The danger actors linked to the malware loader identified as IcedID have designed updates to the BackConnect (BC) module that is utilized for article-compromise action on hacked techniques, new findings from Staff Cymru expose.
IcedID, also called BokBot, is a strain of malware comparable to Emotet and QakBot that begun off as a banking trojan in 2017, before switching to the purpose of an first obtain facilitator for other payloads. Modern variations of the malware have been observed getting rid of functionality similar to on line banking fraud to prioritize ransomware delivery.
The BackConnect (BC) module, first documented by Netresec in October 2022, depends on a proprietary command-and-management (C2) protocol to trade commands involving a server and the contaminated host. The protocol, which comes with a VNC element for distant entry, has also been discovered in other malware these as the now-discontinued BazarLoader and QakBot.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
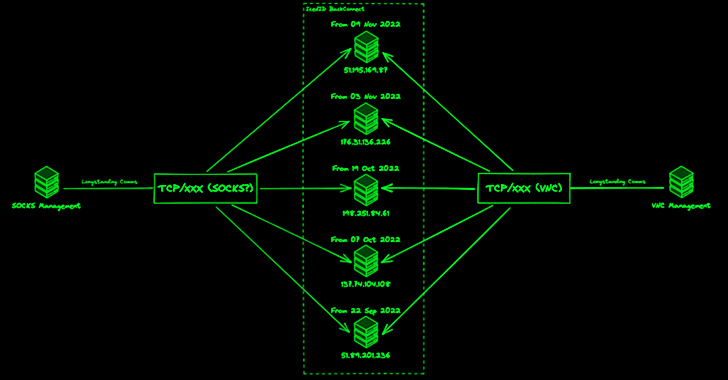
In December 2022, Team Cymru noted the discovery of 11 BC C2s active given that July 1, 2022, noting that operators probable situated in Moldova and Ukraine are overseeing distinct things of the BC protocol.
“For the previous a number of months, BackConnect visitors caused by IcedID was uncomplicated to detect mainly because it transpired over TCP port 8080,” Palo Alto Networks Device 42 mentioned in late May perhaps 2023. “However, as early as April 11, 2023, BackConnect action for IcedID adjusted to TCP port 443, making it more durable to come across.”
The most current evaluation of the attack infrastructure from Workforce Cymru has discovered that the number of BC C2s have shot up from 11 to 34 since January 23, 2023, with the common uptime of a server drastically lowering from 28 times to eight times.
“Because 11 April 2023, a total of 20 significant confidence BC C2 servers had been identified, based on pivots from management infrastructure,” the cybersecurity business explained in a report shared with The Hacker News.
“The initially observation is that the range of concurrent C2 servers in operation has greater […], with as numerous as 4 C2 servers getting management communications on a certain day.”
A further examination of the targeted visitors originating from BC C2 servers has uncovered as many as 8 candidate victims between late April 2023 and June 2023 that “communicated with a few or much more BC C2s more than a somewhat prolonged interval of time.”
Forthcoming WEBINARShield Against Insider Threats: Grasp SaaS Security Posture Administration
Nervous about insider threats? We have obtained you covered! Be a part of this webinar to explore useful techniques and the strategies of proactive security with SaaS Security Posture Management.
Be a part of These days
It can be also suspected that the same IcedID operator or affiliate is accessing several victims within the identical time frame, primarily based on the quantity of site visitors observed between the victims and the servers.
“In examining administration infrastructure connected with IcedID BC, we are also ready to discern a sample of a number of distinctive accesses from buyers we assess to be each associated with the working day to day operations of IcedID, and their affiliates who interact with victim hosts put up-compromise,” Staff Cymru reported.
“The proof in our NetFlow knowledge implies that certain IcedID victims are utilized as proxies in spamming operations, enabled by BC’s SOCKS abilities. This is a opportunity double blow for victims, not only are they compromised and incurring information / money decline, but they are also additional exploited for the uses of spreading even more IcedID campaigns.”
Identified this write-up appealing? Adhere to us on Twitter and LinkedIn to study far more exclusive articles we put up.
Some parts of this report are sourced from:
thehackernews.com

 STARK#MULE Targets Koreans with U.S. Military-themed Document Lures
STARK#MULE Targets Koreans with U.S. Military-themed Document Lures