In today’s rapidly evolving SaaS ecosystem, the aim is on human end users. This is a single of the most compromised places in SaaS security administration and requires rigorous governance of user roles and permissions, checking of privileged consumers, their stage of activity (dormant, energetic, hyperactive), their style (inside/ exterior), irrespective of whether they are joiners, movers, or leavers, and a lot more.
Not surprisingly, security endeavours have generally been human-centric. Configuration possibilities contain applications like MFA and SSO for human authentication. Function-primarily based entry command (RBAC) limits the amount of access password complexity tips block unauthorized individuals from accessing the software.
Still, in the earth of SaaS, there is no scarcity of obtain granted to non-human actors, or in other phrases, 3rd party linked apps.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Support accounts, OAuth authorizations, and API keys are just a number of of the non-human identities that have to have SaaS obtain. When viewed as a result of the lens of the software, non-human accounts are related to human accounts. They have to be authenticated, granted a established of permissions, and monitored. However, because they are non-human, considerably less considered is given to ensuring security.
Non-human Accessibility Examples
Integrations are probably the least complicated way to fully grasp non-human obtain to a SaaS app. Calendly is an app that removes the back-and-forth email messages of appointment-creating by displaying a user’s availability. It integrates with a user’s calendar, reads the calendar to determine availability, and routinely provides appointments. When integrating with Google Workspace via an OAuth authorization, it requests scopes that enable it to see, edit, share, and delete Google Calendars, amongst other scopes. The integration is initiated by a human, but Calendly is non-human.
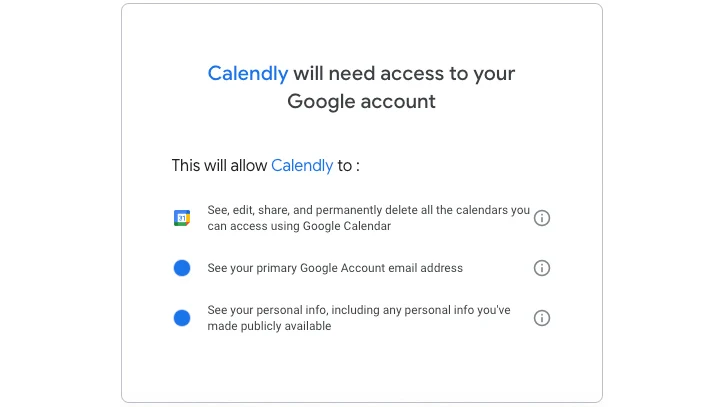 Determine 1: Calendly’s required permission scopes
Determine 1: Calendly’s required permission scopes
Other non-human accounts contain information sharing amongst two or extra purposes. SwiftPOS is a place-of-sale (POS) application and machine for bars, dining places, and retail outlets. Information captured by the POS is transferred to a small business intelligence system, like Microsoft Electricity BI, exactly where it is processed and analyzed. The info is transferred from SwiftPOS to Electric power BI by means of a non-human account.
The Problem of Securing Non-human Accounts
Controlling and securing non-human accounts is not as simple as it seems. For starters, each individual application has its individual technique to controlling these kinds of user accounts. Some applications, for illustration, disconnect an OAuth integration when the person who licensed it is deprovisioned from the application, when other individuals manage the relationship.
SaaS purposes also take distinct approaches to taking care of these accounts. Some consist of non-human accounts in their user stock, even though some others retail store and display the knowledge in a various segment of the software, producing them quick to overlook.
Human accounts can be authenticated by means of MFA or SSO. Non-human accounts, in contrast, are authenticated one particular time and forgotten about until there is an issue with the integration. Individuals also have typical actions designs, such as logging on to programs through doing the job hrs. Non-human accounts generally obtain applications throughout off-peak time to lessen network traffic and pressure. When a human logs into their SaaS at 3 AM, it may cause an investigation when a non-human hits the network at 3 AM, it can be just organization as usual.
