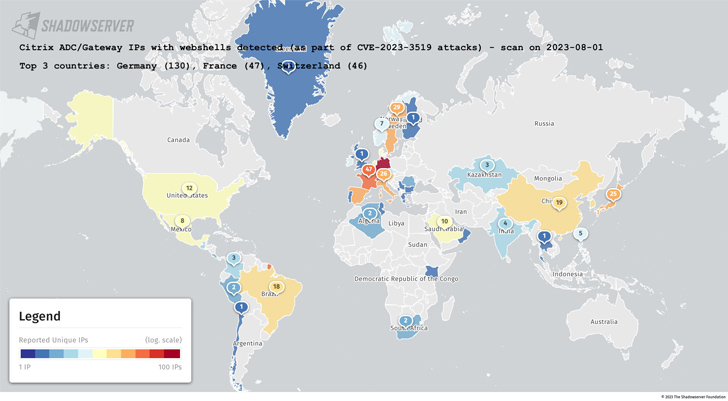
Hundreds of Citrix NetScaler ADC and Gateway servers have been breached by destructive actors to deploy web shells, according to the Shadowserver Foundation.
The non-revenue claimed the attacks consider advantage of CVE-2023-3519, a critical code injection vulnerability that could direct to unauthenticated distant code execution.
The flaw, patched by Citrix last thirty day period, carries a CVSS score of 9.8.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The greatest range of impacted IP addresses are based mostly in Germany, adopted by France, Switzerland, Italy, Sweden, Spain, Japan, China, Austria, and Brazil.
The exploitation of CVE-2023-3519 to deploy web shells was formerly disclosed by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which claimed the attack was directed from an unnamed critical infrastructure organization in June 2023.

The disclosure will come as GreyNoise explained it detected 3 IP addresses making an attempt to exploit CVE-2023-24489 (CVSS rating: 9.1), an additional critical flaw in Citrix ShareFile computer software that enables for unauthenticated arbitrary file add and distant code execution.
The issue has been resolved in ShareFile storage zones controller model 5.11.24 and later on.
Attack area management business Assetnote, which found and documented the bug, traced it to a less difficult version of a padding oracle attack.
“[Cipher Block Chaining] manner and PKCS#7 padding are the default values for AES encryption in .NET,” security researcher Dylan Pindur claimed.
“Seem at how it behaves when invalid as opposed to legitimate padding is offered. Does it result in an mistake? Are the mistakes unique? Does it choose more time or shorter to method? All of these can direct to a likely padding oracle attack.”
Located this short article fascinating? Abide by us on Twitter and LinkedIn to study far more special content material we post.
Some parts of this posting are sourced from:
thehackernews.com


 A Penetration Testing Buyer’s Guide for IT Security Teams
A Penetration Testing Buyer’s Guide for IT Security Teams