Cybersecurity scientists have learned critical vulnerabilities in industrial VPN implementations principally made use of to supply remote access to operational technology (OT) networks that could make it possible for hackers to overwrite information, execute destructive code, and compromise industrial manage units (ICS).
A new report released by industrial cybersecurity firm Claroty demonstrates multiple extreme vulnerabilities in organization-grade VPN installations, together with Secomea GateManager M2M Server, Moxa EDR-G902, and EDR-G903, and HMS Networks eWon’s eCatcher VPN customer.
These susceptible solutions are commonly applied in industry-based industries these as oil and fuel, h2o utilities, and electric utilities to remotely obtain, retain and keep track of ICS and discipline devices, like programmable logic controllers (PLCs) and input/output equipment.
According to Claroty researchers, effective exploitation of these vulnerabilities can give an unauthenticated attacker immediate entry to the ICS equipment and likely trigger some bodily destruction.
In Secomean’s GateManager, scientists uncovered numerous security flaws, like a critical vulnerability (CVE-2020-14500) that enables overwriting arbitrary info, executing arbitrary code, or causing a DoS affliction, running commands as root, and obtaining consumer passwords owing to the use of a weak hash form.
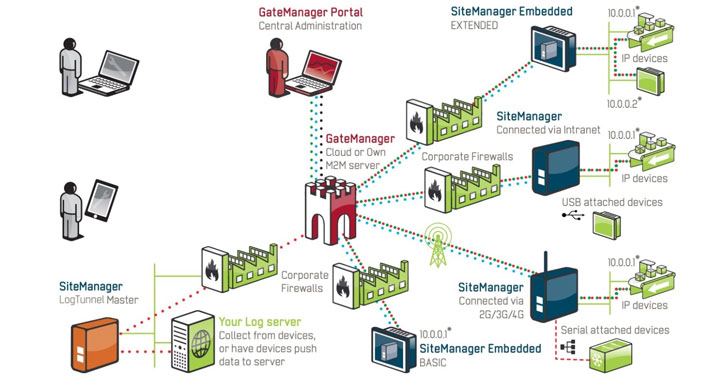
GateManager is a broadly utilised ICS remote entry server deployed around the world as a cloud-based SaaS alternative that allows people to link to the internal network from the internet through an encrypted tunnel whilst staying away from server setups.
The critical flaw, identified as CVE-2020-14500, influences the GateManager ingredient, the major routing occasion in the Secomea remote access solution. The flaw occurs due to poor dealing with of some of the HTTP ask for headers presented by the customer.
This flaw can be exploited remotely and without the need of necessitating any authentication to obtain remote code execution, which could outcome in gaining full access to a customer’s inner network, along with the skill to decrypt all website traffic that passes by the VPN.
In Moxa EDR-G902 and EDR-G903 industrial VPN servers, researchers learned a stack-dependent buffer overflow bug (CVE-2020-14511) in the program web server that can be induced just by sending a specially crafted HTTP request, sooner or later allowing for attackers to have out remote code execution without having the need for any credentials.
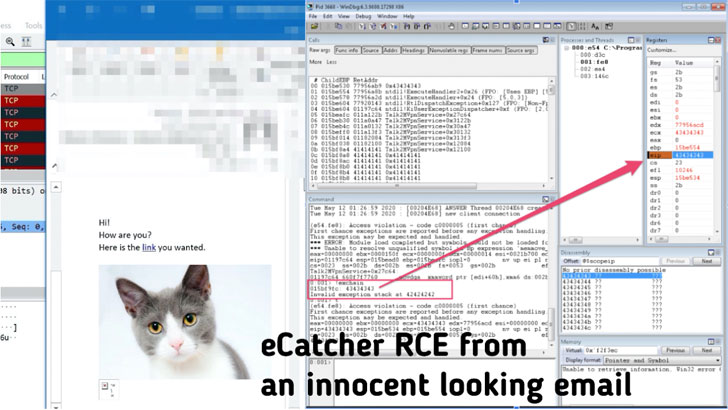
Claroty scientists also analyzed HMS Networks’ eCatcher, a proprietary VPN customer that connects to the firm’s eWon VPN system, and identified that the product is vulnerable to a critical stack-centered buffer overflow (CVE-2020-14498) that can be exploited to reach remote code execution.
All an attacker requires to do is tricking victims into browsing a destructive web site or opening a destructive email made up of a specifically crafted HTML ingredient that triggers the flaw in eCatcher, ultimately making it possible for attackers to acquire entire manage of the focused device.
All a few sellers ended up notified of the vulnerabilities and responded quickly to launch security fixes that patch their products’ loopholes.
Secomea customers are advised to update their items to the freshly produced GateManager variations 9.2c / 9.2i, Moxa users have to have to update EDR-G902/3 to model v5.5 by applying firmware updates accessible for the EDR-G902 sequence and EDR-G903 series, and HMS Networks people are suggested to update eCatcher to Variation 6.5.5 or later.
Observed this write-up attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to examine more exclusive information we write-up.

 Promo Information Breach Hits 14.6 Million Person Accounts
Promo Information Breach Hits 14.6 Million Person Accounts