A economically inspired threat actor of Indonesian origin has been observed leveraging Amazon Web Companies (AWS) Elastic Compute Cloud (EC2) instances to have out illicit crypto mining operations.
Cloud security firm’s Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil (pronounced Goo-ee-vil).
“The group shows a desire for Graphical Consumer Interface (GUI) equipment, especially S3 Browser (model 9.5.5) for their initial functions,” the business claimed in a report shared with The Hacker News. “On attaining AWS Console entry, they conduct their operations right through the web browser.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Attack chains mounted by GUI-vil entail getting initial access by weaponizing AWS keys in publicly uncovered supply code repositories on GitHub or scanning for GitLab circumstances that are vulnerable to distant code execution flaws (e.g., CVE-2021-22205).
A thriving ingress is adopted by privilege escalation and an internal reconnaissance to critique all out there S3 buckets and ascertain the services that are available via the AWS web console.
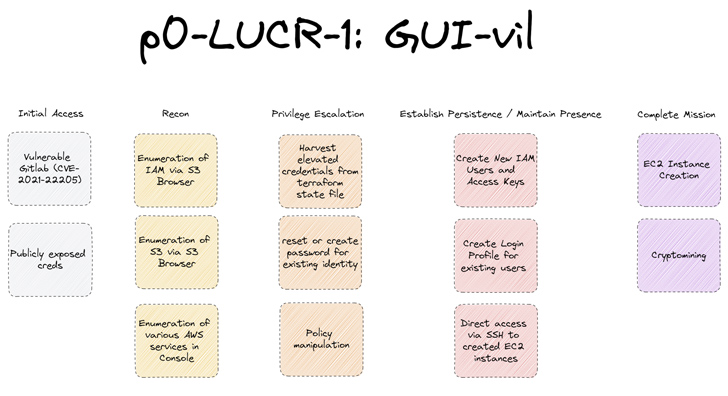
A notable facet of the risk actor’s modus operandi is its try to blend in and persist within the victim natural environment by developing new people that conform to the exact same naming convention and ultimately satisfy its targets.
“GUI-vil will also generate obtain keys for the new identities they are generating so they can continue usage of S3 Browser with these new consumers,” the corporation explained.
Upcoming WEBINARZero Belief + Deception: Master How to Outsmart Attackers!
Find out how Deception can detect innovative threats, cease lateral movement, and greatly enhance your Zero Rely on technique. Sign up for our insightful webinar!
Help save My Seat!
Alternatively, the team has also been noticed generating login profiles for present consumers that do not have them so as to allow obtain to the AWS console without having elevating purple flags.
GUI-vil’s hyperlinks to Indonesia stem from the fact that the supply IP addresses involved with the pursuits are connected to two Autonomous Program Quantities (ASNs) positioned in the Southeast Asian region.
“The group’s principal mission, monetarily driven, is to create EC2 scenarios to facilitate their crypto mining routines,” researchers said. “In numerous situations the profits they make from crypto mining are just a sliver of the cost the sufferer businesses have to shell out for running the EC2 situations.”
Found this post exciting? Abide by us on Twitter and LinkedIn to go through extra distinctive material we write-up.
Some pieces of this article are sourced from:
thehackernews.com


 China Issues Ban on US Chipmaker Products
China Issues Ban on US Chipmaker Products