Critical infrastructure is crucial for societal existence, growth, and improvement. Societies are reliant on the companies presented by critical infrastructure sectors like telecommunication, power, healthcare, transportation, and info technology. Basic safety and security are necessary for the exceptional operation of these critical infrastructures. Critical infrastructure is created up of electronic and non-digital belongings. Organizations should remain forward of cybersecurity threats to avoid failures induced by cyber attacks on critical infrastructure. Locating methods to safeguard electronic belongings in an at any time-modifying landscape loaded with threats is a continual action. Organizations have to also utilize economical security answers and greatest methods to keep guarded and decrease the prospects of compromise.
Security remedies assist secure and boost the visibility of an organization’s threat landscape. Different answers use diverse principles and techniques. An important notion that has risen not too long ago is Extended Detection and Reaction (XDR).
XDR answers provide detection and reaction capabilities throughout many levels. XDR tools correlate info working with threat detection and reaction procedures by collecting logs and situations from various sources, this sort of as network units, servers, and purposes. These abilities make it possible for security groups to rapidly detect, investigate and react to incidents.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Attacks on critical infrastructure
In February 2022, a source chain attack transpired in a single of Germany’s power giants. This attack led to the closure of additional than 200 gas stations across Germany, impacting lives and firms. This party transpired just about a year right after the Colonial Pipeline attack in the United States of The united states, in which knowledge exfiltration happened and a ransomware an infection shut down digital solutions within just their infrastructure for times. An short article from the NYTimes claimed that an believed 5 million bucks were compensated to the hackers associated in the Colonial Pipeline ransomware attack. The hackers in the Colonial Pipeline case ended up in a position to achieve entry making use of a compromised VPN password, and they proceeded to complete intrusion actions for an full working day ahead of they ended up detected.
There are numerous entry points for attacks on critical infrastructure, and some vectors are more prevalent than others. These vectors include compromised credentials, unpatched running systems, susceptible purposes, and malware delivered by means of different techniques.
Emphasis ought to be placed on securing critical infrastructure prior to an attack occurs, irrespective of how it originates. Security methods assistance companies secure them selves from diverse attack vectors. These solutions contain XDR, SIEM, code scanners, infrastructure analyzers, vulnerability scanners, and malware detection remedies. In addition to these alternatives are compliance standards. A several advisable criteria are NIST, PCI DSS, HIPAA, and GDPR. The proper software of these options and compliance requirements can help make improvements to an organization’s security posture.
How XDR can mitigate attacks
An XDR plays a major job in cases where menace actors target diverse digital property of an corporation. With an XDR built-in into an organization’s infrastructure, security events from different resources and belongings are analyzed and correlated to establish what routines are happening in the infrastructure. An XDR has the ability to detect and present automated responses to destructive activities in an setting. This sort of a reaction can eliminate a malicious process, delete a malicious file, or isolate a compromised endpoint. As the responses are executed in in close proximity to true-time, speed plays a critical job in the execution of these responsibilities.
Wazuh SIEM/XDR
Wazuh is a absolutely free and open resource SIEM and XDR platform. It consists of a number of parts that shield both of those cloud and on-premises workloads. The Wazuh platform operates with an agent-server product. The Wazuh central elements (server, indexer, and dashboard) review security facts from endpoints in your infrastructure. At the exact same time, the Wazuh agent is deployed on endpoints to collect security information and provide menace detection and reaction. The Wazuh agent is light-weight and supports numerous platforms. Wazuh also supports agentless monitoring on routers, firewalls, and switches.
Wazuh XDR abilities
Wazuh has numerous abilities that assistance an organization remain in advance of security threats. Some of these capabilities are malware detection, vulnerability detection, file integrity checking, and automated reaction to threats, among others. The next sections consist of a lot more aspects on Wazuh capabilities that assist in defending critical infrastructure.
Log information investigation
The Wazuh log details examination module collects and analyzes security details from many sources. This sort of info incorporate system party logs, application logs, and abnormal process habits logs. As a result, the analyzed knowledge is applied for menace detection and automatic response. This ability provides you visibility into functions happening at distinctive endpoints in your infrastructure.
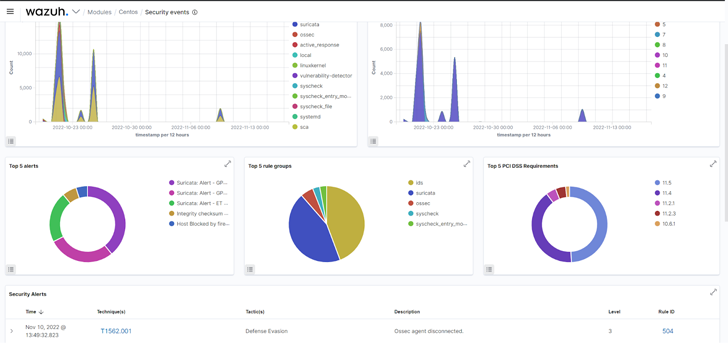 Fig 1: Security events of a monitored endpoint on the Wazuh dashboard.
