XWorm is a somewhat new consultant of the remote accessibility trojan cohort that has already acquired its spot among the most persistent threats throughout the world.
Considering the fact that 2022, when it was first observed by researchers, it has undergone a quantity of significant updates that have drastically increased its features and solidified its being electricity.
The analyst team at ANY.Operate came across the newest version of the malware and could not refuse the possibility of using it apart to study XWorm mechanics configurations. Listed here is how they did it and what they located.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The XWorm sample’s source
The sample in query was learned in ANY. RUN’s databases of malware, a repository containing in depth evaluation stories on all files and inbound links that have been uploaded by buyers of the sandbox in general public manner.
A fast look at the benefits of the assessment uncovered that the sample was in the beginning dispersed through MediaFire, a file-hosting provider. The malware was packaged in a RAR archive and secured by a password.
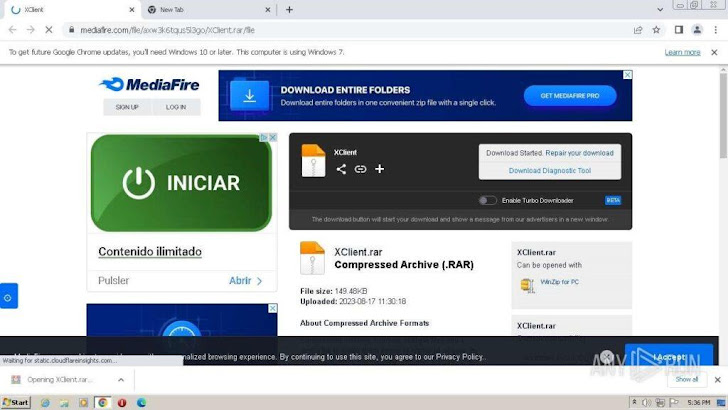 Figure 1: The MediaFire site that contains the archive obtain url.
Figure 1: The MediaFire site that contains the archive obtain url.
On execution, the menace was instantly detected by Suricata policies and recognized as XWorm.
 Figure 2: XWorm’s website traffic marked as malicious by the sandbox.
Figure 2: XWorm’s website traffic marked as malicious by the sandbox.
XWorm’s Practices, Tactics, and Treatments (TTPs)
The sandbox report highlighted many procedures used by the sample:
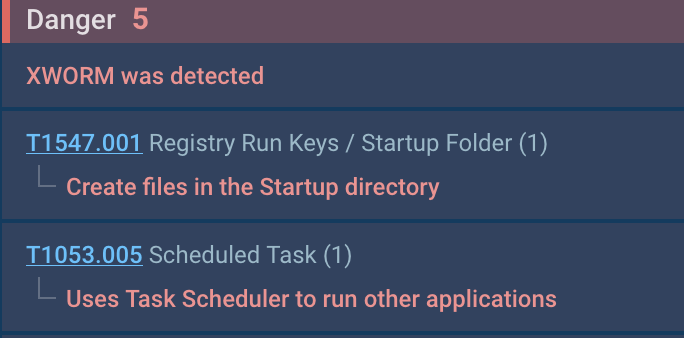 Determine 3: XWorm’s pursuits on the contaminated system.
Determine 3: XWorm’s pursuits on the contaminated system.
MITRE T1547.001: XWorm included its shortcut to the Startup directory.
MITRE T1053.005: It applied the activity scheduler to restart alone with elevated privileges, as indicated by the “/RL Greatest” parameter.
MITRE T1074.001: The application was mounted in the Public directory.
MITRE T1571: The malware experimented with to join to a distant server, but no response was gained.
XWorm’s unsuccessful try to evade sandbox examination
Given that the preliminary assessment report was numerous days outdated, the group made a decision to operate the sample via the sandbox at the time again to check for new activities.
However, immediately after launch, the malware crashed nearly straight away. A brief investigation designed it obvious that the sample now queried a distinctive service to identify if it was operating in a virtual sandbox.
Primarily, XWorm developers implemented an evasion method, which induced the destructive software package to shut down as quickly as it sensed a virtualized natural environment.
To overcome this, the group enabled Household Proxy in the sandbox configurations. This attribute replaces the virtual machine’s datacenter IP deal with with a person from an genuine ISP, earning the malware believe it is running on a actual user’s device.
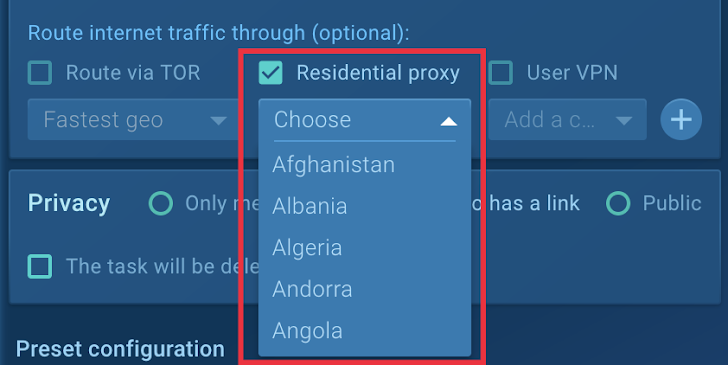 Determine 4: Household Proxy supplies IP addresses from several
Determine 4: Household Proxy supplies IP addresses from several
Just after rerunning the sample with Household Proxy enabled, XWorm was effectively executed and started its action.
