The threat actor tracked as TA866 has resurfaced soon after a nine-thirty day period hiatus with a new massive-volume phishing marketing campaign to deliver acknowledged malware households this sort of as WasabiSeed and Screenshotter.
The campaign, noticed before this month and blocked by Proofpoint on January 11, 2024, concerned sending hundreds of bill-themed emails focusing on North America bearing decoy PDF documents.
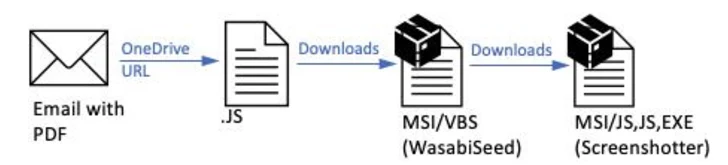
“The PDFs contained OneDrive URLs that, if clicked, initiated a multi-stage an infection chain at some point main to the malware payload, a variant of the WasabiSeed and Screenshotter customized toolset,” the organization security company said.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
TA866 was initial documented by the corporation in February 2023, attributing it to a marketing campaign named Screentime that distributed WasabiSeed, a Visual Basic script dropper which is utilised to download Screenshotter, which is capable of having screenshots of the victim’s desktop at typical intervals of time and exfiltrating that information to an actor-controlled domain.
There is proof to propose that the organized actor could be fiscally motivated owing to the reality that Screenshotter acts as a recon tool to identify superior-benefit targets for publish-exploitation, and deploy an AutoHotKey (AHK)-based mostly bot to eventually drop the Rhadamanthys data stealer.

Subsequent conclusions from Slovak cybersecurity organization ESET in June 2023 unearthed overlaps concerning Screentime and another intrusion established dubbed Asylum Ambuscade, a crimeware group energetic due to the fact at least 2020 that also engages in cyber espionage operations.
The hottest attack chain remains almost unchanged preserve for the change from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive connection, with the marketing campaign relying on a spam service delivered by TA571 to distribute the booby-trapped PDFs.
“TA571 is a spam distributor, and this actor sends superior volume spam email strategies to provide and install a selection of malware for their cybercriminal buyers,” Proofpoint researcher Axel F mentioned.
This involves AsyncRAT, NetSupport RAT, IcedID, PikaBot, QakBot (aka Qbot), and DarkGate, the very last of which lets attackers to carry out a variety of commands these types of as data theft, cryptocurrency mining, and execution of arbitrary plans.
“Darkgate initially appeared in 2017 and is offered only to a tiny variety of attack groups in the sort of Malware-as-a-Company by means of underground discussion boards,” South Korean cybersecurity business S2W claimed in an investigation of the malware this week.
“DarkGate proceeds to update it by introducing functions and repairing bugs centered on analysis final results from security scientists and sellers,” highlighting ongoing initiatives created by adversaries to put into practice anti-analysis techniques to bypass detection.
News of TA866’s resurgence comes as Cofense uncovered that delivery-connected phishing e-mail primarily single out the producing sector to propagate malware like Agent Tesla and Formbook.
“Delivery-themed e-mail boost in the course of the holiday seasons, albeit only slightly,” Cofense security researcher Nathaniel Raymond claimed.

“For the most portion, the yearly trends recommend that these email messages abide by a specific pattern in the course of the yr with different levels of volumes, with the most considerable volumes getting in June, October, and November.”
The growth also follows the discovery of a novel evasion tactic that leverages the caching system of security solutions to get all around them by incorporating a Phone To Motion (CTA) URL that points to a trustworthy site in the phishing concept sent to the specific personal.

“Their method entails caching a seemingly benign model of the attack vector and subsequently altering it to supply a malicious payload,” Trellix stated, stating these types of attacks have disproportionately targeted economical companies, producing, retail, and insurance policy verticals in Italy, the U.S., France, Australia, and India.
When this kind of a URL receives scanned by the security engine, it can be marked as safe and sound, and the verdict is stored in its cache for a established time. This also indicates that if the URL is encountered once more in just that time period, the URL is not reprocessed, and alternatively, the cached end result is served.
Trellix pointed out that attackers are taking edge of this quirk by ready right until the security distributors course of action the CTA URL and cache their verdict, and then altering the website link to redirect to the meant phishing web site.
“With the verdict currently being benign, the email effortlessly lands in the victim’s inbox,” security scientists Sushant Kumar Arya, Daksh Kapur, and Rohan Shah reported. “Now, need to the unsuspecting recipient decide to open up the email and click on on the website link/button within just the CTA URL, they would be redirected to the malicious site.”
Observed this post exciting? Observe us on Twitter and LinkedIn to read through additional exclusive information we publish.
Some components of this report are sourced from:
thehackernews.com


 Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software
Experts Warn of macOS Backdoor Hidden in Pirated Versions of Popular Software