In an work to simplify non-human account management, numerous corporations use the identical API vital for all integrations. To facilitate this, they grant broad authorization sets to the API critical to deal with all the opportunity needs of the corporation. Other situations, a developer will use their have large-permission API essential to grant access to the non-human account, enabling it to access nearly anything in the software. These API keys purpose as all-entry passes made use of by a number of integrations, earning them unbelievably tough to handle.
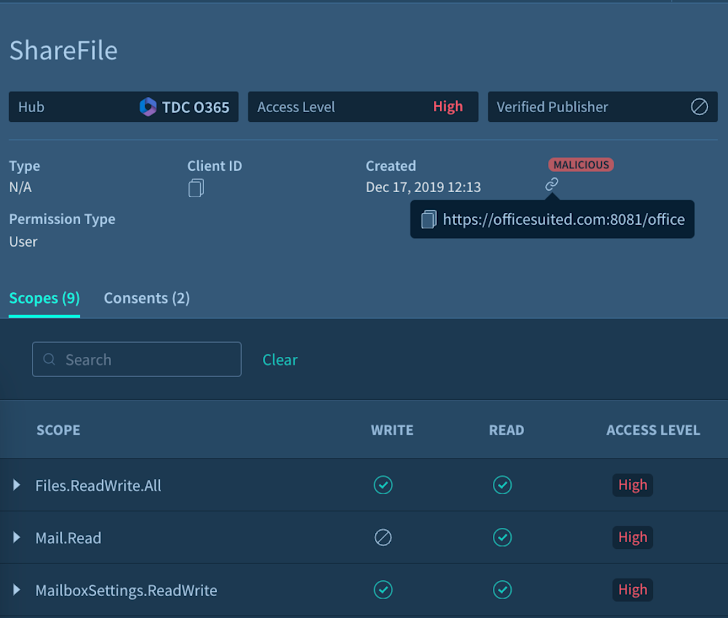 Figure 2: A Malicious OAuth Application detected by way of Adaptive Shield’s SSPM
Figure 2: A Malicious OAuth Application detected by way of Adaptive Shield’s SSPM
Indication up for THN’s impending Webinar: Actuality Test: Identification Security for Human and Non-Human Identities
The Risk Non-human Accounts Add to SaaS Stack
Non-human accounts are largely unmonitored and have large-ranging authorization scopes. This can make them an interesting goal for threat actors. By compromising any of these accounts, risk actors can enter the application undetected, top to breaches, unauthorized modifications, or disruptions in company.
Getting Ways to Protected Non-human Accounts
Making use of a SaaS Security Posture Administration (SSPM) system in live performance with Identification Threat Detection & Reaction (ITDR) alternatives, corporations can correctly manage their non-human accounts and detect when they behave anomalously.
Non-human accounts demand the very same visibility by security groups as human accounts and ought to be managed in the very same consumer inventory as their human counterparts. By unifying id management, it is significantly a lot easier to watch accessibility and permissions and update accounts no matter of who the proprietor is. It also assures a unified strategy to account management. Organizational insurance policies, such as prohibiting account sharing, need to be utilized across the board. Non-human accounts should really be restricted to distinct IP addresses that are pre-authorized on an let listing, and ought to not be granted accessibility through the common login screens (UI login). Moreover, permissions should be tailor-made to fulfill their specific needs as apps, and not be large-ranging or matching their human counterparts.
ITDR performs an important job as properly. Non-human accounts may access SaaS applications at all several hours of the night time, but they are generally rather reliable in their interactions. ITDR can detect anomalies in actions, whether it really is modifications in timetable, the kind of data being additional to the application, or the actions currently being executed by the non-human account.
The visibility offered by SSPM into accounts and ITDR into non-human identity conduct is essential in taking care of dangers and pinpointing threats. This is an crucial exercise for maintaining safe SaaS programs.
Go through much more about preserving towards non-human identities
Located this short article intriguing? This short article is a contributed piece from just one of our valued partners. Adhere to us on Twitter and LinkedIn to go through far more distinctive content we put up.
Some components of this posting are sourced from:
thehackernews.com


 Ex-Google Engineer Arrested for Stealing AI Technology Secrets for China
Ex-Google Engineer Arrested for Stealing AI Technology Secrets for China