Malware AnalysisAnalyze This Sample and A lot more with ANY.Operate
Sign up and get Prompt access to assess this sample, and any other, on ANY.Run. Don’t miss out on out on the supreme resource to realize and beat threats.
Develop Absolutely free Account
On prime of that, with the assist of the MITM proxy element, it was doable to extract the facts transmitted by XWorm to Telegram (MITRE T1102). The facts included: the malware’s variation (XWorm V3.1), the machine’s username, the OS model, and most likely the victim’s hash.
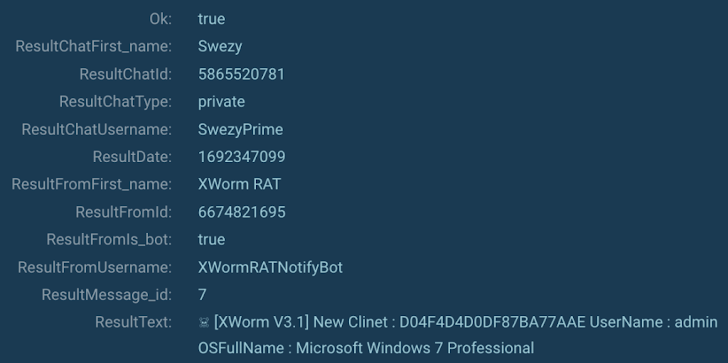 Figure 5: XWorm gathered technique details (MITRE T1082).
Figure 5: XWorm gathered technique details (MITRE T1082).
Static investigation of the new XWorm variant
Immediately after collecting all the crucial information and facts provided by the sandbox, the analysts commenced the static examination stage of their investigate. The to start with action was to load the sample into Detect it Effortless (DIE), an field typical for first malware evaluation. The software rapidly decided that it was a .NET variation of XWorm.
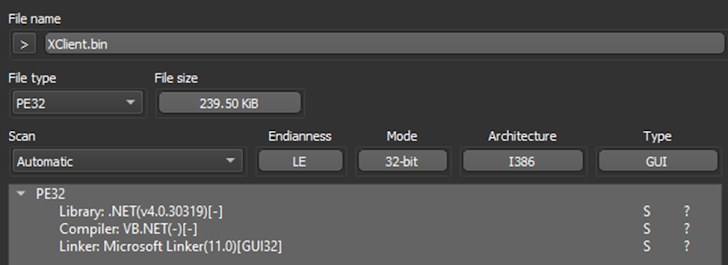 Figure 6: DIE provided an insight into the malware’s compiler.
Figure 6: DIE provided an insight into the malware’s compiler.
From there, the only sensible phase for the crew was to open the file in dnSpy, a .NET debugger, which promptly disclosed that the binary was issue to weighty obfuscation. However, DIE unsuccessful to understand the packer even using Heuristic scanning.
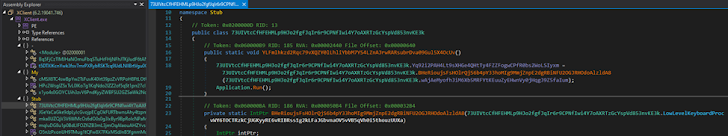 Figure 7: The XWorm’s code turned out to be obfuscated (MITRE T1027).
Figure 7: The XWorm’s code turned out to be obfuscated (MITRE T1027).
Employing de4dot, a .NET deobfuscator and unpacker, also did not have any impact.
Extra of XWorm’s evasion and persistence approaches
More investigation of the destructive binary permitted the staff to uncover added pieces of the puzzle. Exclusively, a range of added mechanics utilized by the malware were being uncovered:
Virtualization detection: XWorm utilised the WMI question “Choose * from Gain32_ComputerSystem” to verify for VmWare or VirtualBox environments.
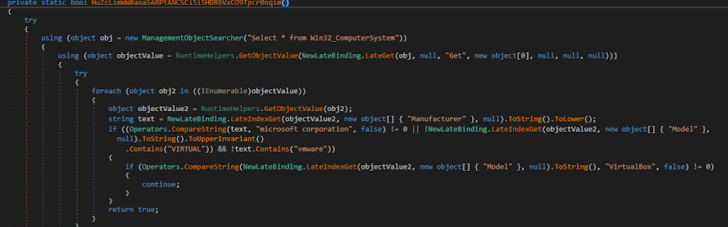 Determine 8: The malware exploited Windows Administration Instrumentation (MITRE T1047).
Determine 8: The malware exploited Windows Administration Instrumentation (MITRE T1047).