Fig 1: Security events of a monitored endpoint on the Wazuh dashboard.
Malware detection
Wazuh has quite a few functions that aid in malware detection. In addition, Wazuh can be built-in with other security tools like YARA and VirusTotal to detect malware. By correctly configuring Wazuh Regular Database (CDB) lists, values from decoded alerts this kind of as users, file hashes, IP addresses, or domain names can be compared with destructive information. Below is a weblog article that demonstrates how Wazuh can be integrated with CDB lists for detecting and responding to destructive documents. This Wazuh capacity can help you detect malware on different monitored endpoints.
File integrity monitoring
The Wazuh File Integrity Monitoring (FIM) module displays an endpoint filesystem to detect improvements in predefined documents and directories. Alerts are activated when a file is created, modified, or deleted in monitored directories. You can see how this module is utilized to detect alterations to an SSH vital file in the website post Detecting illegitimate crypto miners on Linux endpoints. Making use of the Wazuh FIM module, you can detect adjustments to configuration documents on critical units and establish if the activity is authorized or malicious.
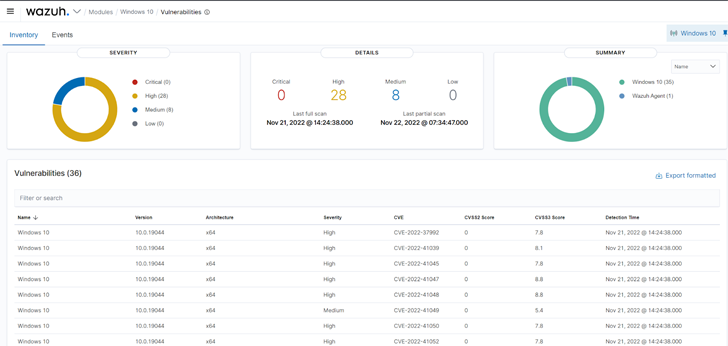
Vulnerability detection
Wazuh employs the Vulnerability detector module to obtain vulnerabilities on a monitored endpoint. Vulnerability detection is effective by doing application audits. These audits are designed probable by leveraging vulnerability feeds indexed from resources like Canonical, Debian, Crimson Hat, Arch Linux, ALAS (Amazon Linux Advisories Security), Microsoft, and the National Vulnerability Database. These feeds are cross-correlated by Wazuh with details from the endpoint’s software inventory. Directors should start remediation instantly soon after vulnerabilities are detected ahead of destructive actors can exploit them.
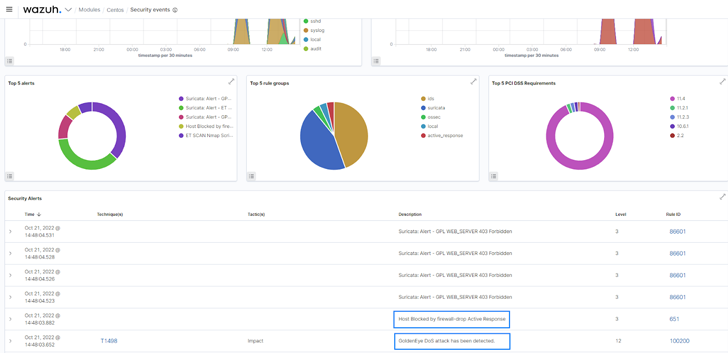
Automatic reaction to threats
The Wazuh energetic reaction module can be configured to mechanically execute countermeasures when activities match distinct standards. It can execute consumer-described actions, these kinds of as a firewall block or drop, targeted visitors shaping or throttling, account lockout, system shutdown, and so forth. The active reaction module was configured to deny network relationship from an discovered malicious resource in the site put up Responding to network attacks with Suricata and Wazuh XDR.
Conclusion
Applying security throughout several layers of critical infrastructure cuts down an organization’s attack surface. We have emphasized a several things to retain in intellect to maintain a appropriate security posture. In protecting your electronic property, we advise a resolution that works perfectly with many endpoints, programs, and systems.
Wazuh is a absolutely free and open up supply XDR remedy. It consists of the abilities vital to discover vulnerabilities, establish the technique configuration point out, and react to threats on your digital property. Wazuh also supplies guidance for compliance criteria like PCI DSS, HIPAA, NIST, and GDPR. Wazuh has an at any time-escalating local community where help is offered to users. Examine out the Wazuh documentation for far more facts.
Observed this report exciting? Stick to us on Twitter and LinkedIn to study far more special content material we publish.
Some components of this post are sourced from:
thehackernews.com


 ConnectSecure marks rebrand with new CEO appointment
ConnectSecure marks rebrand with new CEO appointment