The operators behind the now-defunct Inferno Drainer produced much more than 16,000 unique destructive domains more than a span of a single year among 2022 and 2023.
The plan “leveraged high-excellent phishing internet pages to entice unsuspecting users into connecting their cryptocurrency wallets with the attackers’ infrastructure that spoofed Web3 protocols to trick victims into authorizing transactions,” Singapore-headquartered Team-IB stated in a report shared with The Hacker News.


Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Inferno Drainer, which was lively from November 2022 to November 2023, is approximated to have reaped in excess of $87 million in illicit revenue by scamming more than 137,000 victims.
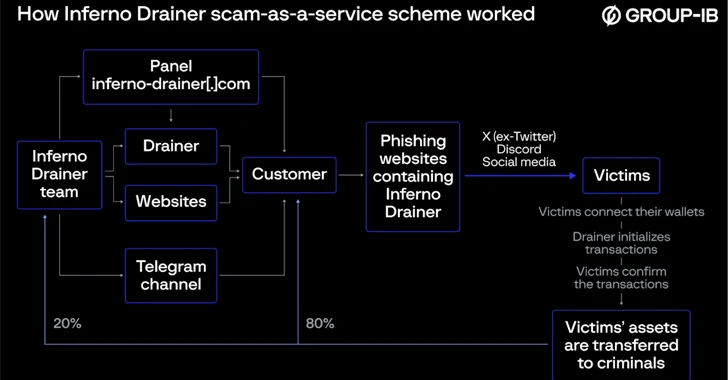
The malware is section of a broader established of identical offerings that are offered to affiliates under the fraud-as-a-services (or drainer-as-a-service) design in trade for a 20% slash of their earnings.
What is much more, consumers of Inferno Drainer could either upload the malware to their personal phishing web-sites, or make use of the developer’s provider for developing and hosting phishing internet sites, possibly at no more price or charging 30% of the stolen property in some circumstances.
According to Team-IB, the activity spoofed upwards of 100 cryptocurrency brand names by using specially crafted web pages that had been hosted on above 16,000 unique domains.

Further more investigation of 500 of these domains has revealed that the JavaScript-primarily based drainer was hosted initially on a GitHub repository (kuzdaz.github[.]io/seaport/seaport.js) ahead of incorporating them straight on the sites. The consumer “kuzdaz” at present does not exist.
In a equivalent trend, an additional set of 350 web sites bundled a JavaScript file, “coinbase-wallet-sdk.js,” on a diverse GitHub repository, “kasrlorcian.github[.]io.”
These web sites had been then propagated on web sites like Discord and X (previously Twitter), attractive opportunity victims into clicking them below the guise of supplying cost-free tokens (aka airdrops) and connecting their wallets, at which issue their belongings are drained after the transactions are accepted.

In working with the names seaport.js, coinbase.js and wallet-connect.js, the notion was to masquerade as well-liked Web3 protocols like Seaport, WalletConnect, and Coinbase to full the unauthorized transactions. The earliest web site that contains a person of these scripts dates back to Could 15, 2023.
“Another regular element of phishing web sites belonging to Inferno Drainer was that buyers are not able to open up web page source code by working with hotkeys or suitable-clicking on the mouse,” Team-IB analyst Viacheslav Shevchenko reported. “This implies that the criminals tried to hide their scripts and unlawful exercise from their victims.”
It is worth noting that Google-owned Mandiant’s X account was compromised previously this thirty day period to distribute links to a phishing website page hosting a cryptocurrency drainer tracked as CLINKSINK.
“Inferno Drainer may possibly have ceased its activity, but its prominence all through 2023 highlights the severe threats to cryptocurrency holders as drainers continue on to build more,” Andrey Kolmakov, head of Team-IB’s High-Tech Criminal offense Investigation Section, mentioned.
Uncovered this post appealing? Follow us on Twitter and LinkedIn to examine far more exclusive material we post.
Some parts of this short article are sourced from:
thehackernews.com

 Hackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer
Hackers Weaponize Windows Flaw to Deploy Crypto-Siphoning Phemedrone Stealer