present users with steady monitoring of operating containers.
Wazuh is a Have to for Enterprises
As the digital world keeps evolving, so do cybercriminals. Thus, preserving up with cybersecurity measures and investing in top-of-the-line intrusion detection is crucial.
Wazuh combines all of these capabilities in a solitary system, generating it a strong instrument for analysts as properly as a true pressure multiplier for overburdened IT team.
Comparatively to other alternatives, Wazuh automatically adds relevant context to alerts and analyses, allows greater final decision-creating, and helps in strengthening compliance and risk administration.
When merged with vulnerability detection, file integrity checking, and configuration evaluation, Wazuh can aid enterprises in remaining just one phase forward of hackers.
By investing time and means into this absolutely free system, corporations can construct much more layers to their cybersecurity measures. And in return, they will set on their own up for more safe networks for years to occur.
Wazuh integrations
Under there are quite a few hyperlinks wherever you can see how Wazuh can be built-in with distinctive applications and software and how abilities can be extended with these integrations:
- VirusTotal
- YARA
- Slack
- Owlh
- Suricata
Discovered this article attention-grabbing? Comply with THN on Facebook, Twitter and LinkedIn to examine additional exclusive written content we submit.
Some parts of this article are sourced from:
thehackernews.com



 Online Investment Fraud Network Taken Down by Law Enforcement
Online Investment Fraud Network Taken Down by Law Enforcement