Debugger detection: It also ran the CheckRemoteDebuggerPresent API function to see if it was remaining debugged.
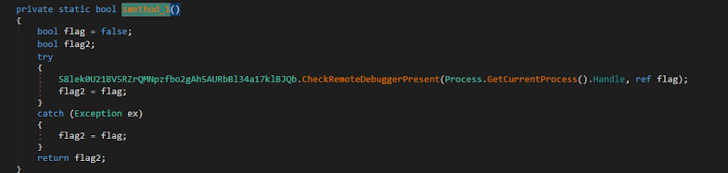 Determine 9: Xworm attempted to evade debugger analysis.
Determine 9: Xworm attempted to evade debugger analysis.
Sandboxie detection: The binary scanned the process to see if the SbieDll.dll library was loaded.
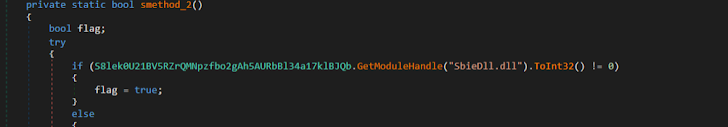 Figure 10: SbieDll.dll is linked with Sandboxie, a sandbox-based isolation application.
Figure 10: SbieDll.dll is linked with Sandboxie, a sandbox-based isolation application.
Datacenter IP test: Xworm queried the equipment to identify if it was hosted in a details center.
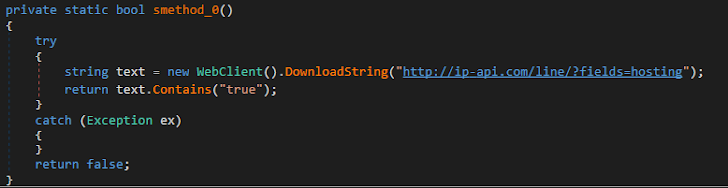 Determine 11: The malware’s IP scanning describes the purpose guiding its preliminary crash.
Determine 11: The malware’s IP scanning describes the purpose guiding its preliminary crash.
Persistence: XWorm utilized the registry and the endeavor scheduler to establish a persistent existence on the technique.
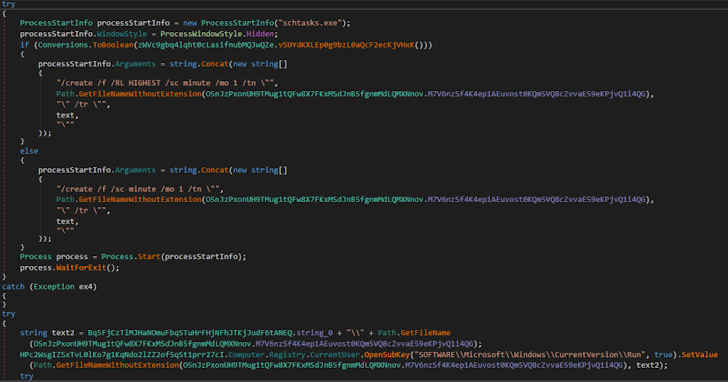 Determine 12: The code exposed the malware’s means to modify the registry.
Determine 12: The code exposed the malware’s means to modify the registry.
Extraction of XWorm’s configuration
Subsequent, the analysts discovered a constructor that looked like a block made up of configurations. They utilised a purpose to reassign some of its fields. The malware 1st computed an MD5 hash from a worth in the presumed options section.
It then copied the attained benefit two times into a non permanent array, but because of to an off-by-a person mistake, the MD5 was not staying copied solely twice. The workforce used the acquired array as a crucial to decrypt the incoming base64 strings applying AES in ECB manner.
They also identified that the field utilised was a mutex. The entire process is explained in depth in ANY.RUN’s web site write-up “XWorm: Technical Evaluation of a New Malware Model.”
XWorm’s configuration
The total configuration of XWorm’s new variant is as follows:
Host
6[.]tcp.eu.ngrok[.]io
Port
13394
AES key
Slaves!-.!2Swezy999!(xxx
Splitter
Xwormmm
Rest time
3
USB drop file
USB.exe
Mutex
Lz8qftMH08V7f1rq
Log file
%temp%\Log.tmp
Telegram token
6674821695:AAExQsr6_hmXk6hz7CN4kMSi9cs9y86daYM
Telegram chat id
5865520781
Summary
Acquiring configurations of the most up-to-date malware is critical but time-consuming. To make it far more successful, you can operate your samples as a result of the ANY.Run sandbox to entry the essential information and facts in seconds.
Check it oneself making use of the XWorm sample. As well as, ANY.Operate gives a 14-working day cost-free trial of its leading plan to security groups to assistance them test the capabilities of the service.
Observed this article attention-grabbing? Follow us on Twitter and LinkedIn to browse more special content material we submit.
Some areas of this article are sourced from:
thehackernews.com


 Earth Lusca’s New SprySOCKS Linux Backdoor Targets Government Entities
Earth Lusca’s New SprySOCKS Linux Backdoor Targets Government Entities