About 34% of security vulnerabilities impacting industrial management systems (ICSs) that were being reported in the very first half of 2023 have no patch or remediation, registering a significant raise from 13% the preceding year.
In accordance to knowledge compiled by SynSaber, a overall of 670 ICS products flaws were being described via the U.S. Cybersecurity and Infrastructure Security Company (CISA) in the to start with 50 % of 2023, down from 681 reported during the to start with fifty percent of 2022.
Of the 670 CVEs, 88 are rated Critical, 349 are rated Substantial, 215 are rated Medium, and 18 are rated Lower in Severity. 227 of the flaws have no fixes in comparison to 88 in H1 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
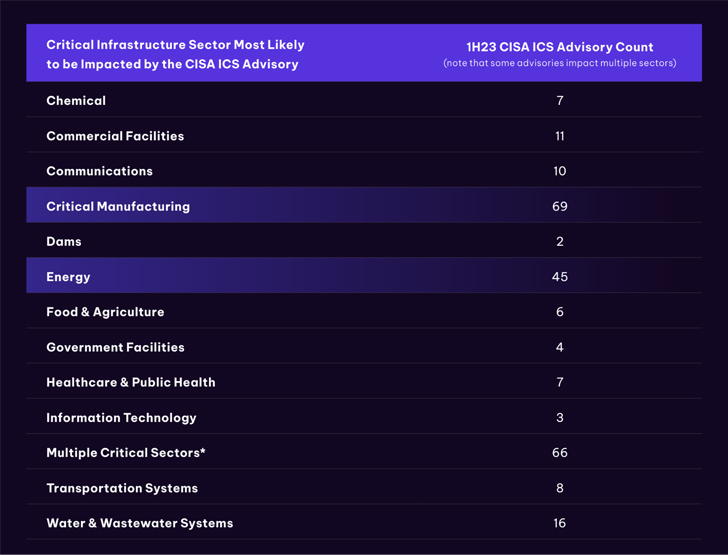
“Critical producing (37.3% of full described CVEs) and Power (24.3% of the whole claimed) sectors are the most most likely to be impacted,” the OT cybersecurity and asset checking firm explained in a report shared with The Hacker News.
Other popular business verticals incorporate h2o and wastewater units, professional services, communications, transportation, chemical, health care, meals and agriculture, and governing administration facilities.

Some of the other notable conclusions are as follows –
- Mitsubishi Electric powered (20.5%), Siemens (18.2%), and Rockwell Automation (15.9%) were being the most impacted sellers in the critical manufacturing sector
- Hitachi Power (39.5%), Advantech (10.5%), Delta Electronics, and Rockwell Automation (both 7.9%) had been the most impacted suppliers in the strength sector
- Siemens emerged as the leading entity manufacturing the most CVEs by way of the initially half of 2023, accounting for 41 ICS advisories
- Use right after cost-free, out-of-bounds go through, improper enter validation, out-of-bounds produce, and race problem have been the major 5 computer software weaknesses
What is actually additional, a the vast majority of CVE experiences (84.6%) originated from original machines suppliers (OEMs) and security suppliers in the United States, adopted by China, Israel, and Japan. Independent and educational research accounted for 9.4% and 3.9%, respectively.
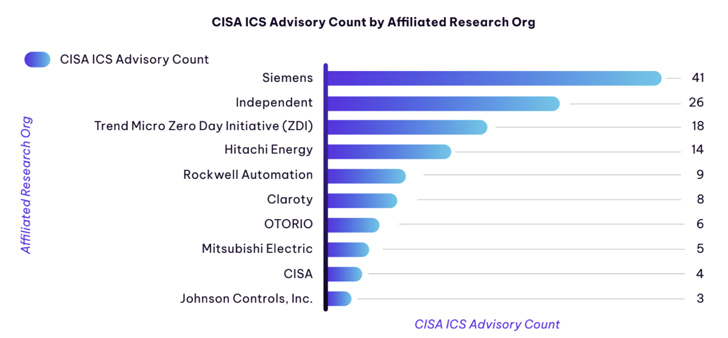
“Permanently-Working day vulnerabilities keep on being an issue – six CISA Advisories discovered for ICS vendor goods that reached conclusion of everyday living with ‘Critical’ severity vulnerabilities have no update, patch, components/ program/ firmware updates, or recognised workarounds,” the business pointed out.
SynSaber, nonetheless, observed that relying on CISA ICS advisories by yourself may well not be sufficient, and that companies require to keep an eye on several resources of facts to get a better thought of the flaws that may be relevant to their environments.

“Treatment need to be taken to have an understanding of vulnerabilities in the context of the environments in which they look,” it mentioned. “Since each and every OT atmosphere is special and reason-built, the chance of exploitation and influence that it may possibly have will differ enormously for each individual business.”
The results arrive as Nozomi Networks discovered a “substantial quantity of network scanning indications in drinking water treatment method services, cleartext password alerts across the creating components sector, software transfer exercise in industrial machinery, [and] OT protocol packet injection tries in oil and gas networks.”
The IoT cybersecurity firm mentioned it detected an common of 813 unique attacks day-to-day against its honeypots, with top rated attacker IP addresses emanating from China, the U.S., South Korea, Taiwan, and India.
Found this short article attention-grabbing? Comply with us on Twitter and LinkedIn to go through a lot more distinctive content material we article.
Some parts of this posting are sourced from:
thehackernews.com


 Top Industries Significantly Impacted by Illicit Telegram Networks
Top Industries Significantly Impacted by Illicit Telegram Networks