A security flaw impacting the Lighttpd web server made use of in baseboard administration controllers (BMCs) has remained unpatched by gadget suppliers like Intel and Lenovo, new findings from Binarly reveal.
Even though the primary shortcoming was discovered and patched by the Lighttpd maintainers way back in August 2018 with model 1.4.51, the absence of a CVE identifier or an advisory intended that it was forgotten by builders of AMI MegaRAC BMC, in the end ending up in solutions produced by Intel and Lenovo.
Lighttpd (pronounced “Lighty”) is an open-source higher-general performance web server application created for pace, security, and adaptability, although optimized for significant-efficiency environments with out consuming a ton of technique assets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The silent fix for Lighttpd fears an out-of-bounds study vulnerability that could be exploited to exfiltrate sensitive details, these kinds of as procedure memory addresses, thereby letting menace actors to bypass very important security mechanisms like address house format randomization (ASLR).

“The absence of prompt and significant data about security fixes prevents suitable dealing with of these fixes down the two the firmware and software program source chains,” the firmware security enterprise mentioned.
The flaws are explained under –
- Out-of-bounds examine in Lighttpd 1.4.45 employed in Intel M70KLP collection firmware
- Out-of-bounds study in Lighttpd 1.4.35 employed in Lenovo BMC firmware
- Out-of-bounds go through in Lighttpd ahead of 1.4.51
Intel and Lenovo have opted not to tackle the issue as the merchandise incorporating the inclined version of Lighttpd have strike end-of-everyday living (EoL) position and are no longer suitable for security updates, successfully turning it into a endlessly-day bug.
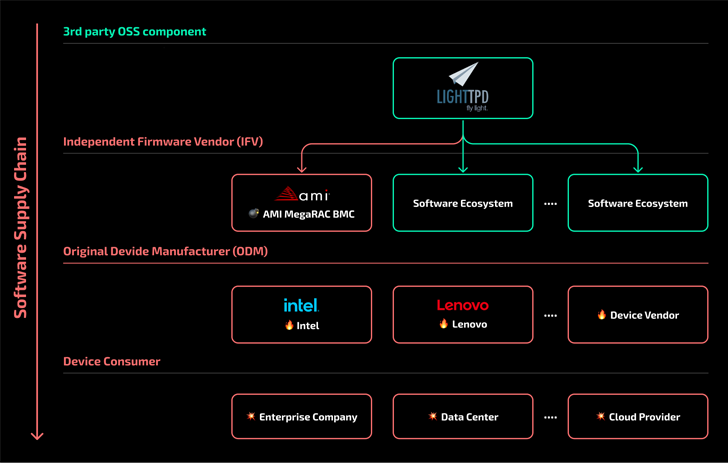
The disclosure highlights how the presence of outdated 3rd-party elements in the most up-to-date model of firmware can traverse the source chain and pose unintended security risks for finish consumers.
“This is however a further vulnerability that will remain unfixed endlessly in some products and solutions and will present superior-effects risk to the business for a really very long time,” Binarly included.
Found this post interesting? Stick to us on Twitter and LinkedIn to read through far more special articles we write-up.
Some components of this posting are sourced from:
thehackernews.com

 AI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead
AI Copilot: Launching Innovation Rockets, But Beware of the Darkness Ahead